When GRC and Heatmaps Do More Harm Than Good to Cyber Risk Management
Building the Language of Cyber Risk
Governance, Risk, and Compliance (GRC) has long been the cornerstone of enterprise risk management. On paper, it ensures alignment between strategy, control, and accountability. In practice, however, traditional GRC, along with its colorful cousin, the risk heatmap, is quietly holding cybersecurity back.
We must start acknowledging a hard truth: cyber risk is not static. It is continuous, dynamic, and shared. Yet most GRC programs treat it as if it were predictable, something that can be reviewed once a year, discussed in a steering committee, and color-coded into a green, yellow, or red box.
That might work for traditional business risks such as supply shortages, financial exposure, or compliance audits, which move in predictable cycles and can be revisited every six or twelve months. But in cybersecurity, risk mutates every hour, every minute. New exposures emerge with every line of code, every new SaaS connection, every third-party API, and every identity created in the cloud. Still, many organizations cling to the illusion that a yearly GRC review equals control.
We are using tools designed for stability, annual audits, static heatmaps, compliance checklists, to manage something that is inherently unstable. That mismatch is not a small operational detail; it is the core reason why so many security programs look mature on paper and yet collapse under real pressure.
The Wrong Tools for the Problem
We are trying to measure turbulence with a ruler, and we are mistaking precision for understanding. To manage a living, breathing, real-time phenomenon with static tools such as checklists, heatmaps, and quarterly audits is like trying to navigate a storm with last week’s weather report. It creates a comforting illusion of structure, but no real sense of direction.
Traditional GRC frameworks were built for a world defined by stability, for industrial systems, financial processes, and regulatory cycles where risk evolves slowly, predictably, and within human timeframes. They were designed for an environment in which change was measurable, controls were permanent, and cause-and-effect relationships could be traced with linear logic. But cyber risk does not move in quarters or years; it moves in seconds.
It is like using a thermometer to measure the speed of wind, or a compass to read the tide. The instrument itself is not wrong, but it was never meant for this kind of motion. The speed of change in digital environments invalidates any model that assumes constancy, and yet we continue to depend on frameworks that reward documentation over adaptation and reporting over response.
A financial controller can measure exposure on a quarterly basis because the data they rely on, revenue, liquidity, assets, and obligations, behaves according to economic rhythms that rarely change overnight. A CISO, in contrast, operates in machine time, where exposure is created and destroyed in seconds, and where visibility is ephemeral by design. By the time a “risk register” is updated, the architecture has shifted, a vulnerability has been disclosed, or an adversarial AI model has already learned to exploit it.
Cyber risk does not fit neatly inside a spreadsheet, just as weather does not fit inside a calendar. When we use GRC heatmaps to manage cyber risk, we are not managing the risk itself but our perception of it. We debate colors while adversaries exploit code, and we hold steering committees while attackers hold sessions of their own, in real time, and with far better intelligence.
The result is a growing disconnect between the speed at which risk evolves and the speed at which governance reacts. We are not failing because we lack frameworks, but because we keep applying the wrong instruments to the right problems. The question is no longer whether GRC is necessary, but whether it is sufficient for a threat landscape and a business that refuses to stay still.
Making Decisions with the Wrong Tool
If the essence of cyber risk management is to make good decisions in the face of uncertainty, then our current governance models are profoundly unfit for purpose. GRC frameworks were designed to document control, not to enable choice. They were built to demonstrate compliance after the fact, not to guide judgment before impact. In that sense, we are trying to make strategic decisions with instruments that were never meant for decision-making, they are designed for evidence, not foresight.
A good decision in risk management is never judged by whether the event occurs, but by whether we were prepared to handle it if it did . It is about readiness, not prediction. Yet, the heatmaps and risk registers that dominate corporate cyber discussions give executives a false sense of precision — they replace probability with color, and impact with adjectives. We end up managing colors instead of consequences.
When you base governance on tools that simplify complexity instead of contextualizing it, you create a dangerous comfort zone where action feels optional. A green box suggests safety even when exposures are expanding silently across third-party ecosystems. A yellow square signals moderate concern, as if risk were a mood rather than a measurable condition. In reality, the underlying variables, exposure, likelihood, and business impact, shift continuously, but the map remains unchanged, like a photograph pretending to describe a moving storm.
Cyber risk management is not about producing dashboards that confirm we are compliant; it is about equipping leaders to make informed, defensible, and timely decisions when certainty is impossible. When you use GRC as your compass, you might feel oriented, but you are navigating with a tool built for audit, not for weather. You are measuring compliance when what you need is consequence.
In Umbrellas, Storms, and Cyber Risk, I used a simple image: carrying an umbrella on a cloudy day. You don’t take it because you know it will rain; you take it because you understand the cost of being unprepared if it does . That single decision, to act on uncertainty rather than wait for confirmation, captures the very soul of cyber risk management. The forecast is never certain, but the exposure is always real.
The tragedy of modern GRC is that it tries to make decisions by pretending uncertainty can be removed. But risk cannot be erased; it can only be managed. And management begins with judgment, with the courage to decide even when the data is incomplete, to prepare even when the sky still looks clear.
When we reduce governance to documentation, and risk to a color-coded matrix, we replace the art of decision-making with the comfort of record-keeping. Cyber risk management was never meant to be about eliminating uncertainty, but about giving it structure, transforming chaos into context, and context into choice.
When Frameworks Freeze and Cyber Risk Moves
The gap between how organizations govern cyber risk and how cyber risk actually behaves has never been wider. Even McKinsey recently noted that attackers now benefit from organizational indecision on cyber risk, including the prevailing lack of clarity about the danger and the failure to execute effective cyber controls. In other words, the adversary’s greatest ally is not speed or sophistication, but our own hesitation.
Indecision is the silent breach. It doesn’t show up in incident reports, yet it creates the conditions where every alert, every exposure, and every delayed control multiplies in consequence. And this indecision is not born from ignorance, but from complexity — from a governance model that still assumes we can pause to analyze before acting, that cyber risk can be understood in meetings and managed in minutes.
The NIST Cybersecurity Framework 2.0 makes this point unambiguously: “Cyber risks are expanding constantly, and managing those risks must be a continuous process. This is true regardless of whether an organization is just beginning to confront its cybersecurity challenges or whether it has been active for many years with a sophisticated, well-resourced cybersecurity team.”
The very institutions that created the language of control are now calling for continuity. Yet most enterprises still operate their GRC programs as if risk were episodic, a quarterly exercise, a yearly certification, a once-a-year heatmap review. When governance is static, decisions lag, and lag becomes exposure.
