Cybersecurity Paralysis, When the Cyber Brain of the Organization Breaks
After many years of being a professor at the university, I learned that the best way to explain complex, abstract ideas is through analogies. When we translate something technical into something human, something conceptual into something familiar, understanding accelerates. Cybersecurity is no exception. And recently, I have found that the most revealing analogy is not technological at all, but biological. For years, cybersecurity has been framed as a problem of tools, telemetry, and technology, but the more closely we observe how organizations behave under pressure, the clearer it becomes that many of the failures we attribute to complexity or lack of resources are actually neurological failures. Not biological ones, but structural ones. Failures in how the organization thinks, interprets, communicates, and reacts. The same patterns we see in the human brain under stress, overload, and trauma appear repeatedly in companies struggling to defend themselves. Alert fatigue mirrors cognitive exhaustion, slow decision making mirrors disrupted instinct, executive blind spots mirror emotional disconnection, and the inability to act in critical moments mirrors the breakdown of reflex pathways. When we map cybersecurity to the architecture of the human brain, a powerful analogy emerges, one that explains why so many organizations think one thing, report another, and react far too late. Cybersecurity paralysis is not merely a technical problem, it is the collapse of an organizational mind that can no longer align its intelligence, its context, and its instinct. And just like in human cognition, when the layers of the cyber brain fall out of sync, everything slows, everything confuses, and everything becomes vulnerable.
Why the Human Brain Became My Compass for Cybersecurity
I have always been passionate and curious about how the human brain makes decisions, how it evolved, and why it remains the most extraordinary adaptive system on the planet. The more I learned about neuroscience, the more I realized that what separates humans from other species is not simply intelligence, but the delicate interplay between intelligence, emotion, and instinct. Other species may have sharper senses or faster reflexes, but humans developed a brain capable of aligning long term reasoning with emotional meaning and immediate protective action. This tri layer architecture is what allowed our species to innovate, collaborate, anticipate danger, and adapt to environments far more complex than those faced by any other animal.
A central question that always fascinated me is how we think, speak, and act in ways that feel coherent, and why sometimes those three layers fall completely out of sync. There are moments when we think one thing, say another, and act in a way that contradicts both, revealing that our internal architecture is far more layered and complex than we consciously perceive. The classical model that divides the brain into the neocortex, the limbic system, and the reptilian brain helps explain this tension. The neocortex is the rational and analytical layer, the part that evaluates information, reasons through complexity, and constructs logic. The limbic brain governs emotion, intuition, motivation, and social connection, shaping how we value things, what we fear, and what we choose to prioritize. The reptilian brain is the instinctive core, the ancient survival system that reacts instantly to threat, long before our rational mind catches up. These three layers coexist, influence one another, and sometimes conflict, but together they form the architecture that allowed humanity to evolve, innovate, and survive.
What struck me is how closely this biological structure reflects the way cybersecurity should function, yet rarely does. In many organizations, the analytical layer, the neocortex, is overloaded with alerts and data. The limbic layer, the business context and communication system, is disconnected from decision makers and unable to convey risk in a meaningful way. And the reptilian layer, the instinctive and protective reflexes that should respond instantly to danger, is either constrained by process or missing entirely. Just as misalignment in the human brain creates confusion, hesitation, or contradictory behavior, misalignment in the cyber brain creates paralysis. The organization thinks one thing, reports another, and reacts far too late.
The human brain became the perfect analogy for modern cybersecurity because it shows us what defense looks like when thinking, feeling, and acting are aligned, and what failure looks like when they are not. It teaches us that intelligence alone is insufficient, that instinct must be active, that context must be translated, and that resilience comes from integration rather than accumulation. Just as humanity evolved through the coordination of cognition, emotion, and reflex, cybersecurity must evolve through the coordination of analytics, risk, and real time response. Tools alone will not solve the problem. What we need is a cyber brain capable of coherence.
