How the Cyber Risk Operations Center (CROC) Uses Vision One ASRM to Operationalize Cybersecurity Strategy
We created the Cybersecurity Compass in response to the growing challenges faced by cybersecurity professionals and stakeholders alike. It serves not only as an integrated cyber defense strategy but also as a way to create a common language between technical teams and decision-makers. By empowering cyber strategists, defenders, and responders to navigate the complex landscape of cyber threats and cyber risks with confidence, the Cybersecurity Compass bridges the communication gap. By addressing the key elements of people, process, and technology at every stage, organizations can strengthen their security posture.
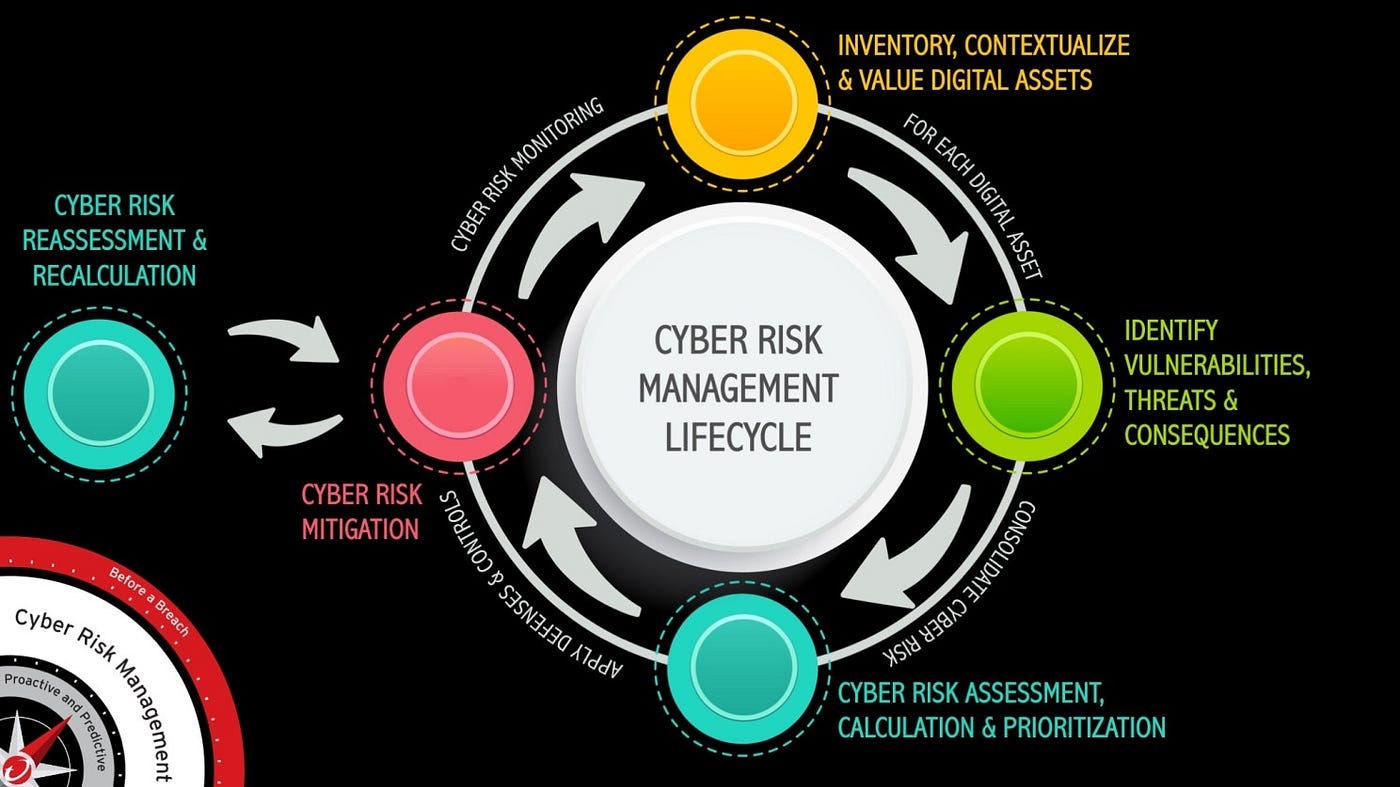
The Cybersecurity Compass provides essential direction and guidance to safely chart a course through the turbulent digital seas, ensuring not just survival but lasting success in the digital age. A critical component of this strategy is the Cyber Risk Operations Center (CROC), which operationalizes cyber risk to improve cybersecurity strategy and bolster organizational resilience. The CROC transforms the strategic vision of the Cybersecurity Compass into actionable insights, integrating fragmented data and making cyber risk management a continuous, adaptive process.