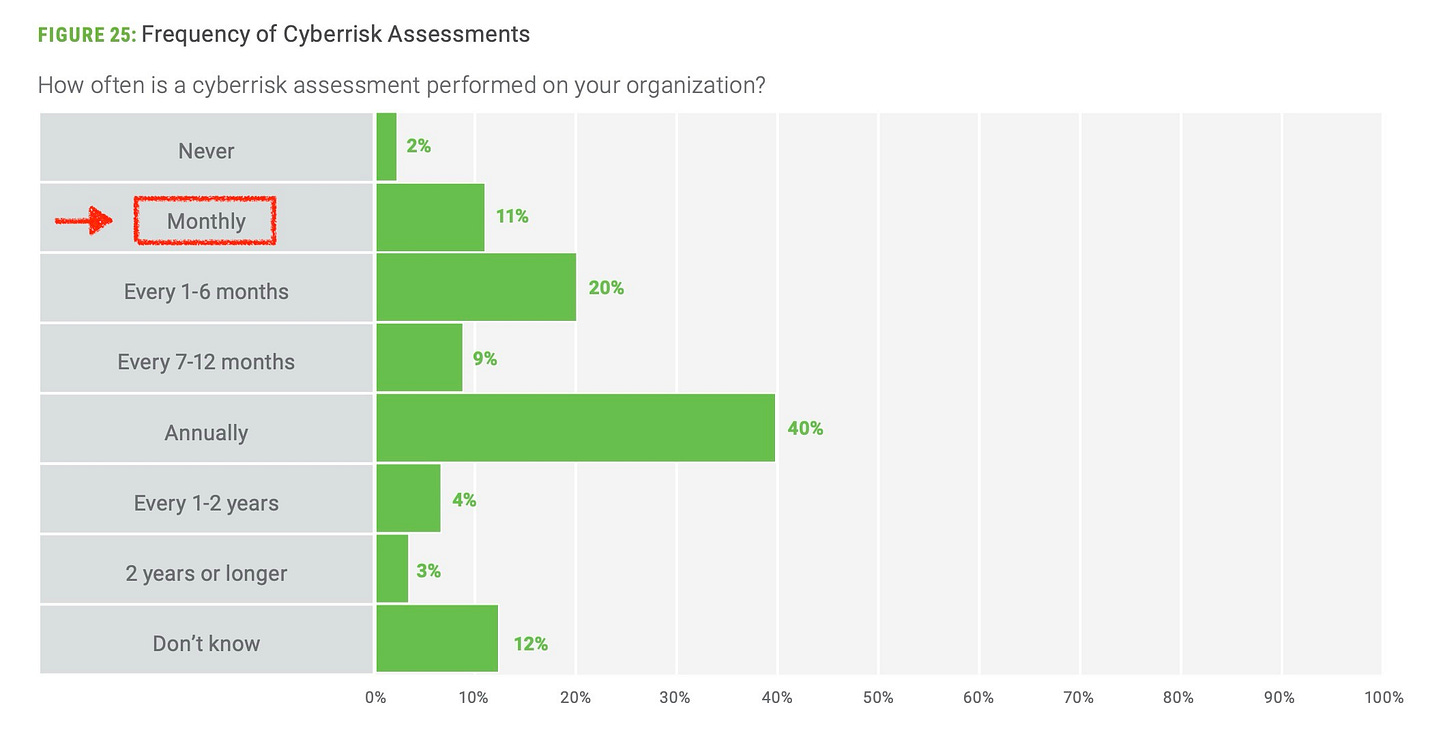
The ISACA State of Cybersecurity 2025 report confirms this disconnect. Every year, I go straight to two sections: the frequency of cyber risk assessments and the obstacles to conducting them. I always hope to see evolution, faster cycles, smarter processes, but I end up disappointed. More than sixty percent of organizations still perform cyber risk assessments on a yearly basis, while monthly remains the lowest frequency reported. It’s as if time itself has become optional. The most concerning part is that monthly is still considered the minimum cadence, when in reality it should be hourly or real-time. Cyber risk doesn’t wait for calendars, it changes with every line of code, every new connection, every new dependency.
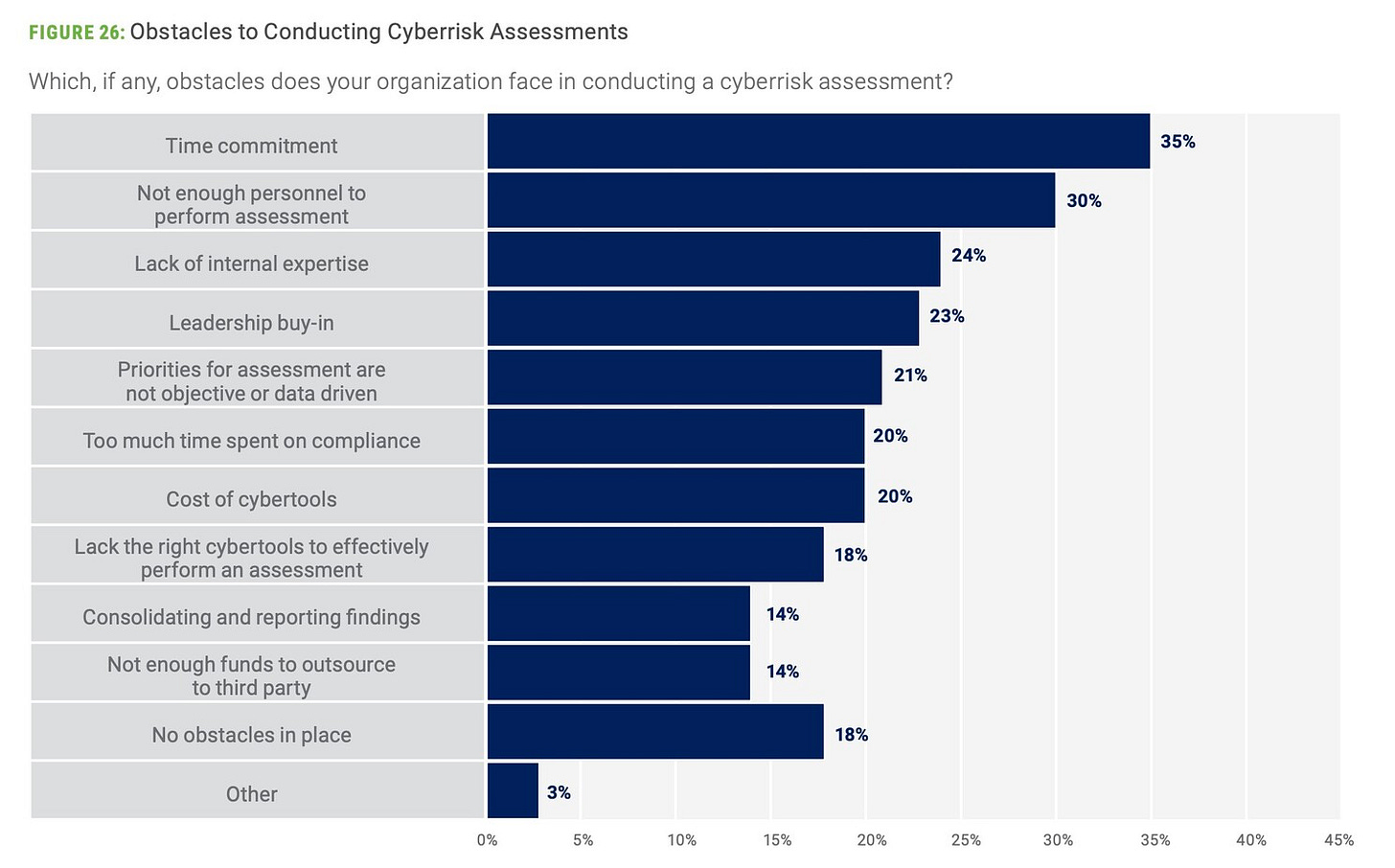
The most concerning part isn’t the cadence, it’s the cause. When asked about the main obstacles to conducting cyber risk assessments, the dominant answers remain manual processes and labor-intensive checklists . In 2025, the majority of enterprises still assess cyber risk by asking people questions, collecting spreadsheets, and debating color codes. These are not continuous systems, they are bureaucratic rituals masquerading as governance
If cyber risk mutates every hour, every minute, then governance must move at the same pace. Yet our frameworks are still optimized for recording, not responding. McKinsey calls it indecision; NIST calls it the need for continuity; ISACA exposes it as inertia. Together, they describe the same reality: we have the wrong tempo for the right problem.
The answer is not to abandon governance, but to operationalize it, to transform it from a retrospective control mechanism into a living decision engine. That is the essence of the continuous defense loop: governance that breathes, risk management that learns, and decisions that evolve at the speed of exposure.
The Rosetta Stone of Modern Cyber Security
The greatest vulnerability in modern cybersecurity is not technological, it is linguistic. Across the boardroom and the security operations center, we speak different dialects of the same problem. Executives talk in terms of revenue, exposure, and shareholder confidence. Security leaders talk in terms of CVEs, CVSS scores, and control frameworks. Somewhere between those two languages, meaning is lost, and with it, the ability to act decisively.
