From Showing Value to Proving Impact: Why the CISO Narrative Must Change
For years, the CISO role has been trapped in a communication problem that no tool, no AI model, and no dashboard has ever fully solved: cybersecurity keeps “showing value” but the business keeps asking for “impact.” And those are not the same thing. Many CISOs deliver incredible operational results, reducing incidents, improving detection, patching vulnerabilities faster, consolidating platforms, driving compliance, enhancing visibility. Yet, when budget season arrives, security still feels like a cost center. In many organizations, security success becomes invisible because “nothing happened,” and security effort becomes noise because executives can’t translate alerts, controls, and coverage into business outcomes. This is the central dilemma: the CISO can prove security activity all day long, but still fail to prove why the business should care. And when security only speaks in technical outputs, it becomes disconnected from the language executives use to make decisions, revenue, customer trust, productivity, continuity, brand value, operational resilience. So the real shift isn’t about better metrics; it’s about a different lens. The CISO must evolve from showing value (“we did security things”) to proving impact (“we changed business outcomes”).
That’s why, when I was reading the framework created by Jacco van der Kooij (Winning by Design), it immediately clicked for cybersecurity leadership. Not because it is about sales, but because it is about the psychology of decision making and the structure of executive conversations. Jacco starts with a blunt truth: conventional approaches focus on needs, features, and benefits, but modern buyers do not want features, they need impact. That single sentence explains much of what goes wrong when CISOs present to boards. Security leaders often communicate like “traditional sellers”: we map business needs to security controls and then list benefits. But executives don’t buy controls; they fund outcomes. They don’t invest in SIEM because SIEM is impressive. They invest because they believe it will reduce cyber risk exposure, prevent downtime, protect brand value, and accelerate confident decision-making. In other words: impact is the real product, and security leaders has to learn to sell impact internally.
The Impact Framework: Impact Is an Onion, Not a Banana
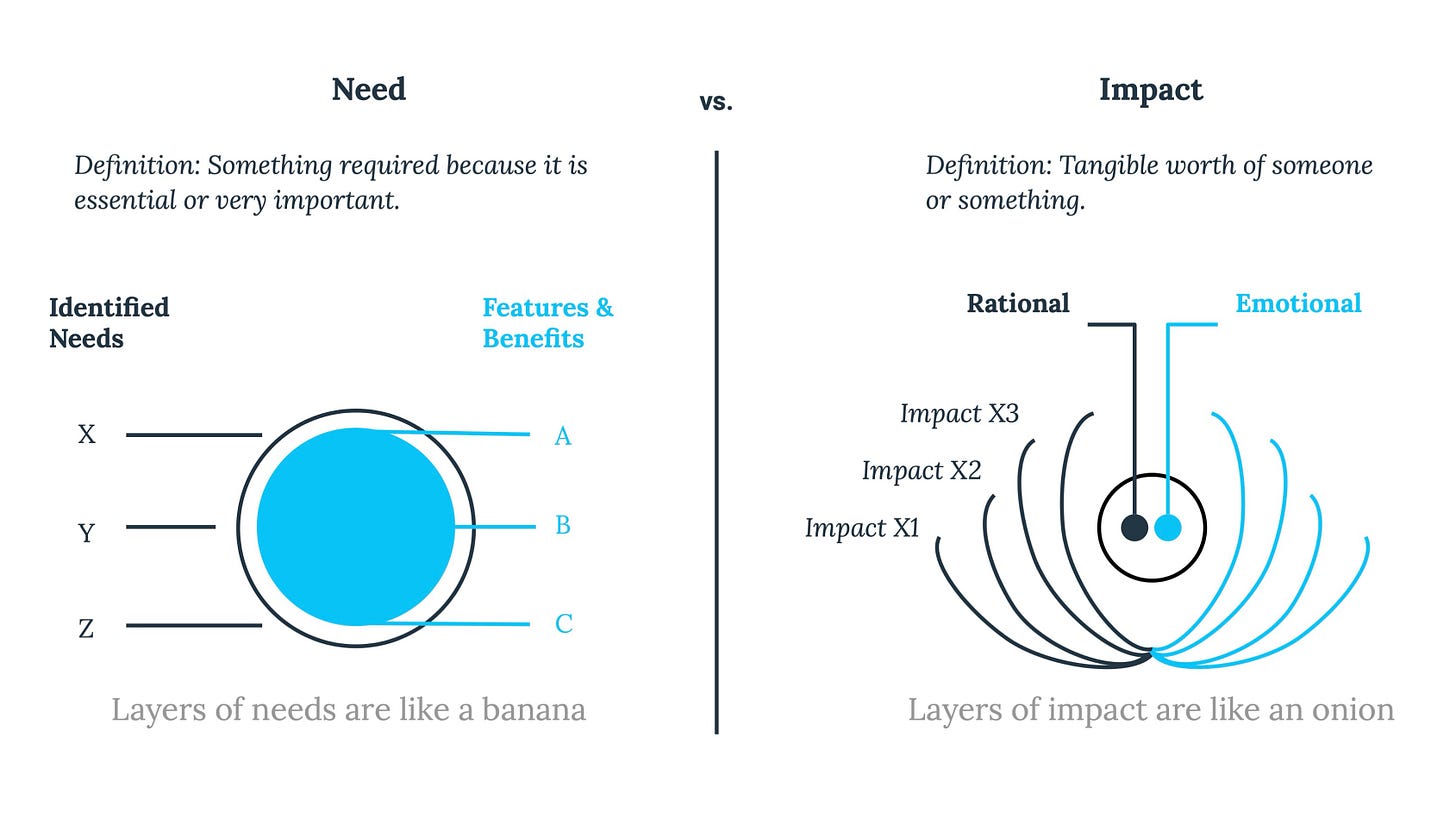
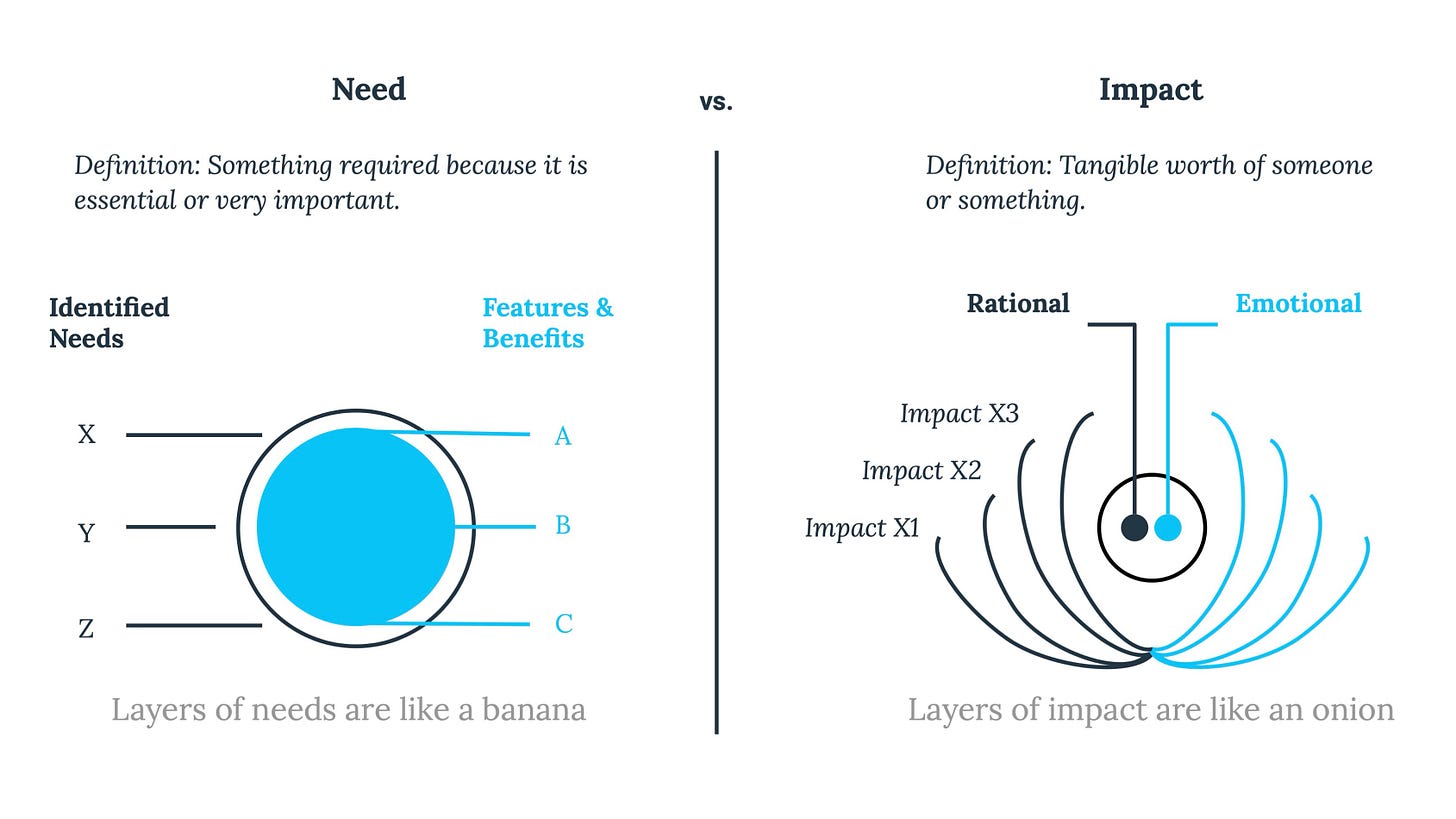
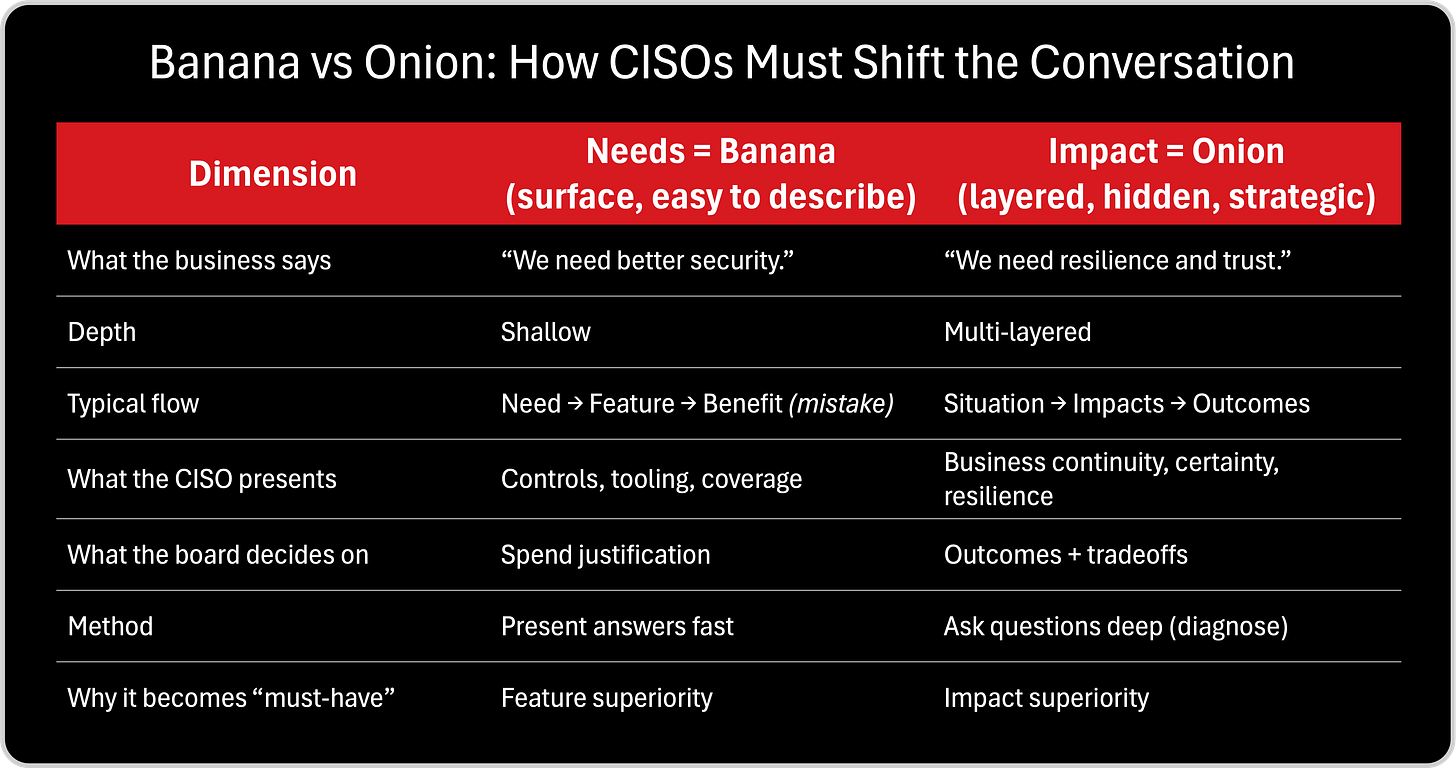
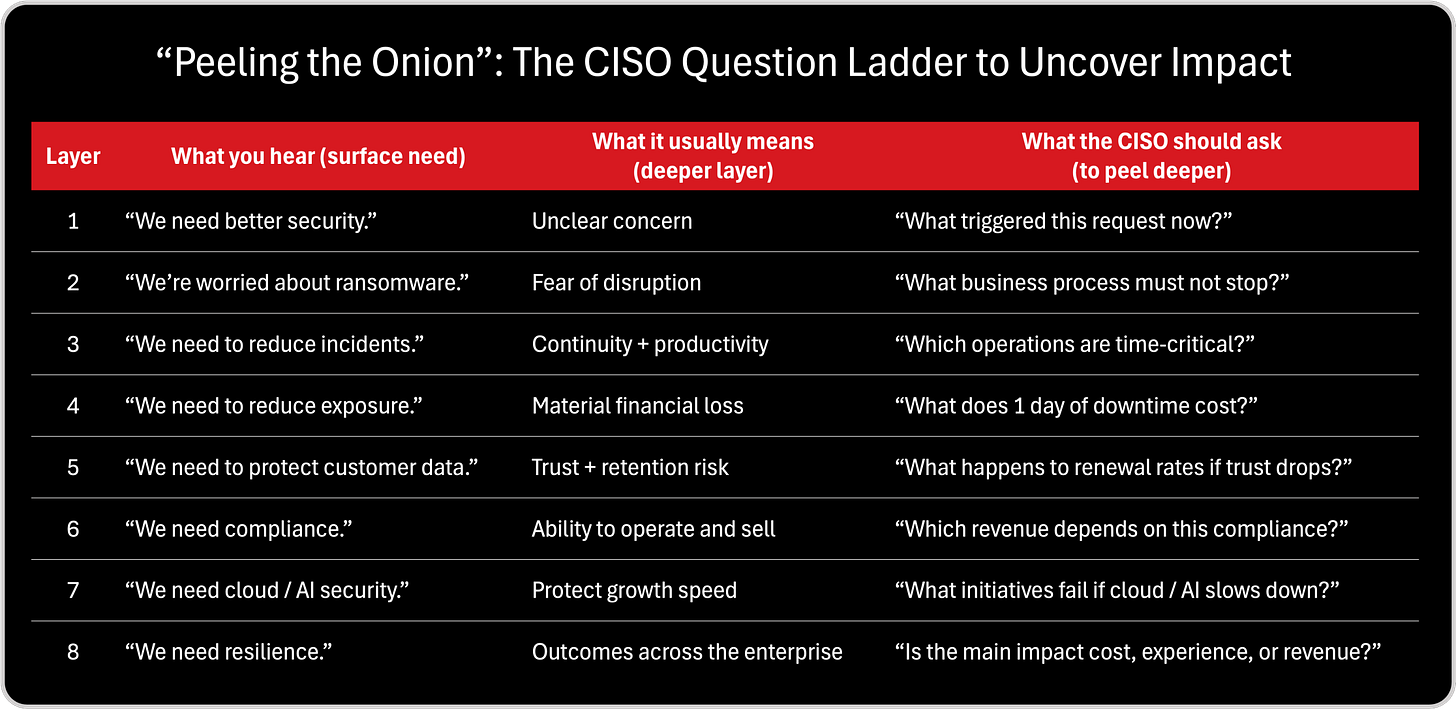
When I was reading Jacco’s framework, one metaphor immediately stuck with me because it describes the CISO communication gap better than any security dashboard ever could. Jacco explains that “needs” are like a banana: visible, simple, and easy to describe. But “impact” is like an onion: layered, deep, and often hidden beneath multiple layers that must be peeled back by asking better questions. And this is exactly what happens in cybersecurity. Executives often express a surface need, “we need ransomware protection,” “we need compliance,” “we need better visibility”, but what they are truly buying is not a tool or a control. They are buying continuity, trust, resilience, decision speed, and protection of strategic initiatives. That’s why I believe the modern CISO must stop presenting solutions too early and instead learn to peel the onion first, because impact is what transforms security from a cost conversation into a business conversation. The following two tables operationalize this model for CISOs: first, a simple side by side view of “banana vs onion“Peeling the Onion”: The CISO Question Ladder to Uncover Impact,” and second, a practical “question ladder” that helps translate surface security needs into executive-level impact.