In today’s complex cybersecurity landscape, organizations face a vast array of cyber risks stemming from endpoints, email, identity systems, networks, cloud environments, containers, and operational technology systems. These risks can be overwhelming, particularly when the data is fragmented across different dashboards and tools. The Cyber Risk Operations Center (CROC), powered by Trend Micro’s Vision One Attack Surface Risk Management (ASRM), unifies this fragmented data, transforming it into actionable insights and facilitating comprehensive cybersecurity management.
Moreover, the integration of AI further enhances the CROC’s ability to contextualize and prioritize risks, enabling faster and more informed decision-making across diverse environments.
The Role of the CROC in Modern Cybersecurity
The CROC serves as a centralized command for cybersecurity operations, integrating cyber risk data from various sources across endpoints, email, identity systems, networks, cloud environments, containers, and OT infrastructures. This unified approach aligns security actions with business priorities and orchestrates remediation across these domains.
Through CROC, organizations can:
Consolidate Cyber Risk Findings Across Multiple Domains: The CROC gathers cyber risk metrics from across the enterprise, creating a centralized platform for viewing and managing risks across critical assets, including the complex cloud environments.
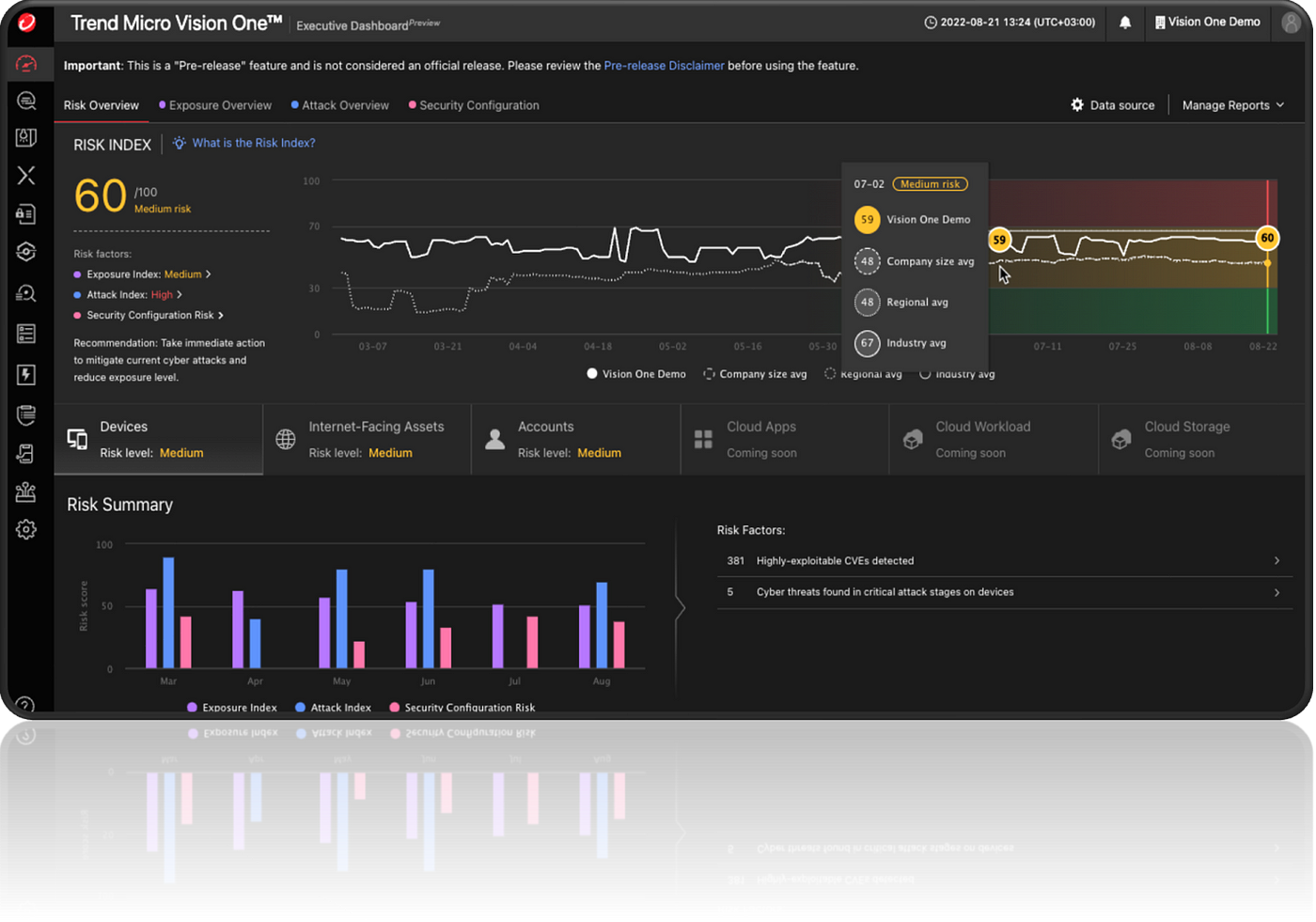
Enable Real-Time Insights with AI-Driven Contextualization: By continuously monitoring all systems — from endpoints to cloud workloads — the CROC provides real-time updates on cyber risk posture. AI algorithms within Vision One ASRM analyze this data, offering enhanced contextualization and prioritization of risks based on business impact and threat intelligence
Facilitating Collaboration: Using the Cybersecurity Compass as a framework the CROC creates a common language between key stakeholders like CISOs, CROs, CFOs, and other decision-makers, ensuring that everyone is aligned in understanding and addressing cyber risks. By delivering data-driven insights, it helps coordinate efforts across risk management, budgeting, and cyber insurance strategies. This shared understanding fosters better communication and unified decision-making across departments, leading to a more integrated and effective cybersecurity approach.