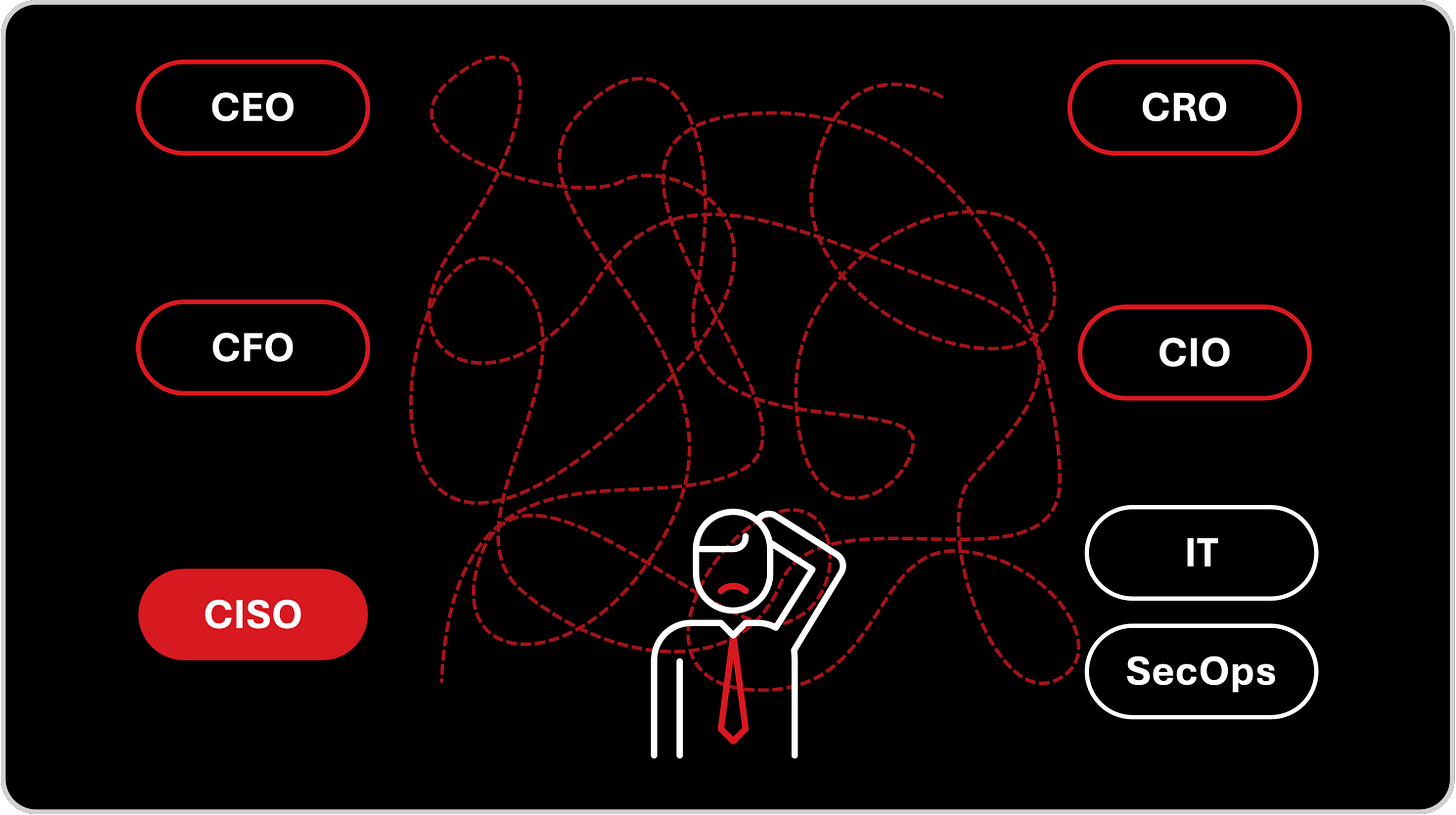
The result is disconnection. The CISO stands in the middle of a maze of conversations — one thread leading to the CFO, another to the CIO, the CRO, the CEO, each demanding clarity, each interpreting risk through a different lens. The conversation becomes tangled, delayed, and diluted. By the time alignment is reached, the threat landscape has already shifted.
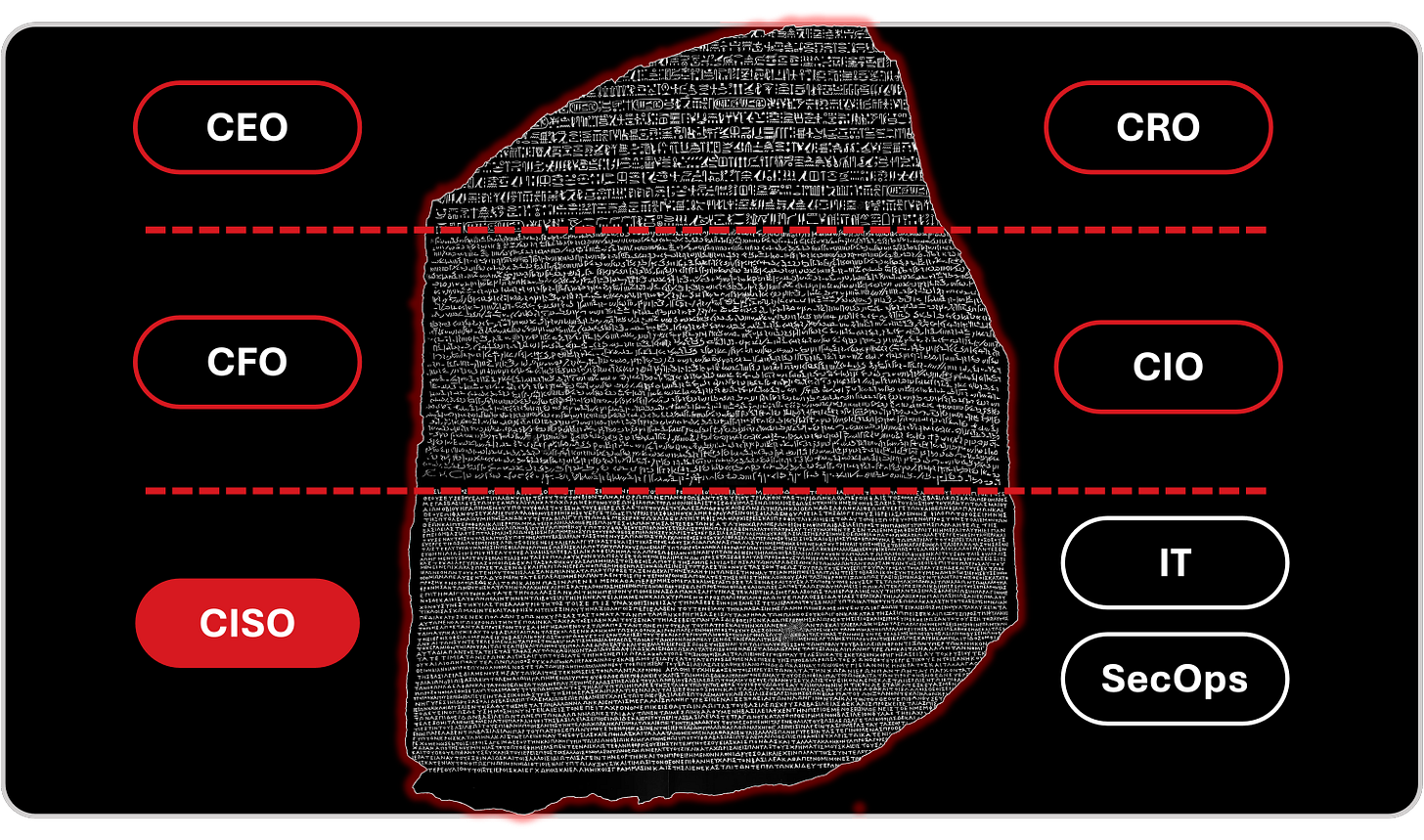
What we need is not another framework, but a Rosetta Stone for cyber security, a way to translate technical telemetry into financial and strategic consequence. Only when we can define, measure, and express cyber risk in the language of business will governance become a true mechanism of value protection rather than mere compliance.
In ancient times, the Rosetta Stone allowed scholars to decode languages that had long been silent. In our era, quantification is that stone, a bridge between systems of meaning. When a CISO can express exposure in terms of probability, impact, and financial loss, and when the CFO can understand those values as part of enterprise risk, dialogue becomes action. This is not just translation; it is transformation.