The framework also gives CISOs another critical insight: impact has two dimensions: rational and emotional. Emotional impact includes things like peace of mind, while rational impact is measurable through savings and results. Most CISOs are trained to communicate rationally: numbers, charts, KPIs. But boards are human systems, not mathematical systems. And the Impact Framework highlights something that explains countless failed executive security presentations: people tend to make emotional decisions first, and only validate later with facts and figures. Cybersecurity leaders often walk in with metrics expecting that logic will create urgency. But urgency rarely comes from logic. Urgency comes from fear of loss, fear of disruption, fear of reputational damage, fear of regulatory consequences, fear of being the next headline. Those are emotional impacts. So the modern CISO must build narratives that trigger the right emotional understanding (without manipulation), and then back it up with rational proof. This is why cybersecurity impact storytelling is now a leadership skill, not a nice to have communication trick.
Translating Security Programs into Cost, Experience, and Revenue
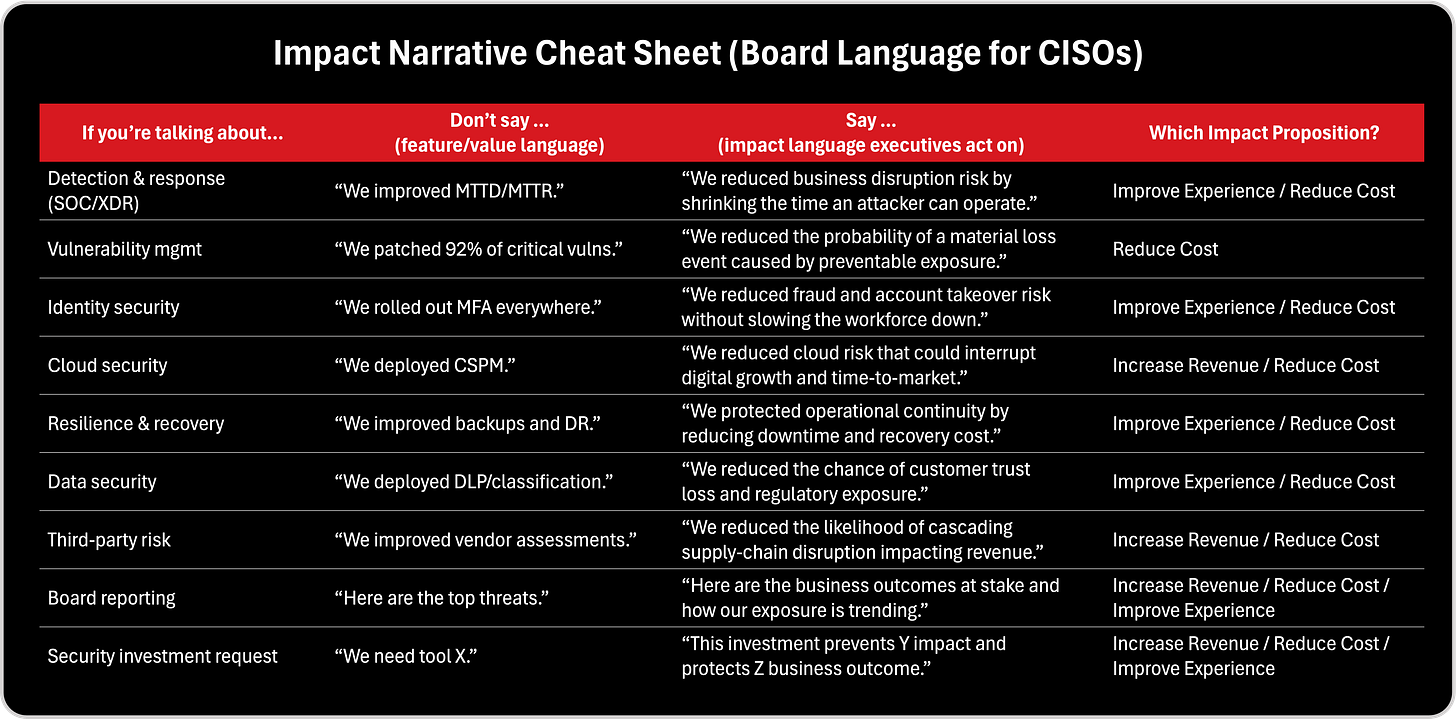
One of the most practical tools in Jacco’s blueprint is the definition of three high level impact propositions: reduce cost, improve experience, and increase revenue. This is the perfect executive translation layer for a CISO. Because every security initiative, if it matters, must map into at least one of these outcomes.
Reducing cost in cybersecurity is often misunderstood. It’s not “saving money on tools.” It is reducing the total cost of risk and operational disruption. That means: preventing incidents that trigger unplanned financial losses; lowering breach exposure; reducing regulatory penalties; reducing fraud; reducing downtime; and