The Need for Digital Twins in Cybersecurity: From Awareness to Anticipation
After more than two decades in cybersecurity, I can say this with certainty: I’ve spent most of my career dreaming of this moment.
A moment where we could finally move beyond reacting to yesterday’s breach, where security wasn’t a guessing game, and where defenders had the same strategic advantage as attackers. For years, we’ve been chasing threats in the rearview mirror—deploying patches, updating signatures, running tabletop exercises—all while hoping that our assumptions held up under pressure. But hope is not a strategy.
In a world where cyber threats evolve at machine speed and enterprise ecosystems grow more complex by the day, traditional cybersecurity approaches are no longer enough. The reactive models we’ve relied on—no matter how refined—simply can’t keep pace. Organizations are now shifting to proactive strategies, ones that demand not just new tools, but new ways of thinking.
And among the most transformative of these is the cybersecurity digital twin: a living, data-driven simulation of your environment. Not a snapshot. Not a guess. A continuously updated model that empowers security teams to test, learn, adapt, and act—before attackers do.
This isn’t just an evolution of technology; it’s the realization of a vision that many of us in the field have carried for decades. A vision where we can simulate the unknown, validate defenses in real time, and anticipate risk with clarity. A vision where cybersecurity is no longer confined to alerts and incident reports, but becomes an intelligent, predictive, and strategic function of the business.
We are no longer just protecting what exists. We are beginning to simulate what could go wrong—so we can ensure it doesn’t.
Understanding Digital Twins: A Human Body Analogy
To better grasp the concept of a cybersecurity digital twin, imagine your body as an organization.
Your organs are business-critical systems.
Your nervous system represents data flows and communication channels.
Your immune system is your cybersecurity defense stack—detecting and responding to threats.
Now imagine if you could build a virtual model of your body that continuously monitors your heartbeat, blood flow, brain activity, and immune responses—in real time. This model could simulate:
How your body would respond to a new virus before you’re actually infected.
The effect of introducing a new medication (like a software patch or new security policy).
How fatigue, diet, or stress (think misconfigurations, identity misuse, or lateral movement) might compromise your immune system.
That’s what a cybersecurity digital twin does for your organization.
It mirrors the real-time state of your infrastructure and security posture, allowing you to test “what if” scenarios—without touching the live system. Want to see what happens if a ransomware strain hits your file server? Simulate it. Want to know how changing access policies would affect lateral movement? Model it. Want to practice your immune response to a breach? Train your incident response team inside the twin.
Just like doctors use medical simulations to anticipate and prevent harm, security teams use digital twins to detect weaknesses, validate defenses, and improve resilience—before real damage occurs.
Why Digital Twins? Why Now?
Digital twins have long been the backbone of innovation in sectors like aerospace, automotive, and manufacturing—industries where failure is costly, downtime is unacceptable, and precision is everything. In those fields, digital twins simulate engines, turbines, assembly lines, and supply chains to predict performance, prevent failure, and optimize efficiency. Now, cybersecurity is facing a parallel reality.
As digital transformation accelerates, the logic behind the success of digital twins in operational domains applies with equal—if not greater—urgency to the world of cyber defense. We are no longer managing a static network perimeter. We are navigating a sprawling, hyperconnected ecosystem where every workload, every identity, every cloud API, and every vendor integration expands the attack surface.
Today’s modern enterprise must defend:
Hybrid and multi-cloud infrastructure
IoT and operational technology (OT)
AI-augmented cyberattacks
Dynamic, interconnected supply chains
Meanwhile, security leaders must also deliver on:
Regulatory compliance, with frameworks becoming more stringent and real-time reporting becoming the norm.
Operational resilience, ensuring that cyber disruptions don’t impact service delivery or customer trust.
Board-level risk accountability, where cyber risk is now a core business risk, not just a technical concern.
The sheer scale, velocity, and complexity of today’s threat environment has outgrown traditional tools and practices. Point-in-time assessments, periodic audits, and siloed red team exercises can’t provide the dynamic situational awareness or predictive insight required to manage modern risk. This is where cybersecurity digital twins step in.
By creating a continuously updated, high-fidelity simulation of your environment, digital twins enable organizations to visualize risk, simulate adversarial behavior, validate defenses, and adapt security strategy in real time. They become the foundation for moving from static protection to dynamic risk management—bridging the gap between cyber awareness and cyber readiness.
Simply put: Digital twins allow us to test “what if” before “what now.”