Heatmaps, GRC dashboards, and qualitative adjectives cannot fulfill that role because they reduce uncertainty to colors rather than converting it into context. A quantified cyber risk framework whether powered by FAIR, CREM CRQ, or any integrated model, becomes the grammar that unifies cybersecurity and business strategy.
Until we share this common language, governance will remain a negotiation between silos. But once that language is found, risk becomes readable, decisions become measurable, and cybersecurity finally becomes part of enterprise value creation, not just cost avoidance.
That is the real Rosetta Stone of our time: a shared language where security can speak in dollars, probability, and consequence, and where the board can finally listen in understanding, not translation.
Translating Questions into a Common Risk Language
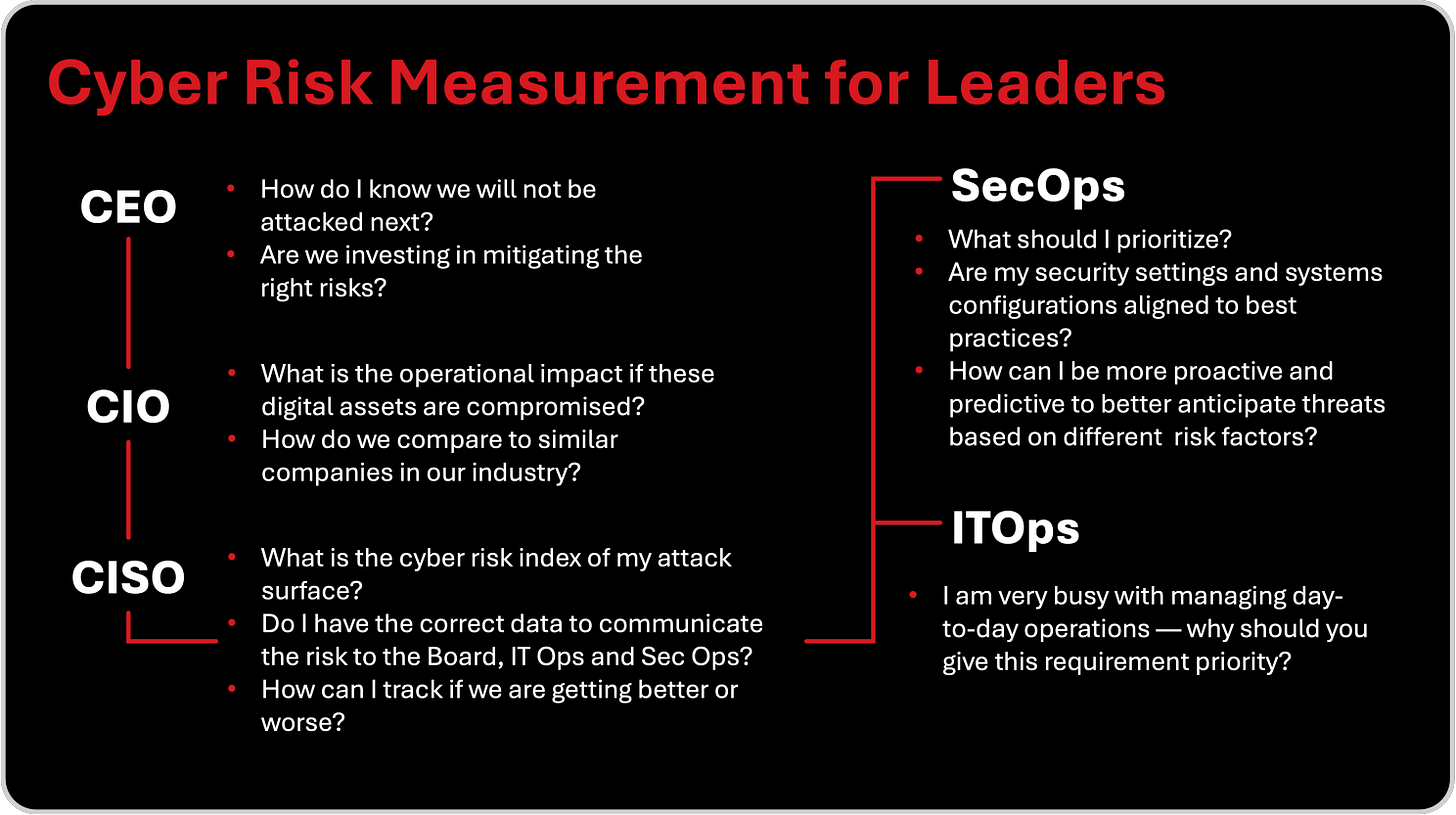
If you listen closely to how organizations talk about cyber risk, you will hear a Babel of intentions. The CEO speaks of protection and investment, asking whether the company is defending what matters most. The CFO listens through the lens of exposure and capital, trying to understand how much uncertainty translates into potential loss. The CIO focuses on continuity, comparing digital resilience to industry peers. The CISO struggles to convert telemetry into meaning, searching for data that can bridge the technical and the financial. Meanwhile, SecOps and IT teams live in the immediacy of operations, trying to prioritize the next alert, the next configuration drift, the next unpatched system.
Each of these perspectives is valid, yet none can see the full picture alone. What we call “cyber risk” is not one conversation but many, and each one uses a different unit of measurement. The CEO speaks in strategic outcomes, the CFO in probabilities and budgets, the CIO in systems and uptime, the CISO in vulnerabilities and indicators, and the operators in tickets and alerts. Between those vocabularies lies the silent cause of indecision: we cannot improve what we cannot describe in the same language.
This is why quantification becomes translation. Measuring cyber risk in financial terms, in dollars at risk, probability of loss, and impact on critical assets, creates a single syntax that all can understand. The CEO can make investment decisions, the CFO can assess exposure, the CIO can prioritize modernization, and the CISO can direct remediation, all within a shared frame of meaning.
In this model, the Cyber Risk Index (CRI) becomes more than a metric, it becomes the universal score that aligns business oversight with operational action. For the board and the C-suite, CRI expresses exposure in measurable terms that can be tracked over time. For ITOps and SecOps, that same score drives prioritization, helping teams decide which vulnerabilities, misconfigurations, or exposures matter most to the business right now. Instead of reacting to an endless queue of alerts, they act on a hierarchy of consequence.
When the CISO says, “Our current cyber risk exposure is $8 million across the next 90 days, primarily due to third-party dependencies,” every stakeholder understands both the gravity and the context. That sentence is not about technology; it is about consequence. It moves the conversation from What’s wrong? to What’s worth fixing first?
The diagram above captures this reality. Each role is asking the right questions, but they are asking them in isolation. A mature cyber risk management model, for CRI and CRQ, does not silence those questions; it synchronizes them. It gives every leader a way to see the same landscape through a different lens but on the same map.
Only when risk becomes measurable, comparable, and traceable across all these perspectives can cybersecurity evolve from a reactive function into a strategic discipline. And only then can governance finally deliver what it was meant to ensure, clarity, accountability, and coherence across the entire enterprise.
Building the Language of Cyber Risk
When I realized that the real challenge in cybersecurity was not technology but translation, I began designing frameworks that could help organizations move from confusion to coherence, from disconnected controls to a unified model of risk-informed decision-making. Every one of those frameworks was born from the same conviction: “What is not, defined cannot be measured. What is not measured cannot be improved. What is not improved always degrades.”