lowering the burden of manual operations. A CISO can translate a program like detection engineering, SOC modernization, incident response readiness, and posture management into cost reduction by calculating avoided losses, reduced incident frequency, reduced mean time to contain, and reduced disruption costs. The metric isn’t “how many alerts we closed.” The metric is “how much loss we prevented and how much operational waste we eliminated.”
Improving experience may be the most underestimated cybersecurity impact. Experience isn’t only customer experience, it includes employee experience, partner experience, and operational experience. Security that introduces friction slows the business down. Security that improves experience accelerates operations. That includes faster provisioning, smoother identity flows, fewer authentication disruptions, fewer outages, faster response, less downtime, safer innovation, and increased confidence to launch digital programs. Jacco’s model even gives examples like “two clicks vs. eight clicks” to show that experience can be designed and measured. In a security context, “experience impact” might be: reducing false positives so teams stop wasting time; shortening investigations; enabling faster deployments; creating better resilience so outages don’t happen; and building trusted digital services that customers rely on.
Increasing revenue is the advanced CISO narrative, and the one that separates technical CISOs from business CISOs. Many security leaders avoid this because it feels indirect. But the truth is: security is often a revenue enabler. It enables regulated deals. It reduces friction in procurement. It increases trust, which improves retention. It protects brand, which protects market value. It reduces time to market risk for digital products. It unlocks new markets that require certifications and assurance. Jacco’s framework explicitly lists increasing revenue as one of the three core impact propositions, and once a CISO adopts that lens, security becomes part of the growth strategy rather than a tax on growth.