And in today’s cybersecurity landscape, that’s not just helpful—it’s essential.
What Is a Cybersecurity Digital Twin?
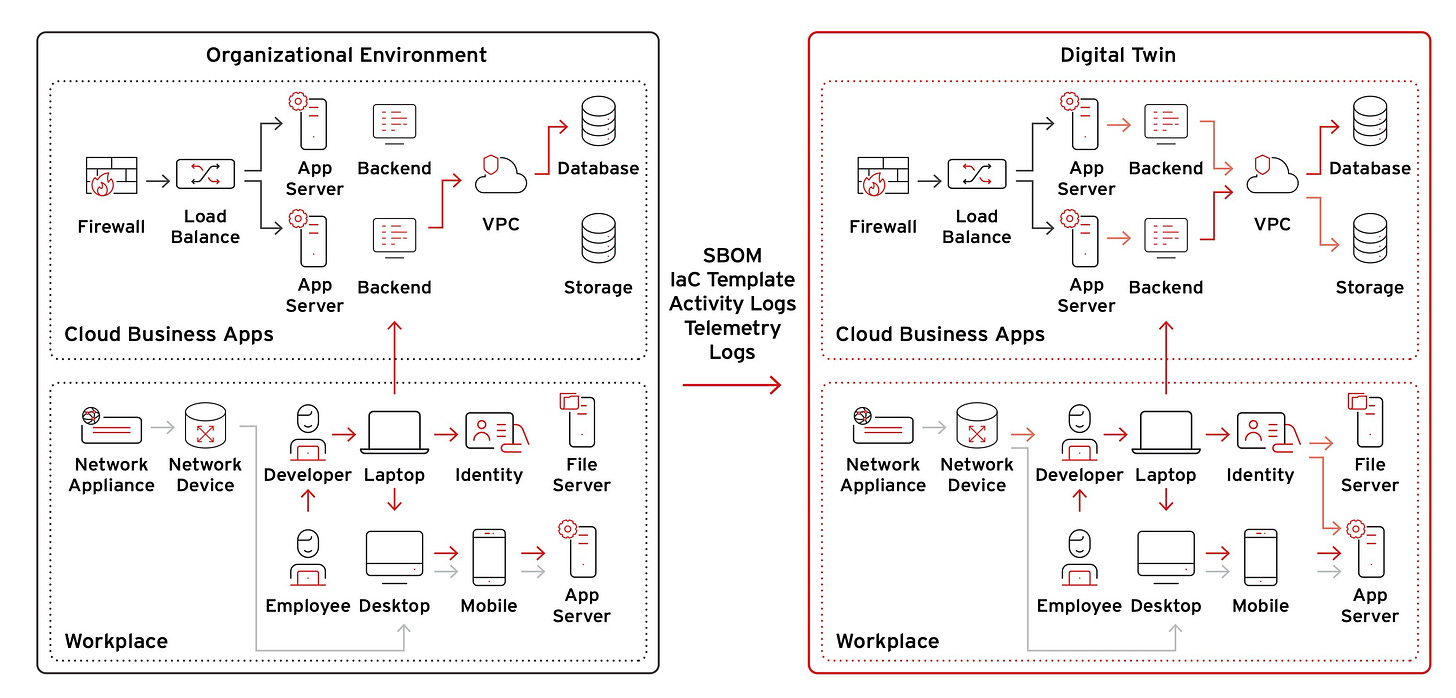
A cybersecurity digital twin is a high-fidelity, continuously updated virtual replica of your organization’s IT and OT environments. But it’s far more than a digital map or asset inventory—it’s an intelligent, simulation-ready model that captures the structure, behavior, and relationships within your cyber ecosystem.
At its core, a cybersecurity digital twin models and mirrors:
Assets – Including cloud workloads, endpoints, IoT devices, containers, and virtual machines.
Identity and access controls – Mapping user roles, credentials, entitlements, and identity provider integrations across systems.
Network traffic flows – Reflecting how data moves within and beyond the organization, from segmentation policies to firewall paths and connection logs.
Security controls and misconfigurations – Tracking patch levels, exposed vulnerabilities, policy gaps, and misaligned configurations.
Application dependencies – Understanding which systems rely on which APIs, services, or third-party tools to function.
Business-critical services and data flows – Capturing how operational processes and digital services are interconnected and where disruptions would hurt most.
This isn’t a snapshot frozen in time—it’s a living, breathing model, constantly refreshed by real-time telemetry, enriched with threat intelligence, and supercharged by AI agents that can simulate adversarial behavior, analyze control effectiveness, and anticipate how your environment would respond under pressure.