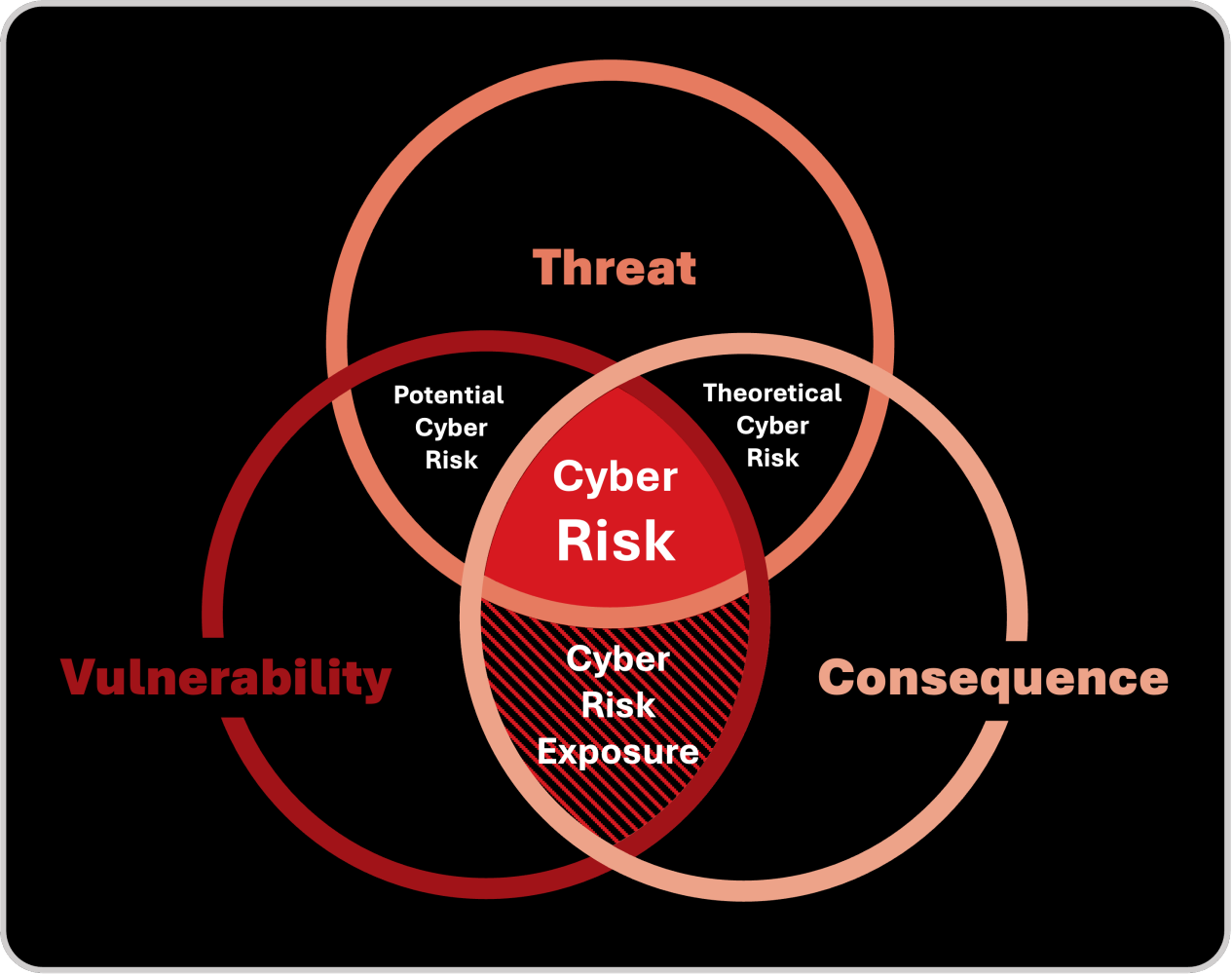
The first step was definition. Before metrics, before automation, before risk scoring, we needed to agree on what cyber risk actually means. To me, cyber risk exists at the intersection of threat, vulnerability, and consequence — the point where intent meets exposure, and exposure meets impact. That intersection, which I visualized in my early models, became the anchor for every framework that followed.
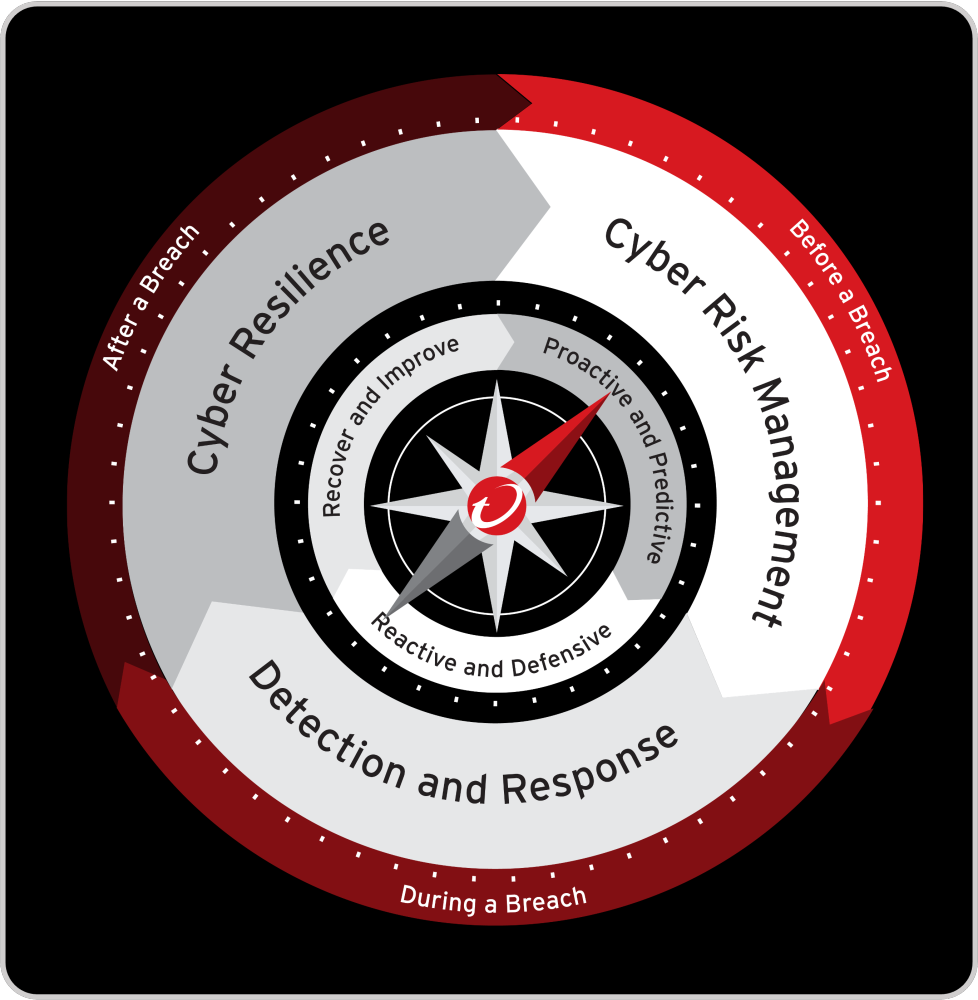
From that foundation, I developed the Cybersecurity Compass, a directional model to help leaders orient their cybersecurity strategy. It maps the full journey, before, during, and after a breach, connecting cyber risk management, detection and response, and resilience into a single, continuous system. The Compass was never meant to be static; it was a way to visualize cybersecurity as navigation rather than control, emphasizing direction over documentation.