Why Impact Requires Speed (and Why I Connect This to Decision Effectiveness)
While I was reflecting on the Impact Framework, one thing became clear: the shift from value to impact is not just a communication upgrade, it is also an operational race. Jacco explains that impact is layered like an onion, and that it is often hidden many layers deep, requiring leaders to go “many questions deep” to uncover what the business truly cares about. But in cybersecurity, we operate in an adversarial environment where time is never neutral. That’s why I believe impact must also be tied to tempo. It is not enough to identify impact; the organization must be able to act on impact fast enough to prevent the attacker from turning time into advantage. Otherwise, the board may agree with the business case, the strategy may be correct, and the program may be justified, but the decision arrives after the window of influence closes.
This is exactly why I wrote about the concept in my article “Attackers Only Need to Be Faster Than Our Decision Making Process.” In that article, I argue that cyber adversaries don’t need to outsmart us, they only need to move faster than we decide. Attackers operate with speed, automation, and momentum, while defenders often slow themselves down with analysis, validation, escalation paths, and governance loops. The result is a structural imbalance: even a correct decision can become ineffective if it is made too late. That’s the core reason CISOs cannot only “show value” anymore. Value metrics, controls deployed, detections improved, patching percentages, do not automatically translate into impact if timing is lost. Impact is only real when it changes outcomes before time switches sides.
