How Do We Measure the Quality of Decisions in Cybersecurity?
Most cybersecurity programs measure activity. Few measure what actually matters: decision quality.
In cybersecurity, success is often measured in tools deployed, alerts blocked, or incidents contained. Dashboards full of red-to-green metrics and quarterly reports showing incident counts have long been the way we “prove” progress.
Yet, those are outcomes — snapshots of activity, not the true levers of resilience. A company can deploy dozens of tools, block millions of attacks, and still fail catastrophically because the wrong decisions were made at the wrong time.
Through my work and conversations with leaders across industries, I’ve learned that what really separates resilient organizations from fragile ones is not how many alerts they stop, but how they decide:
How they decide which cyber risks to prioritize.
How they decide where to allocate scarce resources.
How they decide when to act — and when not to.
And most importantly, how they decide again when the environment shifts, as it always does.
The real measure of a strong cybersecurity strategy is therefore the quality of the decisions an organization makes under cyber uncertainty.
As I’ve argued before:
Cybersecurity strategy is an integrative set of choices that positions your organization on a cyber risk landscape of your choice in a way that sustains resilience over time.
In other words: your ability to make — and remake — clear, cyber risk–informed decisions is your ultimate strategic advantage.
Decisions: The Real Currency of Cyber Resilience
When we strip cybersecurity down to its essence, it’s not about the tools we buy or the frameworks we adopt — it’s about the choices we make under pressure.
Every investment, every control, every response plan is the product of a decision. And because the cyber threat landscape shifts constantly, those decisions must be remade, refined, and revalidated over time.
This is where many organizations stumble: they aim for a “perfect plan” that will hold indefinitely. But in reality, resilience doesn’t come from perfection — it comes from the ability to adapt decisions continuously.
For cybersecurity leaders, the real challenge is not drafting static strategies. It’s building a decision framework — one that aligns teams, guides investments, and sustains cyber resilience in a world that doesn’t stop moving.
And that’s where cyber risk management plays its most vital role: not as a compliance exercise, but as the engine that feeds better decisions.
Cyber Risk Management as Decision Support
The primary purpose of cyber risk management is not documentation or compliance. It’s this:
To improve the quality of decisions made by leaders within an organization.
In the context of cyber risk, that means giving decision-makers clear, accurate, and timely information about threats, exposures, and business impact. The ultimate goal is not to eliminate cyber risk (impossible) but to balance cyber risk with opportunity — ensuring resilience and strategic progress.
That’s why I keep advocating for measuring cyber risk in some form. It doesn’t have to be perfect — but without a defined measure, we cannot evaluate or improve our decisions.
As the saying goes:
“What is not defined cannot be measured. What is not measured, cannot be improved. What is not improved, is always degraded.”
And this brings us to a critical distinction that often gets blurred in practice: the difference between mitigation and cyber risk reduction.
Mitigation vs. Cyber Risk Reduction: Why the Words Matter
I’m often asked about the difference between mitigation and cyber risk reduction in the cybersecurity context. Although they sound similar, there’s a crucial distinction:
Mitigation: These are the actions or controls you put in place to lessen the probability or impact of a cyber threat. Examples include rolling out a new email filtering solution, segmenting your network, or instituting stronger access controls.
Cyber Risk Reduction: This is the outcome — the actual decrease in overall cyber risk exposure once your mitigation strategies have taken effect.
In other words, you can deploy security tools and policies (mitigation) without necessarily lowering your cyber risk (reduction).
Organizations frequently mistake doing something (mitigation) for achieving tangible change (cyber risk reduction). It’s the difference between installing a next-gen firewall versus demonstrating how that firewall measurably lowered the likelihood and impact of certain attack vectors.
Understanding — and measuring — this distinction is central to closing the gap in cybersecurity.
And it naturally raises the next question: how do we measure whether our decisions are actually reducing cyber risk exposure?
Decision Quality as Cyber Risk Reduction
How do we measure decision quality? One useful lens is cyber risk reduction.
Better decisions should translate into less cyber exposure over time. Not just more mitigations, but measurable reductions in the cyber risk landscape your organization faces.