Think of it as a flight simulator for cybersecurity—but instead of training pilots, it enables security teams to:
Safely simulate ransomware outbreaks, insider threats, or zero-day attacks.
Test containment strategies, response workflows, and resilience plans.
Visualize lateral movement paths, credential misuse, and impact propagation.
Evaluate the effect of new security controls or architectural changes—before applying them in production.
The digital twin can be as granular or abstract as needed. In some cases, it focuses only on high-value assets and known attack paths. In others, it may emulate an entire hybrid environment—cloud, on-prem, SaaS, and OT—based on telemetry flowing in from XDR platforms, CMDBs, SIEMs, identity providers, and network telemetry tools.
This evolving virtual replica gives defenders the context they’ve historically lacked—connecting technical exposures to business impact, and moving cybersecurity from isolated controls to holistic, risk-aware decision-making.
In essence, a cybersecurity digital twin is not just a tool.
It’s a strategic capability—one that transforms how organizations understand, test, and optimize their security posture in the face of continuous change and escalating threats.
The Power of Simulated Reality: Use Cases That Matter
Digital twins represent a fundamental shift in how cybersecurity operates—transforming it from a series of static snapshots into a real-time, high-fidelity simulation loop. Instead of reacting to alerts and assumptions, defenders gain the ability to test, validate, and adapt their defenses continuously, based on live data and evolving threats.
Here’s how cybersecurity digital twins are being operationalized today—and why they matter:
1. Autonomous Red Teaming at Scale
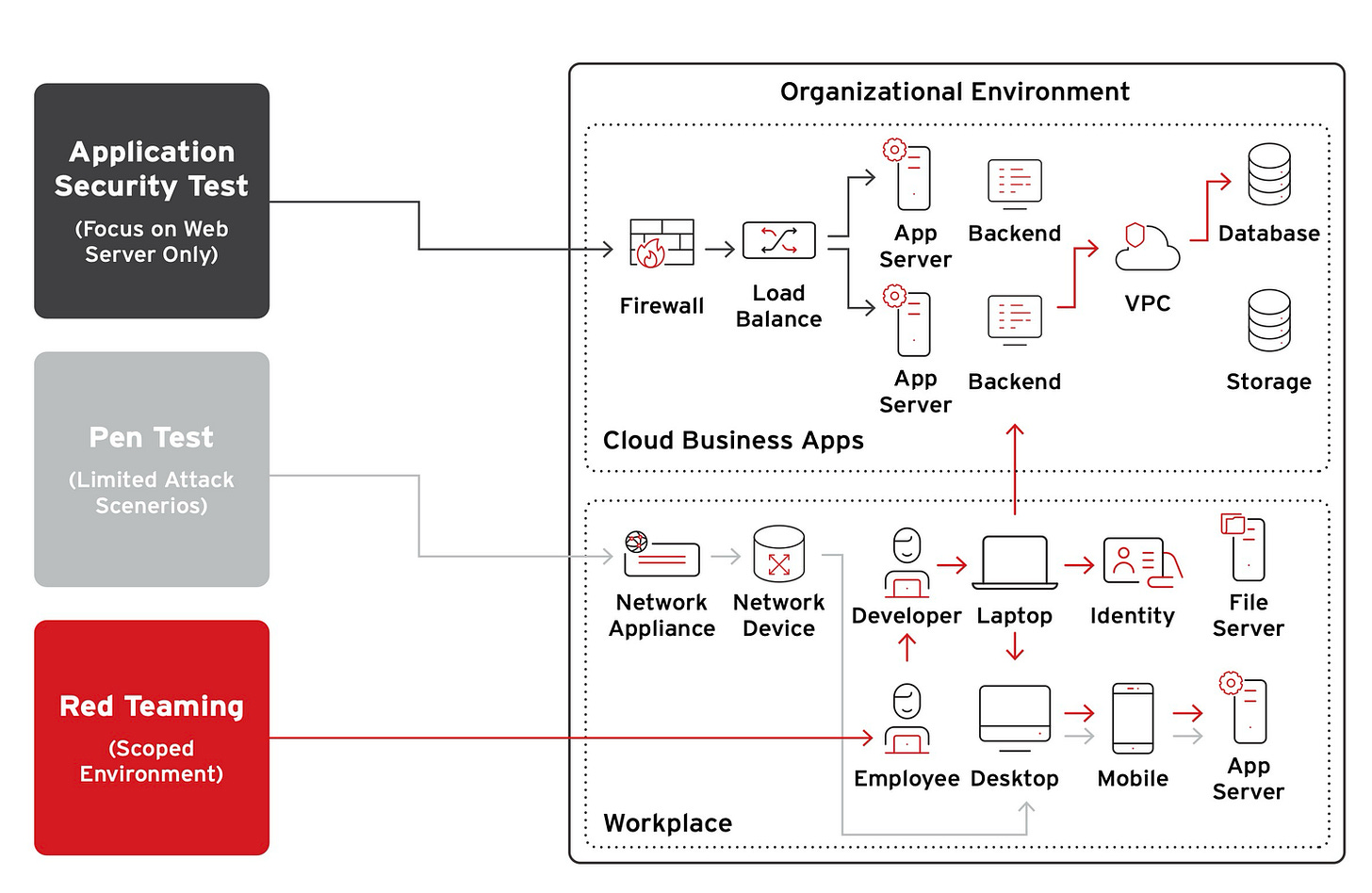
Red teaming has long been one of the most effective ways to discover weaknesses before adversaries do. But traditional red team exercises are time-bound, scoped, and dependent on human resources.