Synergy with the Security Operations Center (SOC): The CROC works in close synergy with the SOC, combining strategic risk management with operational threat detection and response. While the SOC focuses on real-time threat monitoring and incident response, the CROC adds a layer of long-term risk prioritization and mitigation. This collaboration allows for more efficient coordination between responding to immediate threats and addressing broader, systemic risks. By feeding actionable insights into the SOC, the CROC ensures that the most critical risks are swiftly communicated, enhancing the organization’s overall security posture.
Enabling Proactive Risk Mitigation: The CROC empowers organizations to adopt a proactive risk mitigation strategy by continuously monitoring systems and prioritizing risks. This ensures that vulnerabilities are identified and addressed before they escalate into critical issues. With a proactive stance, organizations improve their resilience, preventing potential incidents and staying ahead of evolving threats.
Leveraging Cybersecurity Standards for Cyber Risk Calculation and Prioritization
The CROC’s operations are rooted in cyber risk scoring based on well-established cybersecurity frameworks, ensuring systematic cyber risk management and adherence to industry best practices.
NIST 800–30 (Risk Assessment Framework): This standard defines how organizations can assess the likelihood and impact of cyber risks. By following NIST 800–30, the CROC ensures that risk assessments are comprehensive, covering a wide range of attack vectors — from email phishing to vulnerabilities in OT systems .
NIST 800–60 (Information and System Categorization): NIST 800–60 categorizes assets based on their impact on the organization’s mission. This helps CROC prioritize vulnerabilities and threats based on the criticality of the assets they affect — whether that’s a cloud environment supporting essential applications or an OT system critical to business operations
MITRE ATT&CK (Adversarial Tactics, Techniques, and Common Knowledge): The MITRE ATT&CK framework helps CROC identify tactics and techniques used by adversaries, aligning cyber risk data with real-world attack scenarios. This allows the CROC to proactively mitigate high-risk vulnerabilities before they can be exploited by threat actors .
Vision One ASRM: Enhancing CROC’s Capabilities Across Multiple Domains
Trend Micro’s Vision One ASRM platform enhances the CROC’s ability to assess and prioritize cyber risks across various environments. ASRM integrates data from endpoints, cloud workloads, email systems, containers, identity management tools, and OT systems, delivering a comprehensive view of the organization’s attack surface.
Key features of Vision One ASRM within CROC include:
Unified Asset Inventory Across Critical Systems: The platform consolidates data from endpoints, cloud environments, networks, and more, creating a complete asset inventory that ensures continuous monitoring of vulnerabilities across all domains.