The Cyber Brain, A New Model for Understanding Organizational Defense
The idea of the Cyber Brain emerges from a simple but powerful realization: organizations behave like biological systems. They think, interpret, and react through layers of cognition that mirror the architecture of the human brain. After years of observing how companies struggle to defend themselves, I began to see the same patterns of overload, emotional disconnect, and instinctive paralysis that appear in humans under stress. The analogy is not superficial, it is structural.
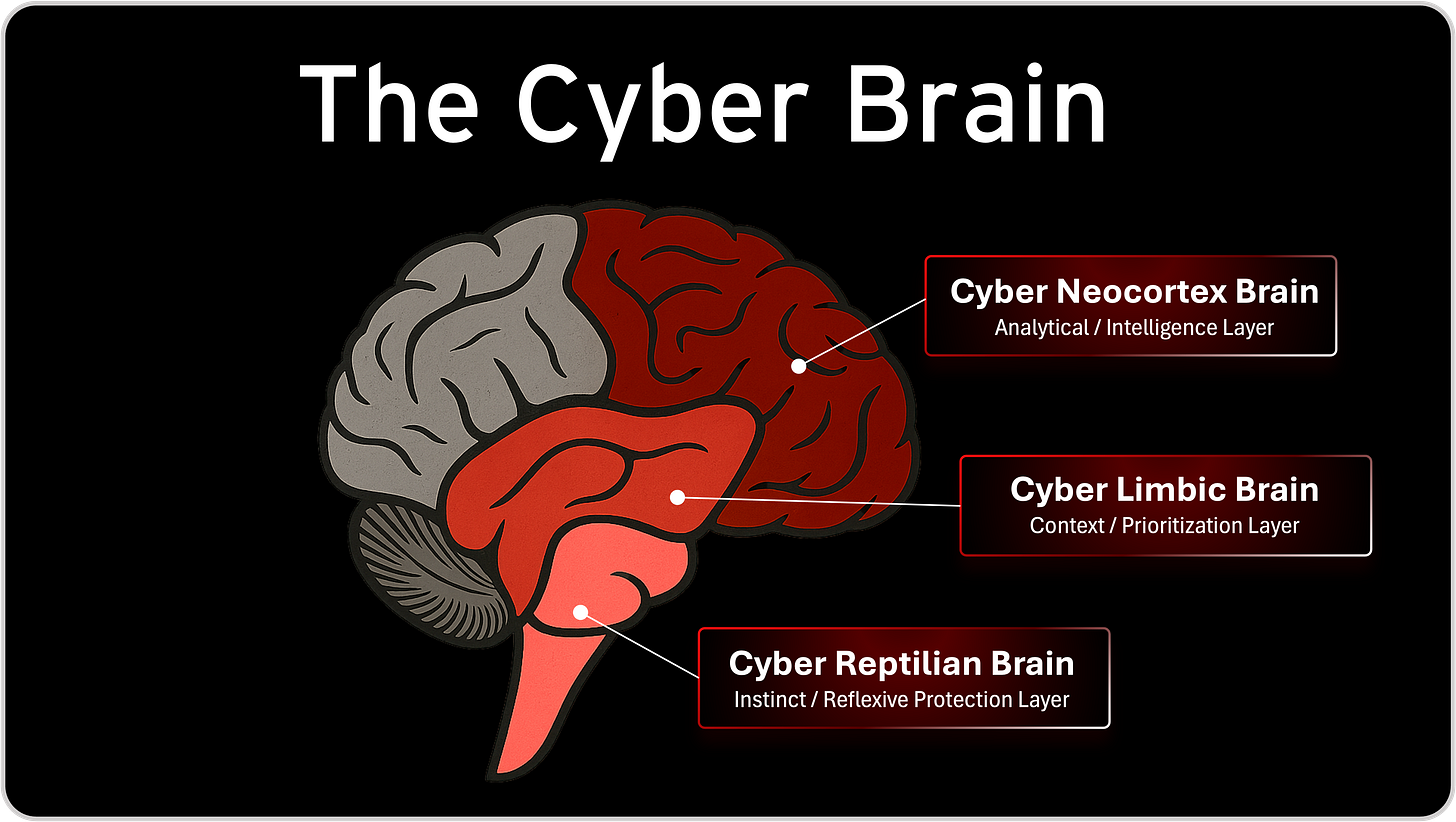
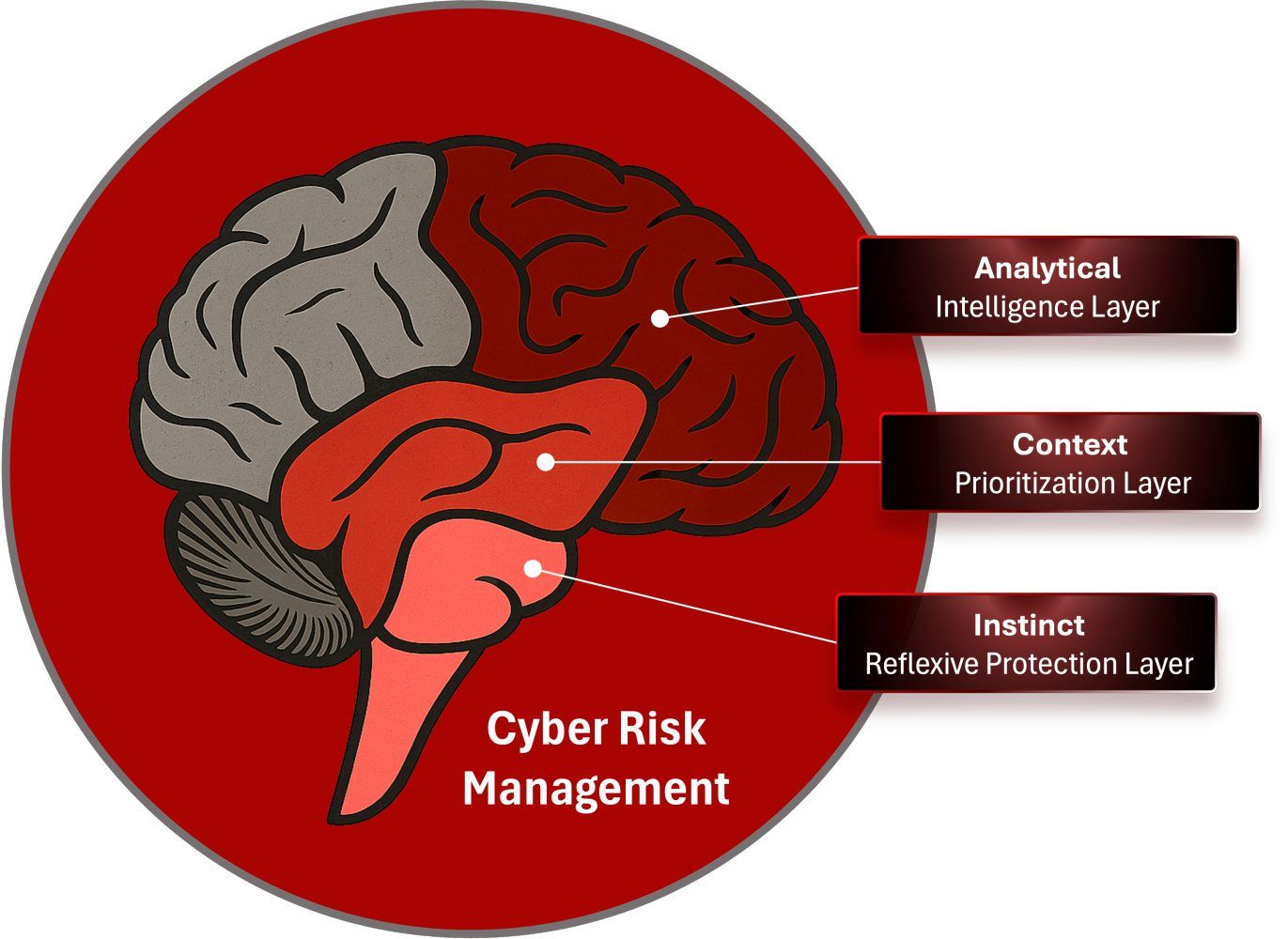
The Cyber Brain is composed of three interdependent layers. Each one maps to a different part of the human brain, and each one mirrors a different function within the organization.