Cybersecurity digital twins change the game. By leveraging AI-powered adversarial agents, organizations can simulate an unlimited number of real-world attack scenarios—such as lateral movement, credential compromise, data exfiltration, and domain escalation—within a safe, isolated replica of their environment.
No risk to production.
No need to wait for annual pen tests.
No reliance on guesswork.
Instead, security teams gain the ability to test defenses continuously—against tactics pulled from the latest threat intelligence, MITRE ATT&CK techniques, or custom scenarios. This approach helps identify gaps in EDR, XDR, identity controls, and segmentation before attackers find them.
2. Continuous Defensive Validation
Defensive controls—like SIEM rules, endpoint policies, access restrictions, and DLP configurations—are only effective if they’re properly tuned and aligned to actual threats. Yet in most organizations, validation is either reactive (after an incident) or episodic (after configuration changes).
Digital twins make defensive validation a continuous process.
Are your detection rules catching credential abuse?
Will your segmentation policies stop lateral movement?
Are your MFA controls truly resilient to bypass techniques?
With a digital twin, these questions are answered not through theory, but through live simulations—where changes to detection logic or policy enforcement can be validated in minutes, not months. The result: faster tuning, fewer blind spots, and higher confidence in your overall defensive posture.
3. Risk-Informed Decision-Making
Cybersecurity budgets are finite. Yet most investment decisions are made using incomplete data—driven by compliance mandates, peer benchmarks, or gut instinct.
Digital twins enable a data-driven, simulation-based model for strategic planning.
Security leaders can simulate the introduction of:
A new EDR/XDR agent
A Zero Trust segmentation policy
An AI-powered threat hunting capability
They can then measure the projected impact on risk exposure, breach likelihood, time to response, or business service uptime. This turns abstract proposals into validated scenarios, making it easier to prioritize efforts, justify investments to the board, and align cybersecurity with enterprise objectives.
4. Real-Time Business Resilience Simulation
In most organizations, security, IT, and business continuity planning live in separate silos. When ransomware hits, or a cloud service fails, the ripple effects across applications, users, and services are often understood only in hindsight.
With digital twins, organizations can simulate those ripple effects in real time—before they occur.
By modeling:
System dependencies
Data flows
Incident response playbooks
Critical business paths
… digital twins help teams identify where bottlenecks, delays, or failures will emerge—and how to mitigate them. This enables live BCDR scenario planning, continuous war-gaming, and smarter automation of recovery workflows.
Security leaders and operations teams gain shared visibility, faster decision-making, and a more resilient response posture.
5. Dynamic Cyber Risk Modeling
Understanding risk is at the heart of modern cybersecurity. But too often, risk assessments are static reports, based on outdated snapshots or generic scoring frameworks. Digital twins enable the next generation of dynamic, scenario-based cyber risk modeling.
By continuously ingesting live telemetry—across identity, assets, network, and vulnerabilities—and overlaying it with adversarial simulations and threat intelligence, the digital twin becomes a real-time risk engine.
Organizations can ask and answer critical questions such as:
What’s the real-world blast radius of this misconfiguration?
If this vulnerability is exploited, what systems and data would be impacted?
What’s the risk to our business if this third-party integration is compromised?