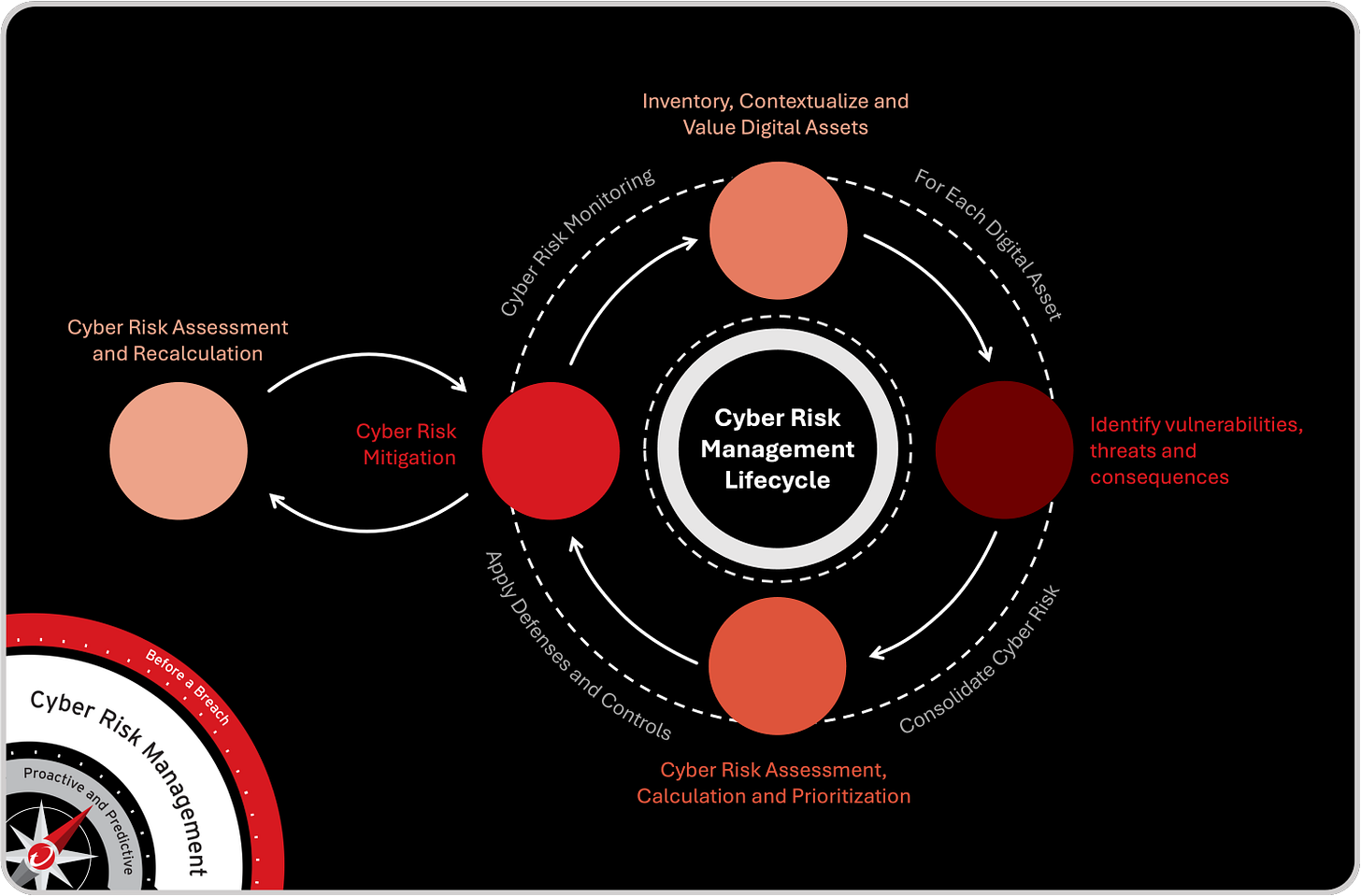
But direction alone was not enough. Organizations needed a way to operationalize that philosophy, to move from abstract governance to measurable execution. That’s where the Cyber Risk Management Lifecycle (CRML) was born. The CRML framework defined a repeatable process for managing cyber risk across people, process, and technology: inventorying assets, identifying threats and vulnerabilities, assessing and prioritizing risk, applying defenses and controls, and continuously monitoring and recalculating exposure. It turned governance from a retrospective checklist into an active cycle.
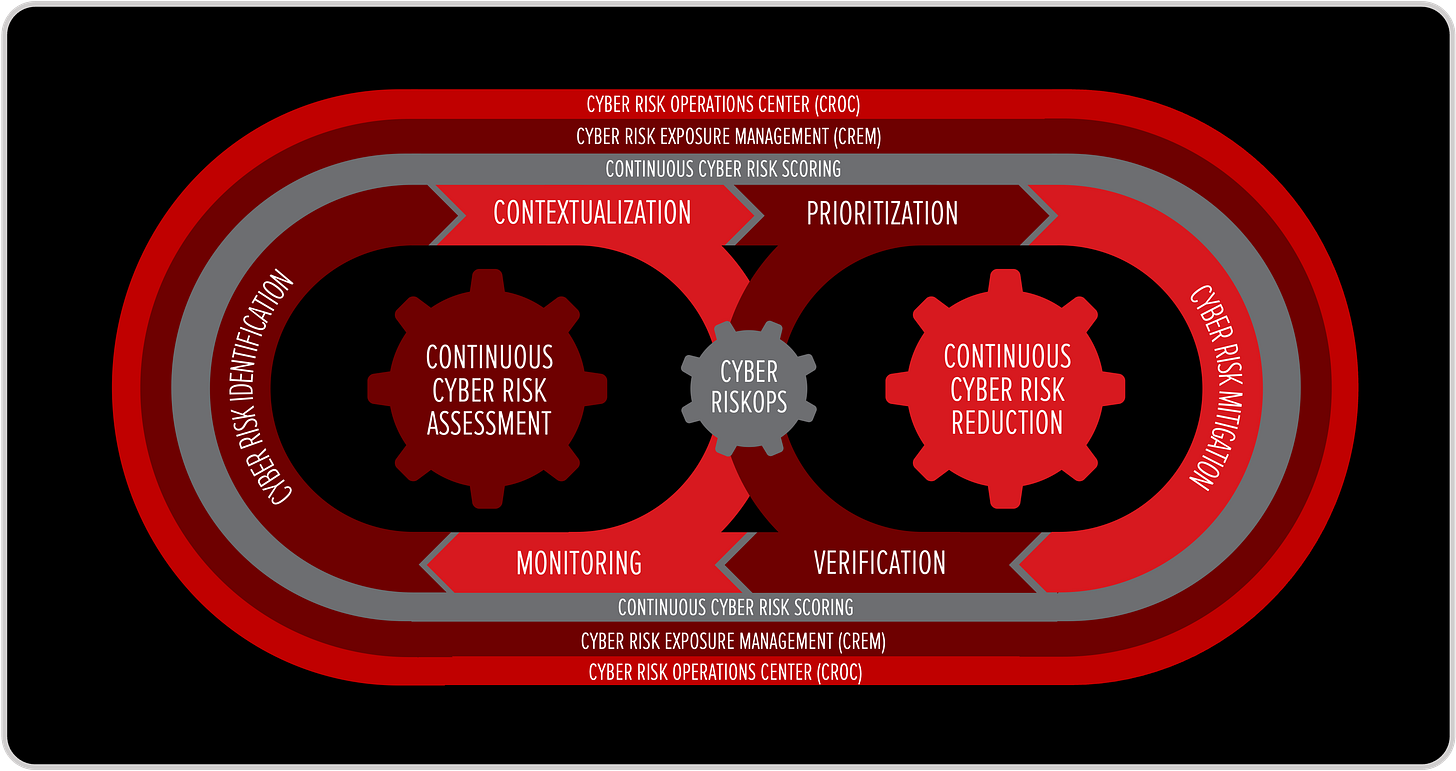
Then came CyberRiskOps, the bridge between strategy and operations, the point where cyber risk management becomes a living discipline. If CRML defines how we manage risk, CyberRiskOps defines how we live with it: continuously identifying, contextualizing, prioritizing, mitigating, verifying, and monitoring exposure across digital ecosystems. CyberRiskOps is not a framework; it is a rhythm, the operating system of modern resilience.