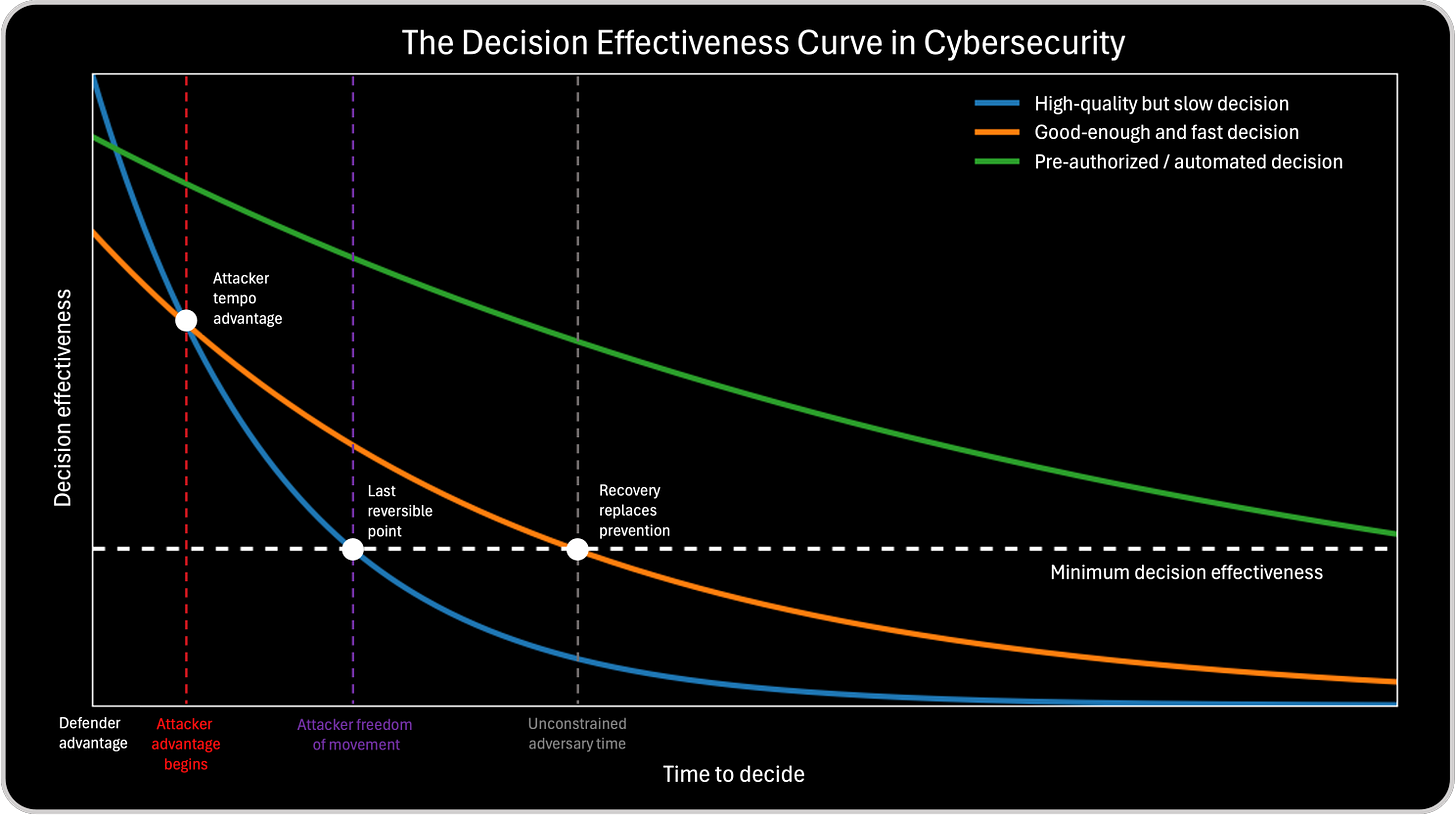
To make that visible, I introduced the Decision Effectiveness Curve, which shows that decision effectiveness decays as time to decide increases, even if decision quality improves. In other words: cybersecurity is not only about making good decisions, it is about making decisions while they still matter. That’s why “impact” becomes the correct executive language for CISOs: it forces us to discuss outcomes, not activity. But to truly operationalize impact, CISOs must also address decision velocity—because attacker advantage often emerges as a tempo problem, long before it becomes a breach.
And this is where the connection becomes powerful: Jacco’s onion framework teaches CISOs how to uncover what matters to the business, while the Decision Effectiveness Curve explains how fast we must act once we know what matters. Together, they create a leadership-level model: Discover impact (onion), then execute impact at speed (tempo control). That is the difference between a security program that looks good on slides, and a security operating model that actually prevents loss.
The CISO Board Update Template (Impact First)
To operationalize this, the CISO needs a repeatable structure for board communication. The goal is to stop presenting “security work” and start presenting “business outcomes.” The Winning by Design blueprint also shows that impact matters from start to finish, across the whole lifecycle, from discover impact to grow impact. That means CISOs should not only present controls implemented; they should present impact realized.