This approach allows for contextual, continuously updated risk scores, not just at the asset level but across workflows, departments, and critical business services.
And because simulations are tied to actual architecture and behaviors, the risk insights are grounded in operational reality—helping risk managers, CISOs, and executives prioritize based on actual impact, not theoretical exposure.
Simulate. Validate. Adapt. Repeat.
Together, these five use cases illustrate how digital twins unlock a continuous improvement cycle in cybersecurity. They enable defenders to simulate the unknown, validate assumptions, and adapt defenses—not reactively, but intelligently and preemptively.
In an era where attackers use AI to move faster and target smarter, cybersecurity must evolve into a dynamic, risk-aware, and simulation-driven discipline.
Digital twins are the foundation of that evolution.
From Engineering to Cybersecurity: The Three Layers Powering Digital Twins with AI
Digital twins are not a new concept. They’ve been used for decades in engineering disciplines—from simulating aircraft engines to optimizing factory floors. But what makes them revolutionary for cybersecurity today isn’t the model itself—it’s what happens when we combine digital twins with artificial intelligence.
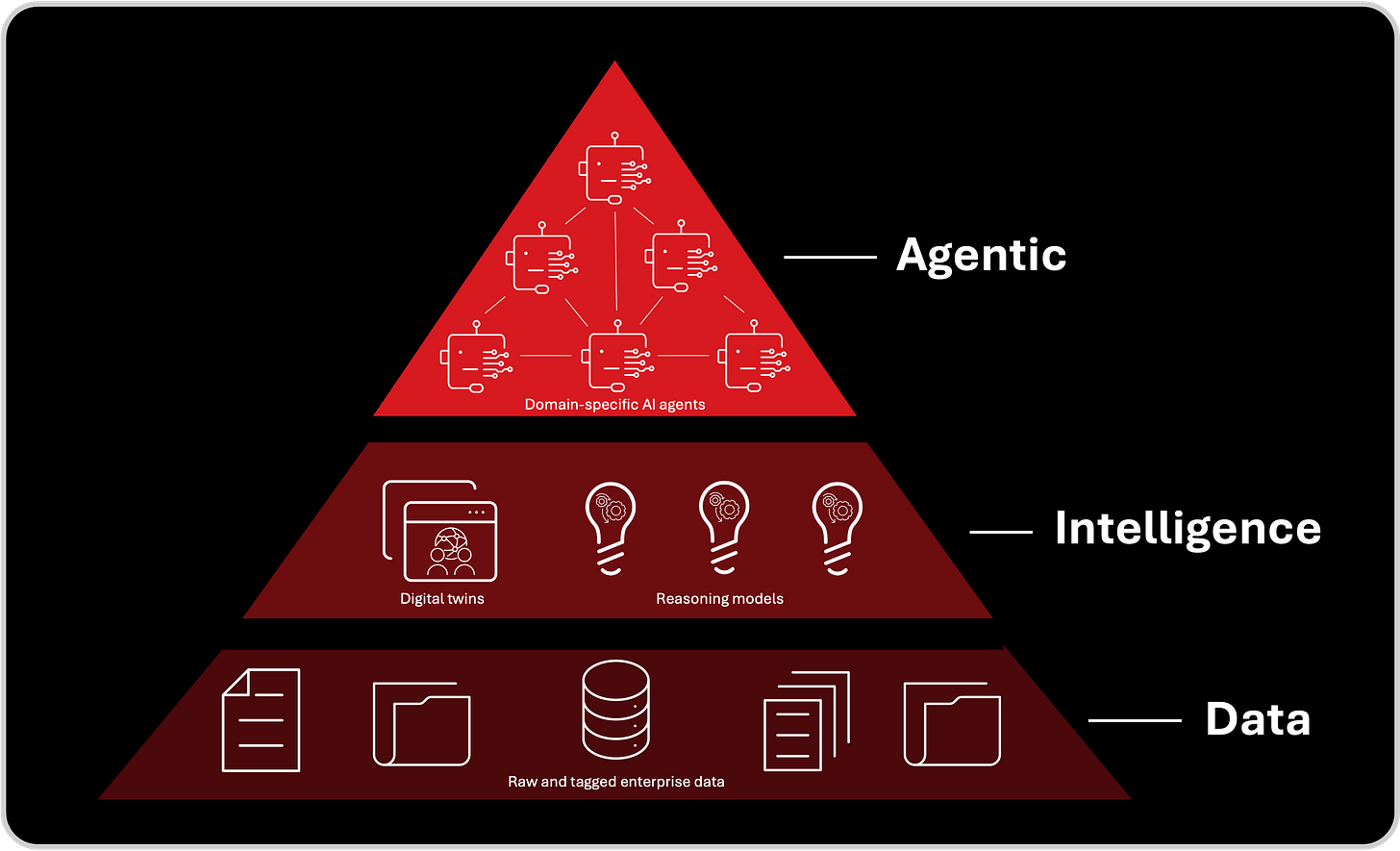
This transformation unfolds across three foundational layers, each building on the one before it to create a digital twin that doesn’t just reflect reality—it understands it, interrogates it, and adapts to it in real time.