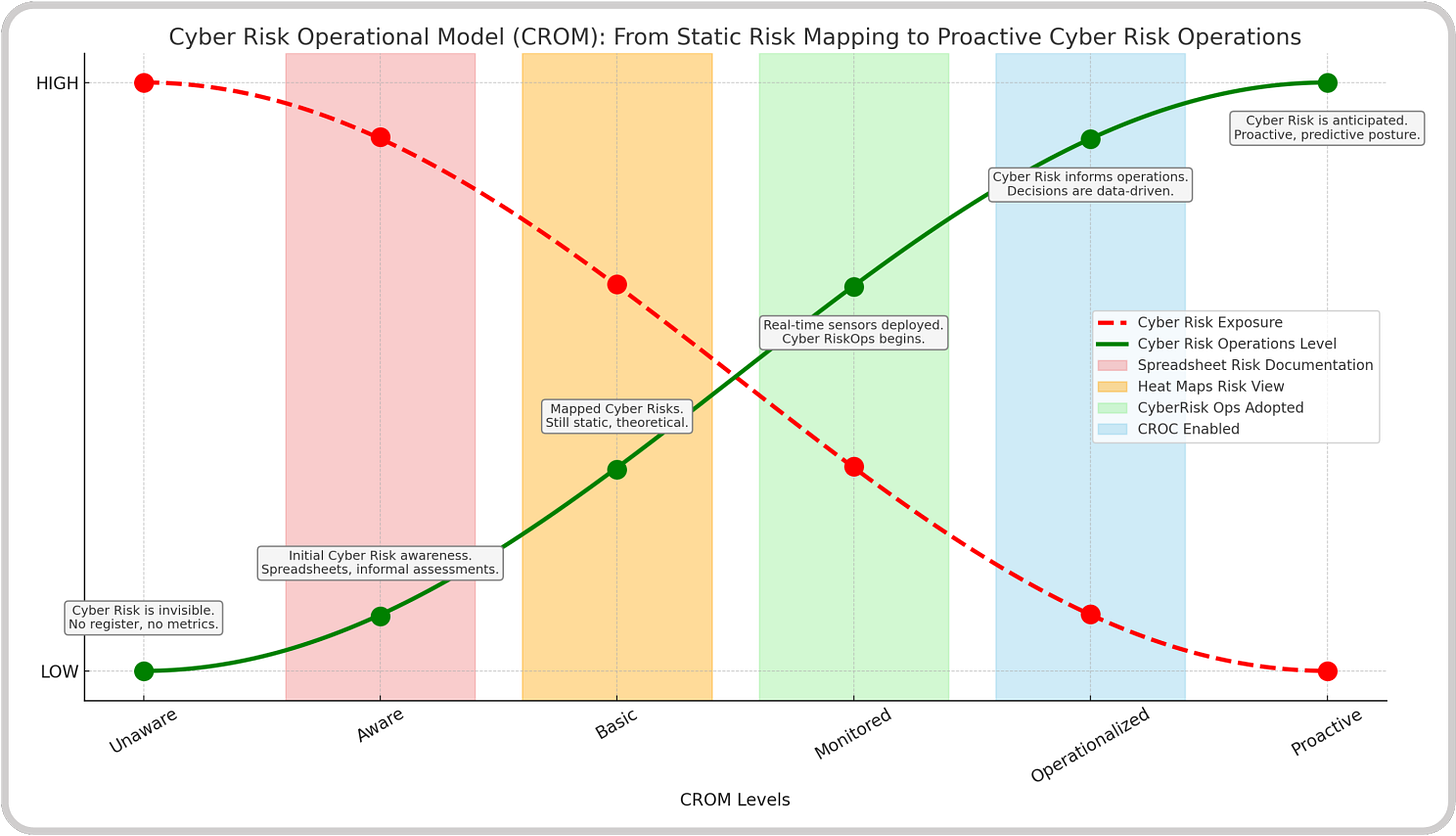
To help organizations measure where they stand in that transformation, I created the Cyber Risk Operational Model (CROM). CROM describes five maturity levels, from unaware to proactive, showing how organizations evolve from static, spreadsheet-based risk mapping to real-time, data-driven risk operations. The model demonstrates how cyber risk exposure decreases as cyber risk operations maturity increases, giving leaders a quantifiable path toward proactive resilience.
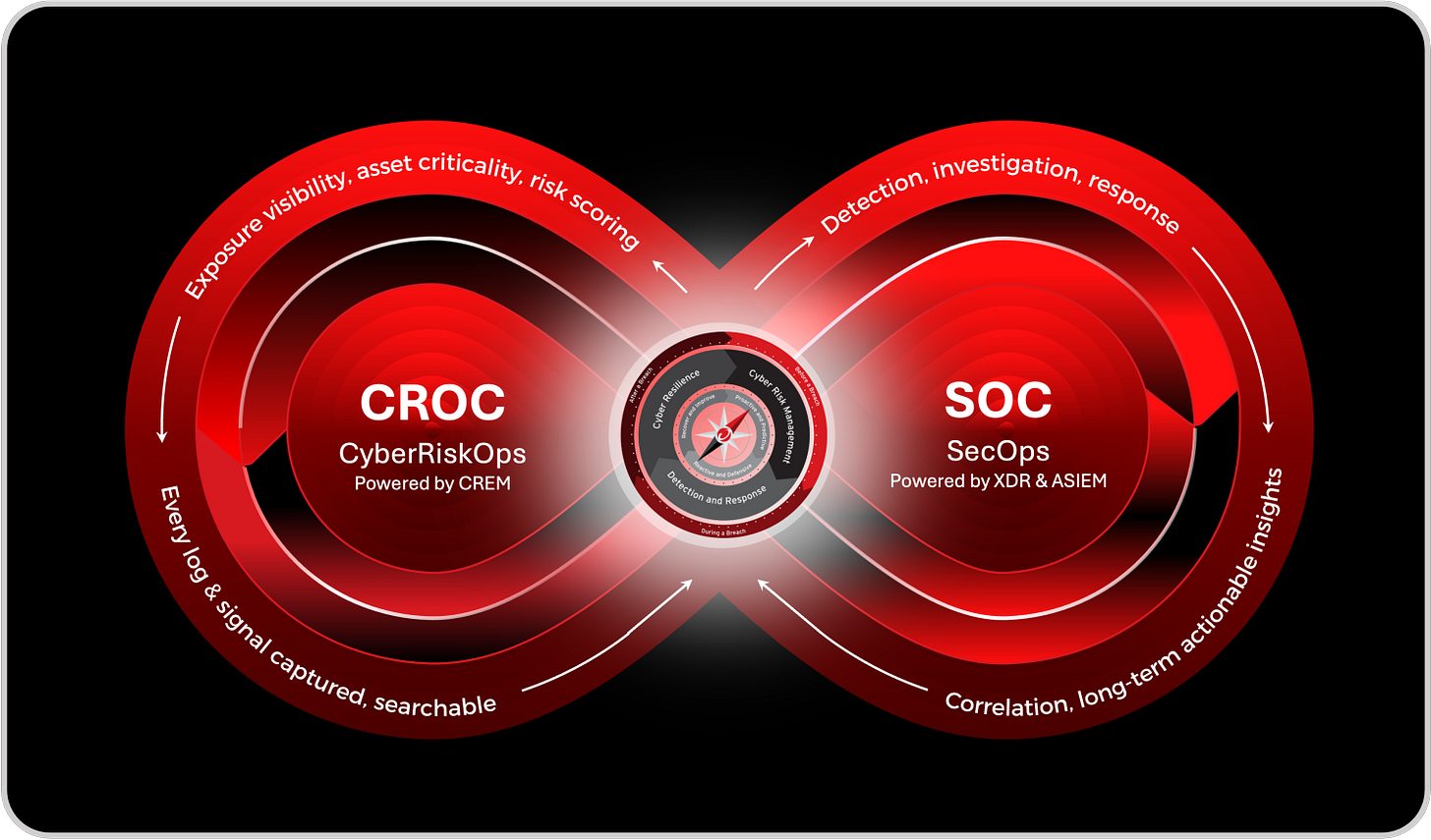
But models and lifecycles alone could not close the gap between governance and execution. We needed a place, a function, that could operationalize this philosophy at scale. That led to the creation of the Cyber Risk Operations Center (CROC), a dedicated capability that complements the traditional Security Operations Center (SOC). While the SOC focuses on detection, investigation, and response, the CROC focuses on exposure, visibility, and reduction, powered by Cyber Risk Exposure Management (CREM). Together, the SOC and CROC form two halves of a continuous loop: one reacting to what has already happened, the other preventing what could happen next.
That loop, the Continuous Defense Loop, completes the vision. It embodies the transition from reactive defense to proactive resilience. It integrates telemetry, quantification, and automation into a living governance model that evolves in real time. In this loop, governance becomes guidance, risk becomes measurable, and resilience becomes continuous.