This is why mitigation vs. reduction matters so much: you can mitigate endlessly and still not reduce cyber risk. But you cannot reduce cyber risk without making better decisions.
To validate that connection, organizations need a reliable yardstick — and that’s why the Cyber Risk Index has emerged as a key measure
Why a Cyber Risk Index Matters
Here lies the real challenge: how do we know if our decisions are actually reducing cyber exposure?
Investments in controls, new tools, or policies often get justified as “mitigations.” But without a measurement framework, we can’t answer the core question: Is this mitigation truly lowering our cyber risk?
That’s where a Cyber Risk Index (CRI) comes in. A CRI provides a quantitative snapshot of cyber exposure over time, blending threat likelihood, vulnerabilities, and business impact into a score or benchmark. It doesn’t need to be perfect, but it must be consistent — a way to evaluate whether decisions and mitigations are creating measurable reductions in cyber risk.
As I’ve previously discussed, the real strength of a CRI lies in two things:
Transparency — the methodology must be open and understandable, so that leaders and stakeholders trust the numbers.
Public methodology — without a clear, defensible way of calculating the index, it’s just another opaque metric.
These elements are essential for decision quality. Because if my organization’s CRI was 62.3 before a major cybersecurity decision, then after implementing that decision I should expect to see a tangible reduction in the score. If the index doesn’t move, then the decision may have been activity without impact.
Think of the CRI as a KPI for decision quality:
If the CRI improves after a series of decisions, we know those choices were effective.
If the CRI stagnates or worsens, then our mitigations may be cosmetic — activity without impact.
Over time, the CRI becomes the baseline for comparing decision-making performance across teams, initiatives, or even business units.
Without an index or metric like this, decision quality remains subjective. With it, leaders can demonstrate progress, validate investments, and refine decision frameworks continuously.
And once that measurement loop exists, it can be operationalized — which is exactly what Cyber RiskOps was designed to do.
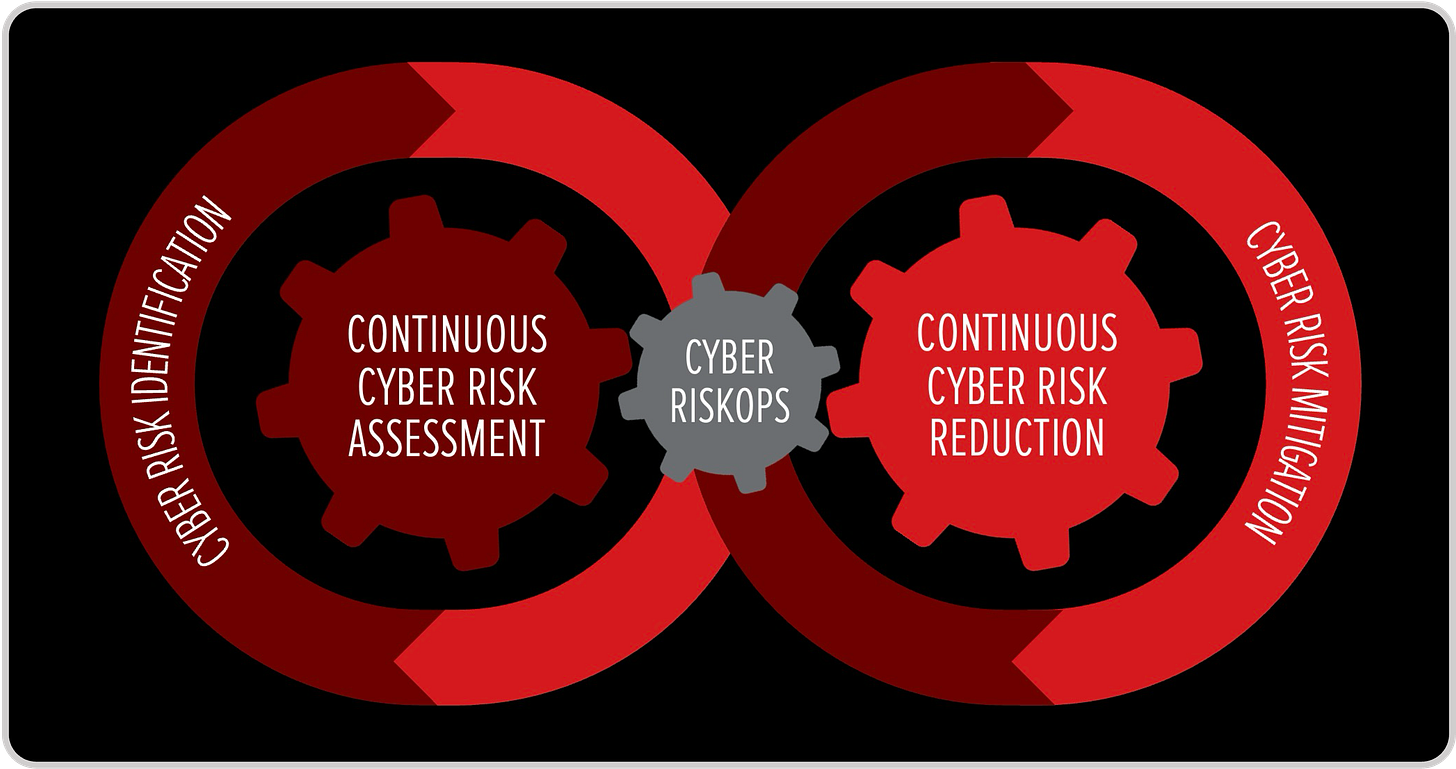
Cyber RiskOps: The Engine of Decision Quality
This is where my Cyber RiskOps framework comes into play.
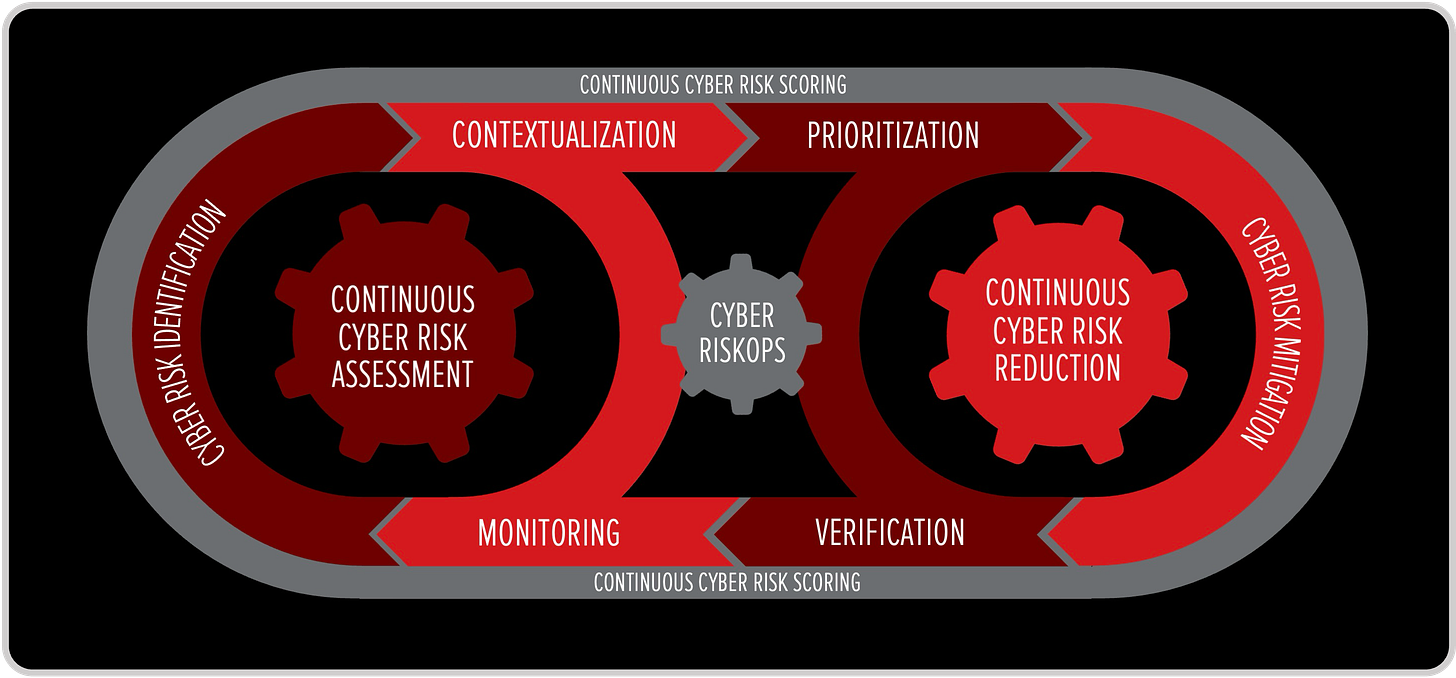
Cybersecurity leaders don’t just need cyber risk assessments or control catalogs — they need a system to connect assessment with action, and action with measurable reduction. That’s exactly what Cyber RiskOps provides: a continuous loop that transforms cyber risk insight into cyber risk reduction.