Layer 1: The Data Layer – Real-Time, High-Fidelity Ground Truth
At the core of every effective digital twin is data. Without comprehensive, accurate, and continuously updated telemetry, there is no twin—only an outdated snapshot.
This foundational layer includes:
Asset inventories (cloud, endpoint, OT, IoT)
Identity and access data
Network traffic flows and segmentation
Vulnerability scans and misconfigurations
Application dependencies
Security telemetry (SIEM, XDR, logs, threat intelligence)
This is the raw material that gives the digital twin its fidelity. The more connected and complete the data, the more nuanced and trustworthy the simulation becomes.
Layer 2: The LLM Layer – Contextual Understanding and Intelligence Mapping
With telemetry in place, the next step is giving the digital twin contextual awareness. This is where Large Language Models (LLMs) come into play.
LLMs ingest and interpret vast amounts of unstructured and structured information—from threat intel reports and CVE disclosures to system logs and detection rules. They act as a reasoning engine, helping the digital twin understand:
Which threats are relevant to your environment
How vulnerabilities relate to exposed assets
What tactics and techniques adversaries are currently using
How different changes (e.g., patching or segmentation) would impact security posture
This layer is like giving the digital twin a brain that can read, correlate, and think across technical and business dimensions—bridging global intelligence with local telemetry.
Layer 3: The Agentic AI Layer – Autonomous Behavior and Decision Simulation
If data is the body and LLMs are the brain, agentic AI is the will to act.
In this top layer, autonomous AI agents operate within the digital twin as both attackers and defenders. These agents can:
Simulate ransomware infections, insider threats, and lateral movement
Test the effectiveness of defensive tools and response playbooks
Execute containment, remediation, and policy tuning automatically
Learn over time which strategies reduce risk most effectively
This transforms the digital twin from a diagnostic tool into a proactive actor—one that continuously tests your environment, validates controls, and recommends or executes defensive actions.
The result is a self-improving, always-on cyber defense model: simulate, validate, adapt—on loop.
From Model to Mind: A New Operational Paradigm
Together, these three layers turn cybersecurity digital twins into something unprecedented:
A living map of your cyber environment (Data)
A reasoning system grounded in threat and business context (LLM)
An autonomous simulator that stress-tests and hardens your defenses (Agentic AI)
This isn’t theoretical—it’s happening now.
And it’s how cybersecurity shifts from reacting to predicting, from auditing to adapting, and from defending to simulating risk before it becomes real.
Embracing the Cybersecurity Digital Twin Era
We are standing at a pivotal inflection point in cybersecurity.
For decades, we’ve battled threats with incomplete information, outdated assumptions, and tools that could tell us what just happened—but not what could happen next. We’ve patched, segmented, monitored, and responded—but always from behind. Cybersecurity digital twins mark the beginning of a new era—one where we stop reacting and start simulating, validating, and anticipating. This isn’t just about technology. It’s about mindset.
Digital twins give us the ability to:
See clearly across complex, hybrid environments.
Simulate intelligently using real-world threats and AI adversaries.
Respond confidently with evidence-based action.
Align cybersecurity with business priorities, risk appetite, and operational resilience.
They allow defenders to reclaim the advantage—to operate with foresight rather than hindsight, to prepare rather than patch, and to manage risk as a continuous, adaptive process.
After more than two decades in this field, I can say with certainty: this is the shift I’ve been waiting for.
Cybersecurity digital twins are not a trend or a tool—they are a strategic capability for a world where risk is continuous, complexity is accelerating, and attackers never rest. Whether you’re securing a global enterprise, a critical infrastructure network, or a modern supply chain, the time to embrace this capability is now.
Because in cybersecurity, the future doesn’t belong to those who react fastest—it belongs to those who simulate first, make decisions with clarity, and take action before threats become incidents.