A simple template looks like this: First, define the business outcome at stake (impact). Second, show what changed since last quarter (movement). Third, show proof (evidence). Fourth, state the next risk decision required (action). For example: “Impact: protect operational continuity in X revenue stream.” “Movement: reduced exposure by Y due to segmentation + improved detection.” “Proof: reduced dwell time, fewer high-severity exposures, faster containment, fewer business disruptions.” “Decision: invest in resilience in this part of the value chain, because it provides the highest protection-per-dollar.” This structure forces the conversation into governance and business choice, which is where boards operate
And this is where the emotional + rational impact structure becomes critical. The board must feel the risk to act, and must trust the rational proof to fund the solution. Jacco highlights that emotional impact supersedes rational impact because of how humans decide. So the CISO update must include both: emotional clarity (“this is what could happen to the business”), and rational evidence (“this is why we know we’re reducing the risk”). Together, this makes cybersecurity not only fundable, but governable.
The CISO’s New Reality: Impact Is a Lifecycle, and Every C-Level Executive Has a Different Journey
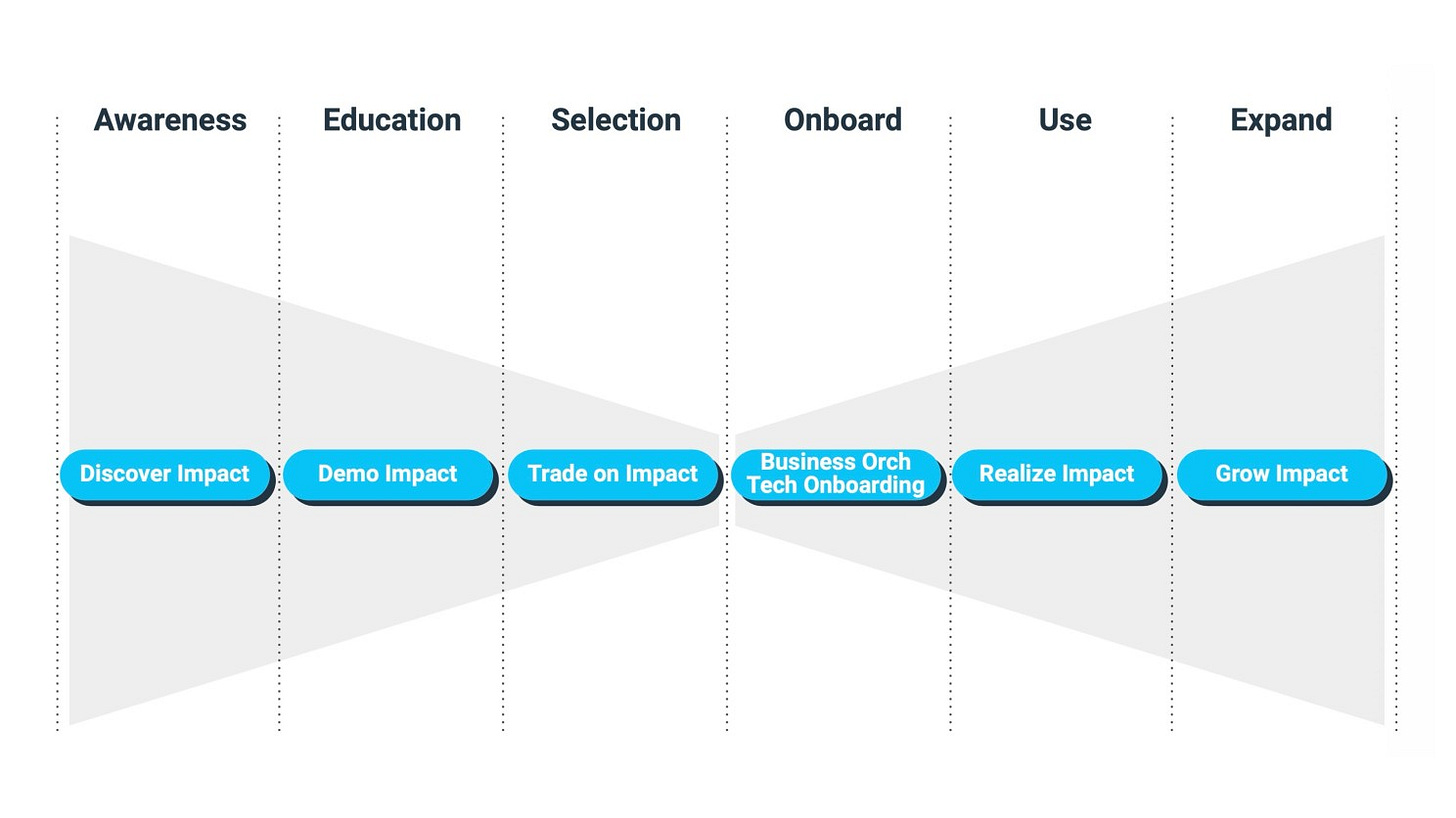
One diagram in The Impact Framework is especially relevant for CISOs because it captures something that security leaders feel every day but rarely name explicitly: impact is not a moment, it is a lifecycle. The model maps the business journey Awareness → Education → Selection → Onboard → Use → Expand and pairs it with the impact journey Discover Impact → Demo Impact → Trade on Impact → Tech Onboarding → Realize Impact → Grow Impact. This is critical because cybersecurity often does the opposite: it treats impact like a pitch. We spend massive effort proving features and benefits up to “selection” and “onboard,” and then we assume impact will naturally materialize. It doesn’t. If impact isn’t engineered through adoption, measurement, and operational execution, security becomes stuck in “value reporting” forever, counting alerts, counting vulnerabilities, counting controls, while executives keep asking the only question that matters: what changed in the business? The Impact Lifecycle diagram makes the answer unavoidable: if the CISO cannot connect security outcomes to realized impact during Use, and cannot scale those outcomes into Expand, then the program never escapes the gravity of being a cost center.