Each of these frameworks, the Compass, CRML, CyberRiskOps, CROM, CROC, and the Continuous Defense Loop, is part of the same language. They do not compete with existing systems; they connect them. Together, they provide a way for every stakeholder, from the boardroom to the SOC, to understand, measure, and act on cyber risk in their own context but with a shared meaning.
Because in the end, that is the true goal of cybersecurity governance: not compliance, not control, but communication, a common grammar for resilience.
From Fragmentation to Flow
As I’ve observed across industries, most organizations still govern cyber risk as if it were a static concept rather than a living condition. Their governance frameworks, often assembled over time, have become a patchwork of disconnected systems: one tool for audit, another for compliance, another for risk registers, each operating in its own corner. What was meant to unify control has, paradoxically, fragmented it. The outcome is a leadership team looking at twelve dashboards, twelve definitions, and twelve versions of the truth.
Cyber risk, however, cannot be aggregated through documentation; it must be correlated through data. Risk does not live in isolation, and neither should governance. Continuous defense demands continuous data, not quarterly reports stitched together after the fact. What we need is flow, the seamless movement of information from operations to oversight, and from oversight back to operations, where governance stops being a bottleneck and becomes a living feedback loop.
The same distortion appears in the way we visualize risk. Heatmaps, those familiar mosaics of red, yellow, and green, promise clarity but deliver comfort. They create the illusion of control by simplifying uncertainty into colors that everyone can agree on, yet few can act upon. A “low” vulnerability can mean a multimillion-dollar outage if it touches a critical process; a “critical” finding may be irrelevant if it sits in isolation. Colors don’t protect the business, context does. And context only emerges when we quantify risk in dollars, probabilities, and consequences, translating the abstract language of threats into the concrete logic of decision-making.
This shift, from compliance to consequence, from static review to continuous adaptation, defines the future of governance. Compliance tells us whether we did the right thing yesterday; cyber risk management tells us whether we are ready for tomorrow. A company can pass every audit and still fall to ransomware because compliance measures history, while risk management measures velocity.
That is why in the Continuous Defense Loop, governance must become a dynamic process, one that senses, learns, and responds as exposure changes. It’s a system of living telemetry that integrates the technical precision of cybersecurity with the strategic priorities of the business.
In this new reality, the CISO is no longer a guardian of controls but a broker of risk, translating uncertainty into insight, aligning every control and every dollar with measurable impact. The language of GRC must evolve with that role, from policy to probability, from audit trails to risk signals, from oversight to understanding.
And the board, too, must change its questions. Instead of asking, Are we compliant?, it must ask, Are we resilient? Are our defenses evolving as fast as our threats? Are our decisions informed by the same data that guides our adversaries?
Towards Building an Inclusive Cybersecurity Language
The issue is not that GRC and heatmaps exist, it’s that we continue to rely on them to describe a reality they can no longer represent. They were built for a world of predictable cycles and static controls, not for an ecosystem where risk evolves in real time. In cybersecurity, comfort often disguises complacency, and structure can become a substitute for understanding.
Cyber risk is continuous, dynamic, and shared. Managing it requires a language that includes everyone, from engineers to executives, from auditors to architects. A language that translates technical telemetry into business consequence, and business priorities into operational action.
That is what I have sought to create through the Cybersecurity Compass, CRML, CyberRiskOps, CROM, CROC, and the Continuous Defense Loop, not new frameworks for complexity, but a common and inclusive grammar for clarity. A language where risk is measurable, decisions are explainable, and resilience is shared across the enterprise.
Because cybersecurity is not just a technical discipline, it is a collective one. Its future will not be written in colors or compliance reports, but in understanding. In the ability to measure, translate, and communicate risk as one. That is how we move from compliance to consequence, from noise to knowledge, and towards a truly inclusive cybersecurity language that unites technology, risk, and business in the same conversation.
Castro, J. (2025). Cyber Risk and Exposure: Where Risk Meets Reality. ResearchGate. https://www.researchgate.net/publication/395107652 DOI:10.13140/RG.2.2.12965.56804
Castro, J. (2025). Cybersecurity and the Unknown Unknowns: Why the Greatest Cyber Risks Are Off the Map. ResearchGate. https://www.researchgate.net/publication/395206031 DOI:10.13140/RG.2.2.10409.66406
Castro, J. (2025). What Is Strategy in Cybersecurity? Rethinking the Way We Lead, Protect and Adapt. ResearchGate. https://www.researchgate.net/publication/393674625 DOI:10.13140/RG.2.2.16703.42409
Castro, J. (2024). Navigating the Lifecycle of Cyber Risk Management: A Strategic Blueprint. ResearchGate. https://www.researchgate.net/publication/388421392 DOI:10.13140/RG.2.2.14793.25447/1
Castro, J. (2025). Context is Everything in Cybersecurity: Why Signals Without Meaning Are Just Noise. ResearchGate. https://www.researchgate.net/publication/392408653 DOI:10.13140/RG.2.2.15442.26561
Castro, J. (2024). From Definition to Action: Measuring and Managing Cyber Risk. ResearchGate. https://www.researchgate.net/publication/388653064 DOI:10.13140/RG.2.2.15858.21448
Castro, J. (2025). Cyber RiskOps: Bridging Strategy and Operations in Cybersecurity. ResearchGate. https://www.researchgate.net/publication/388194428 DOI:10.13140/RG.2.2.36216.97282/1
Castro,J. (2024). Decoding Cyber Risk: A Visual Representation. ResearchGate. https://www.researchgate.net/publication/388386953 DOI:10.13140/RG.2.2.33733.15849/1
Castro, J. (2025). How to Turn Cyber Risk Assessments into Real Cyber Risk Reduction. ResearchGate. https://www.researchgate.net/publication/388564202 DOI:10.13140/RG.2.2.14029.76007/1
Castro, J. (2024). Cyber Risk 101: Understanding and Managing Cyber Risk. ResearchGate. https://www.researchgate.net/publication/388493450 DOI:10.13140/RG.2.2.23453.83684/1
Castro, J. (2025). Cyber Risk Operational Model (CROM): From Static Risk Mapping to Proactive Cyber Risk Operations. ResearchGate. https://www.researchgate.net/publication/390490235 DOI:10.13140/RG.2.2.15956.92801
Castro, J. (2024). Safely Sailing the Digital Ocean with the Cybersecurity Compass. ResearchGate. https://www.researchgate.net/publication/387410177 DOI:10.13140/RG.2.2.20696.00003
Castro, J. (2024). Risk-Based Cybersecurity: A Dynamic Strategy for the Modern Era. ResearchGate. https://www.researchgate.net/publication/388653135 DOI:10.13140/RG.2.2.34313.15204
Castro, J. (2024). From Reactive to Proactive: The Critical Need for a Cyber Risk Operations Center (CROC). ResearchGate. https://www.researchgate.net/publication/388194441 DOI:10.13140/RG.2.2.27408.93445/1
Castro, J. (2025). The Illusion of “Continuous” in Cybersecurity: The Biggest Vulnerability in Frameworks and Regulations. ResearchGate. https://www.researchgate.net/publication/388682749 DOI:10.13140/RG.2.2.10471.15520/1
Castro, J. (2025). What Is Governance in Cybersecurity?. ResearchGate. https://www.researchgate.net/publication/393065290 DOI:10.13140/RG.2.2.30988.63360
Castro, J. (2025). Cyber Risk Should Not Be Treated - It Should Be Operationalized. ResearchGate. https://www.researchgate.net/publication/389991463 DOI:10.13140/RG.2.2.12429.45289
Castro, J. (2025). Umbrellas, Storms, and Cyber Risk: Why Threat Management Is Not Risk Management. ResearchGate. https://www.researchgate.net/publication/396695719 DOI:10.13140/RG.2.2.24818.98240
Castro, J. (2025). Every Cyber Risk. Every Signal. Continuous Defense Loop. ResearchGate. https://www.researchgate.net/publication/396885730 DOI:10.13140/RG.2.2.30137.22882