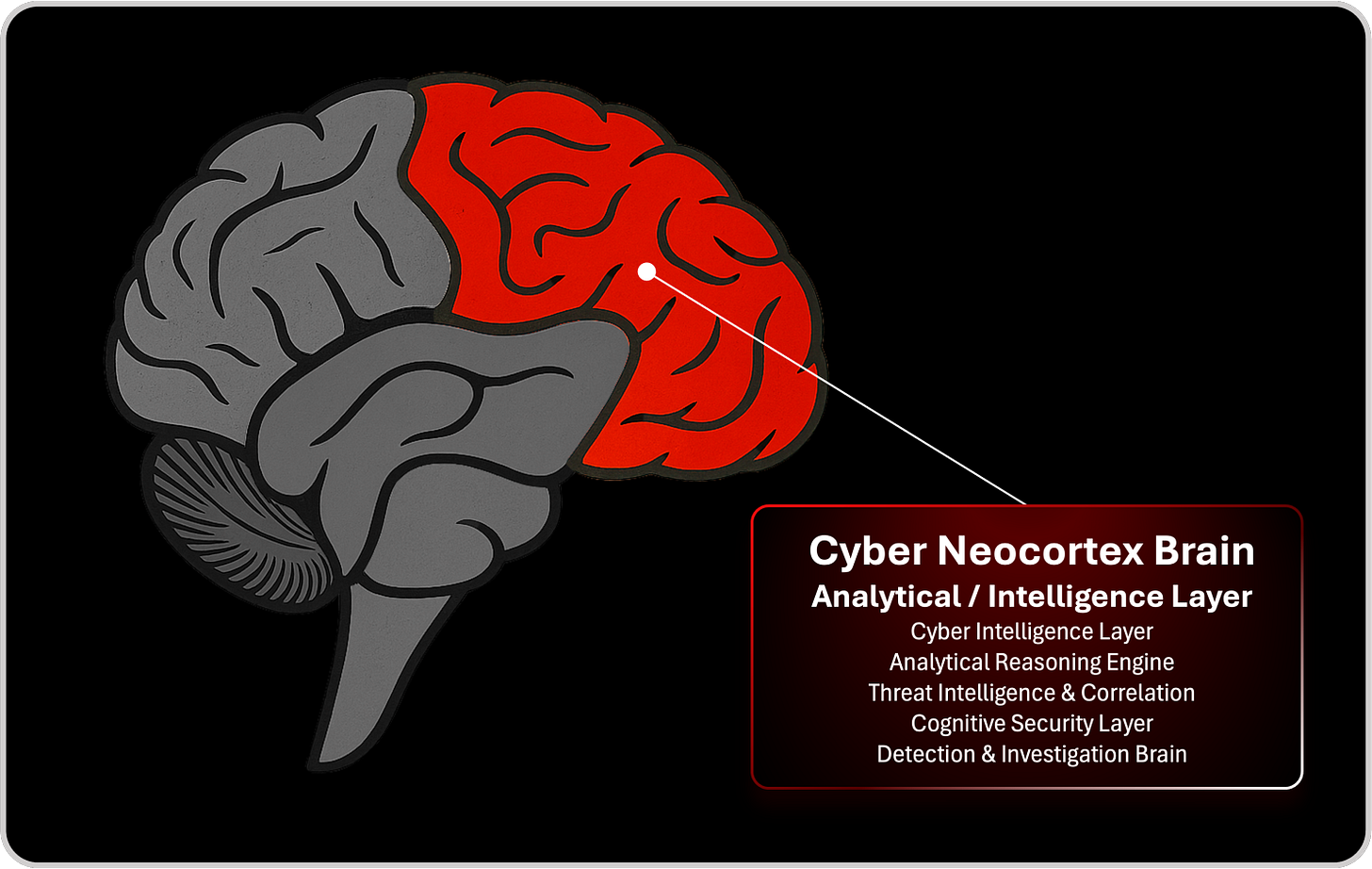
The Cyber Neocortex Brain, the analytical and intelligence layer, is where data is processed, signals are analyzed, and complex reasoning occurs. This is where threat intelligence, telemetry analysis, detection engineering, and investigations live. It is powerful, but also fragile, because like the human neocortex, it becomes overwhelmed when exposed to too much noise or too many competing inputs. Alert fatigue, investigation backlog, and dashboard overload are symptoms of a neocortex that has exceeded its cognitive bandwidth.