But there is another layer in that diagram that is often overlooked, and it matters enormously for board communication. This lifecycle also reveals that each C-level executive experiences a different impact journey, even if they are looking at the same security program. The phases are the same, but the entry point, the concerns, and the proof required are different. A CEO’s impact journey usually starts in Discover and Trade on Impact, because CEOs care about enterprise outcomes: strategic risk, market confidence, reputational exposure, and growth enablement. They need clarity on what could break the company and what could stall the strategy, so impact needs to be framed emotionally first—trust, continuity, brand, confidence, then validated rationally, because human beings tend to decide emotionally and validate later with facts. A CFO’s journey is different: it is anchored in Reduce COST, loss exposure, unplanned spend, margin pressure, insurance economics, and risk-to-cashflow. CFOs don’t want a list of controls; they want a view of expected loss, cost of downtime, and investment tradeoffs. A COO’s journey is operational: the COO lives in Onboard → Use → Realize Impact, because operational leaders don’t debate whether security matters, they need to know whether security prevents disruption and makes execution more stable. Their language is resilience, uptime, productivity, and predictable operations. Meanwhile, a CIO or Chief Digital Officer experiences impact through transformation speed: cloud adoption, modernization, and delivery of digital services without friction. Their focus sits between Tech Onboarding and Realize Impact, because the question is not only “is it secure?” but “does security accelerate or slow our ability to ship?”
And this is where the CRO becomes central, because the CRO is the executive most aligned to impact as a structured discipline. The CRO’s journey starts at Discover Impact but they will push hard toward Realize and Grow, because risk leadership is not satisfied with “we deployed controls”; they want measurable exposure reduction and governance-grade assurance. The CRO thinks in risk appetite, thresholds, systemic correlation, and enterprise resilience. They want to know whether cybersecurity risk is being managed like all other enterprise risks: continuously monitored, continuously reduced, and linked to business objectives. For the CRO, “impact” is not just reduction of incidents; it is reduction of uncertainty and improvement of decision integrity at executive level. In other words: the CRO is often the executive who can help a CISO move cybersecurity from a technical domain into an enterprise operating model—because they understand that the organization must be able to trade risk intelligently, not just deploy controls.
This is also where my own work on decision speed becomes tightly connected to The Impact Framework Journey. In my article “Attackers Only Need to Be Faster Than Our Decision Making Process,” I argue that cyber adversaries don’t need superior capability, they only need to move faster than defenders decide. That creates a dangerous reality: even if the CISO correctly discovers the impacts and sells the program internally, the organization can still lose if its decision-making lifecycle is slower than the attacker’s tempo. So when a CISO uses Jacco’s lifecycle model, the real outcome is bigger than communication: it becomes an execution mandate. The purpose of CISO impact management is to ensure that impact is not only defined and sold during selection, but operationalized so deeply during use that decisions can be executed quickly, consistently, and at scale. That is what moves cybersecurity from “showing value” to “proving impact.” It’s not just about a better story. It’s about the organization being able to act on what matters, before time switches sides.
The New CISO Standard Is IMPACT
The modern CISO cannot win long term by reporting activity. Activity is always debatable. It’s easy to ignore, easy to downplay, and too often it sounds like cost. Impact is different. Impact is what boards are accountable for. Impact is what executives will fund. Impact is what business leaders can prioritize because it connects directly to outcomes: continuity, trust, resilience, and growth. That’s why the Impact Framework is so relevant for cybersecurity leadership: it makes clear that the old story is broken. CISOs must stop selling features, stop leading with needs, and stop assuming metrics will speak for themselves. Instead, we must diagnose the situation, peel the onion, uncover what is truly at stake, and translate cybersecurity into the language of business impact, reducing cost, improving experience, and enabling revenue.
But impact is not only a message, it is a lifecycle. The framework shows that impact must be managed end-to-end: discover, demonstrate, trade, onboard, realize, and grow. This is where the CISO evolution becomes real: not when security “deploys tools,” but when security proves measurable business outcomes in the Use phase and scales them into Expand. And in cyber risk, that lifecycle has a hidden constraint: time. As I mentioned before adversaries don’t need to outsmart us, they only need to move faster than we decide. So the new CISO standard is not only to prove impact, but to operationalize impact at speed, turning signals into decisions and decisions into action before time switches sides. That is how CISOs evolve from security operators into business leaders, and how security stops being treated like a department and starts being recognized as a business
Van Der Kooij, J. (2022). https://winningbydesign.com/resources/blog/emotional-versus-rational-impact/ https://winningbydesign.com/resources/blueprints/emotional-vs-rational-impact/
Castro, J. (2025). Attackers Only Need to Be Faster Than Our Decision Making Process. ResearchGate. https://www.researchgate.net/publication/398971490 DOI:10.13140/RG.2.2.14817.98404