Dynamic Cyber Risk Prioritization Based on Standards: Vision One ASRM uses AI-driven risk scoring that aligns with standards like NIST 800–30 and 800–60 to prioritize risks based on business impact and asset criticality. The integration with MITRE ATT&CK further refines prioritization by aligning vulnerabilities with known attack techniques .
Risk-Based Vulnerability Management: Vision One ASRM’s risk-based vulnerability management approach prioritizes vulnerabilities by considering both the likelihood of exploitation and the potential business impact. This ensures that security teams focus on high-priority risks, whether those are in cloud environments, containers, or traditional endpoints .
Business Context and Shared Cyber Risk Responsibility
Vision One ASRM introduces a feature that enables organizations to organize their assets into groups, allowing for:
Visualizing the overall structure of the organization, providing clarity on how different departments and functions are interconnected.
Streamlining workflows by managing assets in groups instead of individually, making cyber risk management more efficient and scalable.
Viewing Cyber Risk Subindexes for individual asset groups, enabling the identification of higher-risk areas. This granular view ensures that cyber risk is not only managed at the organizational level but also communicated effectively across business units and teams.
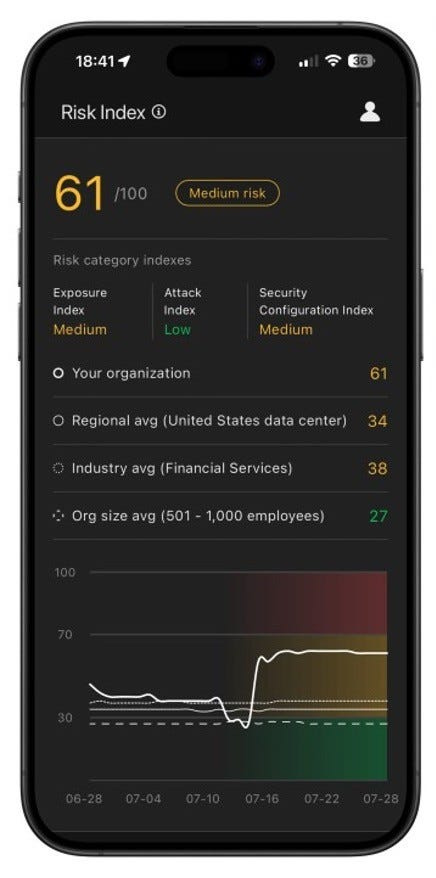
Additionally, Vision One ASRM includes a mobile app that allows any stakeholder within the organization to monitor and view the up-to-date cyber risk score in real time. This app enhances transparency and engagement by enabling stakeholders to:
Stay informed about the organization’s current cyber risk posture.
Ask questions and seek clarity on specific cyber risks or actions.
Actively participate in ongoing cyber risk management discussions and processes.
This mobile app ensures that cyber risk management becomes a continuous, interactive, and inclusive process across the organization, helping all stakeholders stay engaged and involved in maintaining the company’s cyber security resilience.
These two features of Vision One ASRM foster shared responsibility in cyber risk management, ensuring that all parts of the organization are actively involved. The Cyber Coach role enables the CROC to articulate this shared responsibility by guiding teams at different levels to understand their specific cyber risks and providing actionable advice on how to manage those risks effectively. This approach strengthens overall security alignment across the organization, ensuring that cyber risk management is an integrated and collaborative process.
Overcoming Fragmentation with AI-Enhanced Remediation
Organizations often face challenges coordinating remediation efforts across their diverse technology environments. AI-enhanced orchestration within CROC automates remediation tasks, reducing the time to mitigation.
Automation of Remediation Tasks with AI: Vision One ASRM integrates with tools like ServiceNow and JIRA to automate the assignment of remediation tasks. AI algorithms prioritize remediation based on the severity of the cyber risks identified in different environments, ensuring that the most critical issues are addressed first.
End-to-End Orchestration Across Systems: AI enables the CROC to orchestrate responses across all domains — whether from endpoints, email systems, network traffic, identities, cloud workloads or containers. This reduces mean time to remediation (MTTR) and ensures coordinated responses to high-priority threats .