The framework has two gears in constant motion:
Continuous Cyber Risk Assessment: Identifying, contextualizing, and prioritizing risks in real time.
Continuous Cyber Risk Reduction: Ensuring that mitigations translate into measurable decreases in exposure, verified through monitoring and scoring.
At the center of this loop is decision-making.
By embedding contextualization, prioritization, monitoring, and verification into a continuous cycle, Cyber RiskOps ensures that every decision is tested against its impact on cyber risk exposure. This closes the dangerous gap between “we did something” (mitigation) and “we changed something” (reduction).
In other words: Cyber RiskOps operationalizes decision quality.
It turns strategy into an ongoing practice — where decisions are informed by continuous cyber risk scoring, validated by real reduction, and adjusted as the threat landscape evolves.
And that brings us to the final piece: how organizations can evaluate if their decision-making frameworks are truly delivering what matters most — sustained cyber resilience.
Measuring What Really Matters
Decision quality in cybersecurity can be assessed by asking:
Did this decision reduce the organization’s cyber exposure in a meaningful way?
Was the decision made with clear cyber risk–based context, rather than blind compliance or fear?
Does this decision align with our chosen cyber risk landscape and sustain resilience over time?
Can we learn from this decision, so the next one is even better?
If the answer is yes, then we’re moving in the right direction.
And if the answer is consistently yes, then decision quality is becoming the organization’s true competitive advantage.
Decisions, Not Tools, Build Cyber Resilience
Cybersecurity is not a game of perfect foresight. It’s a game of continual choices.
And the true measure of a cybersecurity leader is not how many threats they blocked yesterday — but whether their organization is making better, cyber risk–informed decisions today than it did yesterday.
Because in the end, decision quality is the most strategic metric we have.
We need to move beyond activity-based measurements — the number of alerts, the volume of logs, the tools deployed — and start evaluating whether our decisions are truly reducing cyber risk exposure. That shift is what transforms cybersecurity from a reactive cost center into a proactive enabler of resilience and strategic progress.
As I’ve seen time and again: organizations that embed decision quality into their strategy not only withstand attacks better — they also adapt faster, invest smarter, and align cybersecurity with business outcomes.
Here is my learning:
Cyber resilience isn’t built by tools alone — it’s built by the quality of decisions.
Castro, J. (2025). What Is Strategy in Cybersecurity? Rethinking the Way We Lead, Protect and Adapt. ResearchGate. https://www.researchgate.net/publication/393674625 DOI:10.13140/RG.2.2.16703.42409
Castro, J. (2024). From Definition to Action: Measuring and Managing Cyber Risk. ResearchGate. https://www.researchgate.net/publication/388653064 DOI:10.13140/RG.2.2.15858.21448
Castro, J. (2025). Cyber RiskOps: Bridging Strategy and Operations in Cybersecurity. ResearchGate. https://www.researchgate.net/publication/388194428 DOI:10.13140/RG.2.2.36216.97282/1
Castro, J. (2025). How to Turn Cyber Risk Assessments into Real Cyber Risk Reduction. ResearchGate. https://www.researchgate.net/publication/388564202 DOI:10.13140/RG.2.2.14029.76007/1
Castro, J. (2024). Cyber Risk 101: Understanding and Managing Cyber Risk. ResearchGate. https://www.researchgate.net/publication/388493450 DOI:10.13140/RG.2.2.23453.83684/1