Cyber Intelligence Layer
Analytical Reasoning Engine
Threat Intelligence & Correlation
Cognitive Security Layer
Detection & Investigation Brain
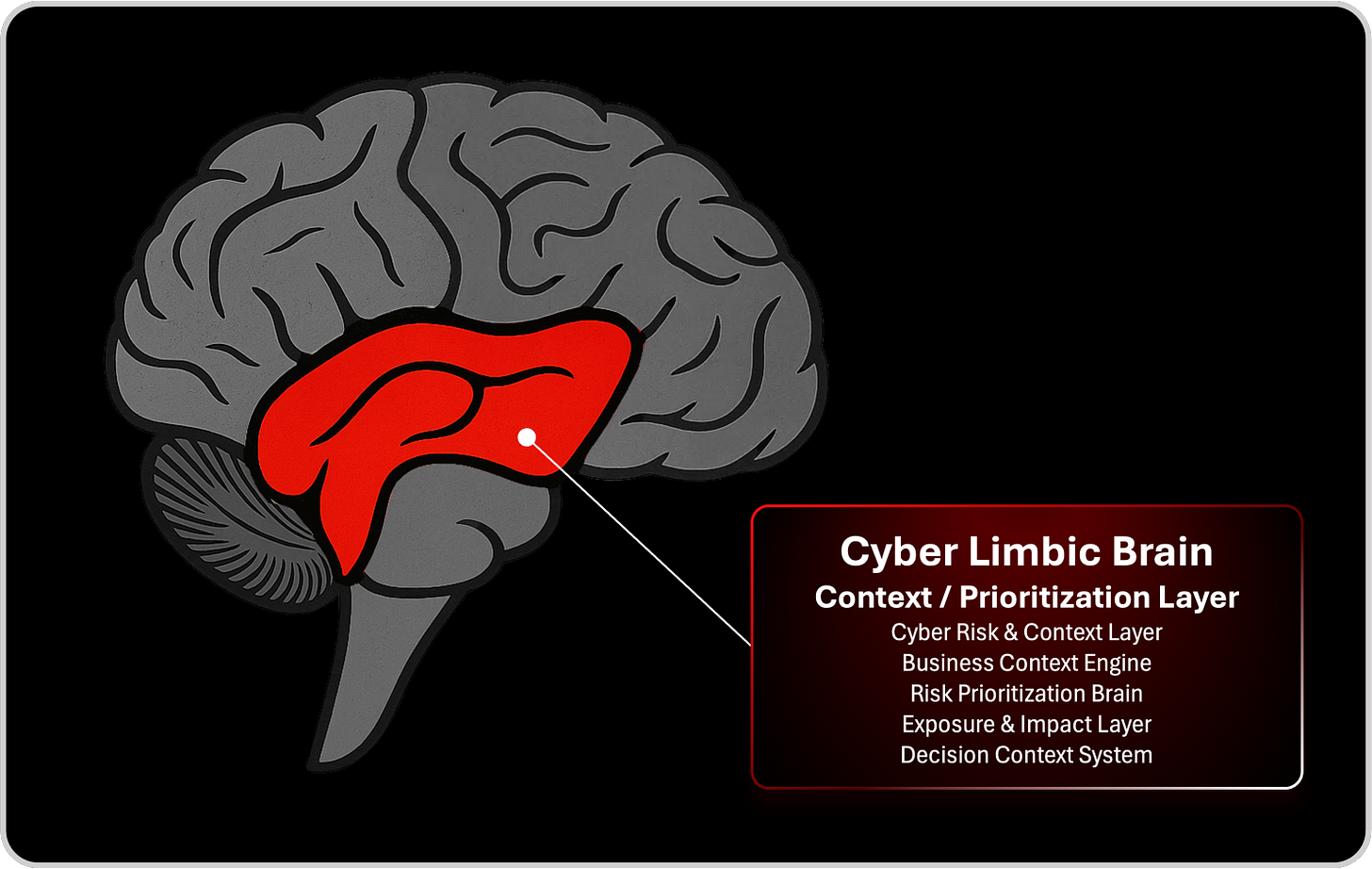
The Cyber Limbic Brain, the context and prioritization layer, gives meaning to everything the neocortex perceives. It is the emotional and interpretive center of the organization, the place where signals become risk, where risk becomes business impact, and where business impact becomes executive decisions. This is where cyber risk management plays its critical role. Without the limbic system translating technical signals into business meaning, leadership becomes blind and technical teams become misunderstood. The result is misalignment, confusion, and a widening gap between the boardroom and the SOC.