The Role of AI in Cyber Risk Contextualization and Prioritization
One of the key advantages of the CROC is its use of AI to contextualize and prioritize cyber risks. AI algorithms analyze vast amounts of data, identifying patterns and providing deeper insights into potential threats. This allows the CROC to:
Enhance Risk Scoring with AI: AI improves the accuracy of cyber risk scores by analyzing factors like asset criticality, current threat intelligence, and historical attack patterns. This ensures that vulnerabilities affecting the most critical systems, such as cloud infrastructures or OT environments, are prioritized appropriately .
Accelerate Decision-Making: By providing real-time, AI-driven insights into the organization’s risk posture, the CROC allows security teams to make faster, more informed decisions, focusing on the vulnerabilities that pose the greatest risk to the organization .
The Importance of Risk-Based Vulnerability Management Across Diverse Environments
As digital infrastructures become more complex, spanning cloud environments, containers, risk-based vulnerability management is critical. This approach ensures that security resources are focused on the highest-priority vulnerabilities, rather than treating all vulnerabilities equally.
Focusing on Business-Critical Threats: With AI-driven insights and adherence to NIST 800–60, CROC prioritizes vulnerabilities based on the business impact of the affected systems — whether those are cloud applications, identity systems, or endpoint workstations .
Continuous Cyber Risk Scoring and Improvement: AI within Vision One ASRM continuously recalculates cyber risk scores based on evolving data from all environments. This real-time updating ensures that organizations can track improvements in their security posture and stay ahead of emerging threats.
Shifting from Reactive to Proactive Defense
The before-a-breach stage of cyber risk management is a core principle of the Cybersecurity Compass. It emphasizes the need for organizations to identify and address vulnerabilities before they are exploited. The CROC operationalizes this approach by using attack path prediction, which maps out potential attack vectors based on interconnected vulnerabilities. This predictive capability helps security teams visualize where attackers might strike, allowing them to take preventative action.
For example, the CROC can identify a vulnerability in a cloud environment that could be exploited for lateral movement across critical systems. By proactively addressing this weakness, the organization strengthens its defenses and reduces the risk of a breach. This proactive, before-a-breach approach is a key to improving overall security posture and aligns directly with the strategic guidance of the Cybersecurity Compass.
Predictive Capabilities with Knowledge Graphs
The CROC leverages AI-driven knowledge graphs provided by Vision One ASRM to predict and visualize attack paths across the organization’s infrastructure. These graphs connect risks across endpoints, cloud workloads, containers, and OT systems, offering a comprehensive view of how adversaries could exploit these vulnerabilities. By continuously updating these models with new threat intelligence, the CROC ensures that its predictions remain relevant and can anticipate future risks .
Enhancing Visibility and Context
Attack path prediction not only empowers security teams to act proactively but also enhances visibility and context into their security posture. By viewing the organization’s attack surface from an attacker’s perspective, the CROC enables teams to prioritize remediation efforts based on the most likely and dangerous attack scenarios. This allows security teams to focus on the most critical vulnerabilities that could cause significant business impact.
Personalized Cyber Risk Reduction and Business Alignment
The CROC, supported by Vision One ASRM, enables personalized cyber risk reduction strategies that align with the organization’s unique business goals. AI enhances the ability to contextualize risks within the business framework, ensuring that the most critical vulnerabilities are addressed first.
AI-Driven Business Context: By applying AI to contextualize cyber risks in terms of business priorities, the CROC ensures that resources are focused on mitigating the risks that could have the greatest impact on the organization’s operations — whether those risks emerge in traditional or cloud infrastructure.
Faster Mitigation of High-Priority Risks: AI streamlines the process of identifying, contextualizing, and remediating high-priority vulnerabilities, reducing the time it takes to address critical risks and improving overall security posture.
Benchmark Security Posture: Companies can track the progress of their cyber risk reduction efforts over time and compare their risk posture against industry peers .
Focus on Business-Critical Threats: By understanding which assets are most critical to business operations, the CROC ensures that the organization focuses its efforts on the most impactful risks
Operationalizing the CROC
The integration of Vision One ASRM within the Cyber Risk Operations Center (CROC) revolutionizes how organizations manage cyber risks across endpoints, email, identity systems, networks, cloud environments, containers, and OT. By leveraging cybersecurity standards like NIST 800–30, NIST 800–60, and MITRE ATT&CK, combined with AI-driven contextualization and prioritization, the CROC empowers security teams to prioritize and remediate the most critical threats swiftly and efficiently. This unified, AI-enhanced approach ensures that organizations maintain a resilient and adaptive cybersecurity posture in an increasingly complex digital landscape.