Cyber Risk & Context Layer
Business Context Engine
Risk Prioritization Brain
Exposure & Impact Layer
Decision Context System
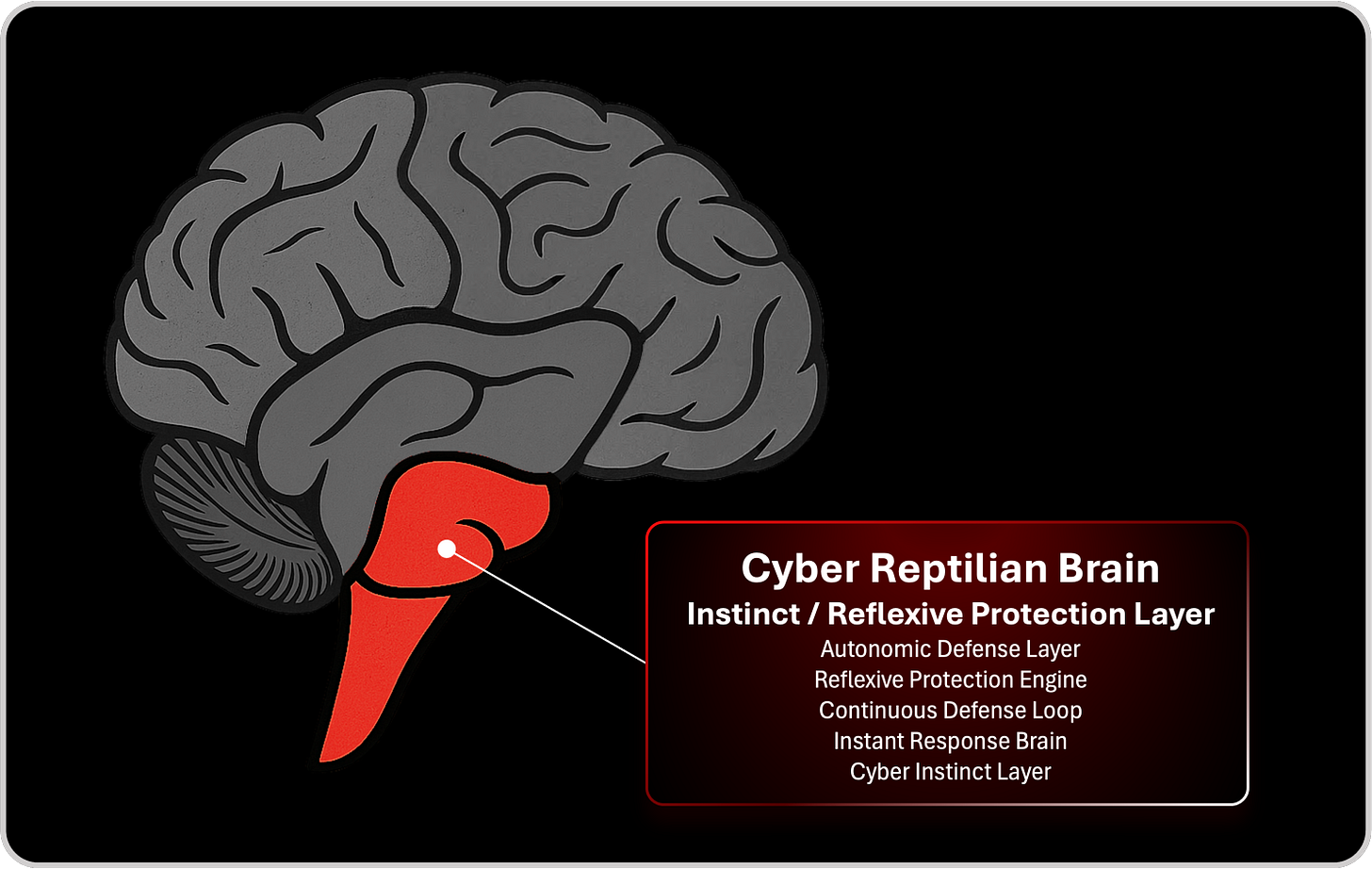
The Cyber Reptilian Brain, the instinctive and reflexive protection layer, is the foundation of survival. In cybersecurity, this is the domain of automated protection, containment, autonomous response, and the continuous defense loop. It is the only layer capable of acting in milliseconds, protecting the organization when analysis is too slow and governance is too distant. When this layer is underdeveloped, disconnected, or overly dependent on human approval, the organization becomes reactive and slow, unable to respond at the speed of adversaries.
Autonomic Defense Layer
Reflexive Protection Engine
Continuous Defense Loop
Instant Response Brain
Cyber Instinct Layer
These three layers form the Cyber Brain. When they work in harmony, when intelligence is clear, context is shared, and instinct is active the organization becomes coherent, adaptive, and resilient. But when they drift apart, paralysis emerges. The neocortex drowns in alerts, the limbic layer fails to communicate meaning, and the reptilian core cannot act when it matters most. That fragmentation is the root cause of most modern breaches, not the absence of technology but the breakdown of internal cognition.
Understanding the Cyber Brain offers a new framework for modern defense. It explains why cyber risk management must become the central integrator, why automation must extend beyond detection, and why intelligence must be filtered, contextualized, and prioritized. Above all, it shows that cybersecurity is not just a technical discipline,it is a cognitive one. To protect the organization, we must rebuild the coherence of its mind.
The Defender Brain vs the Attacker Brain
The difference between defenders and attackers is not only technical, it is cognitive. The defender brain exists inside an organization, shaped by structure, process, governance, accountability, and resource constraints. The attacker brain exists outside those boundaries, shaped by intent, opportunity, and speed. This difference creates a neurological asymmetry that explains why cybercriminals consistently move faster, adapt sooner, and exploit the smallest hesitation in corporate environments.
Cyber adversaries behave like highly fluid and decentralized networks. They move quickly, automate aggressively, and adapt instantly. They do not need to be perfect, they only need to be faster than our decision making. They continuously probe for weaknesses, exploit ambiguity, and react to defensive changes in real time. During more than a decade of collaboration with INTERPOL, I learned one of the most important truths about cybersecurity: criminals operate without hierarchy, without bureaucracy, and without the internal friction that shapes legitimate organizations. They behave like an organism driven by instinct and opportunity. Their learning cycles are immediate, they adjust tactics the moment something succeeds or fails, and they communicate and collaborate with a speed that no regulated environment can match.
This stands in stark contrast to the defender brain. The analytical neocortex of the organization is overwhelmed by alerts, telemetry, dashboards, and signals that require structured investigation. Every action must be documented and justified. Every defensive change requires approvals, coordination, and alignment. Leadership asks for clarity and certainty, yet the analysts providing information operate in ambiguity. This creates cognitive drag. Defenders think slowly, not because they lack skill, but because their environment forces them to evaluate, validate, and communicate before they can act. The defender brain becomes thoughtful but hesitant, intelligent but overloaded, aware but constrained by its own structure.
Meanwhile, the attacker brain is free to think and act as one unified system. The limbic layer of the criminal ecosystem is driven by motivation, reward, pressure, and opportunity. Their emotional drivers are clear. Profit. Impact. Disruption. Their coordination is effortless because they share common incentives and face no political or organizational constraints. Their reptilian layer, the instinctive core of their operations, is always active. They test, pivot, react, and exploit without waiting for permission. Automation and AI amplify their reflexes, turning instinct into machinery, creating speed that defenders cannot match through analysis alone.
This neurological imbalance explains why attackers consistently outpace defenders, even when defenders have more resources, more tooling, and more intelligence. The defender brain must align analysis with governance and action with business context. The attacker brain aligns everything with opportunity. Defenders must justify their actions. Attackers simply act. Defenders must protect everything. Attackers only need one crack. Defenders must maintain stability. Attackers thrive in chaos.
Below are the three layers of the cyber brain (attacker vs defender) broken down to illustrate this asymmetry more clearly:
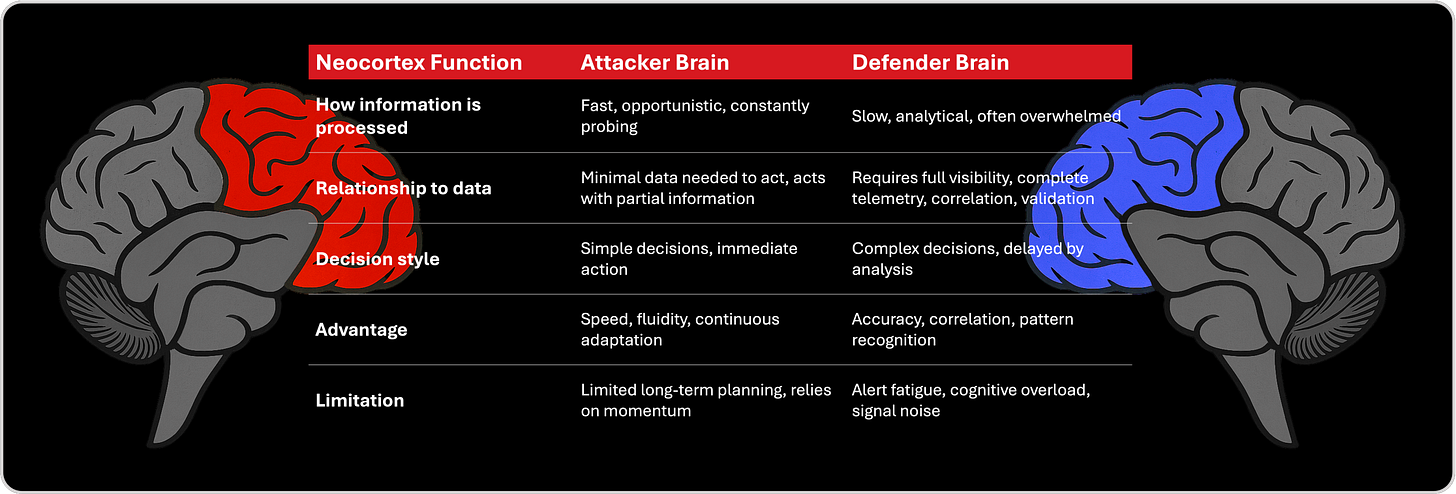
1. Neocortex Layer - Analytical / Intelligence Layer
The neocortex is the analytical engine of both the human brain and the cybersecurity ecosystem. It is the layer responsible for reasoning, analysis, interpretation, and decision making. In security operations, this is where telemetry is processed, anomalies investigated, and conclusions formed. It is powerful, but also vulnerable, because its strength depends on clarity, focus, and manageable cognitive load. When overwhelmed with noise, dashboards, and alerts, the defender’s neocortex becomes slow, hesitant, and saturated, while the attacker’s neocortex thrives under minimal data and simple decision loops. This is where the first deep asymmetry between attacker and defender begins.
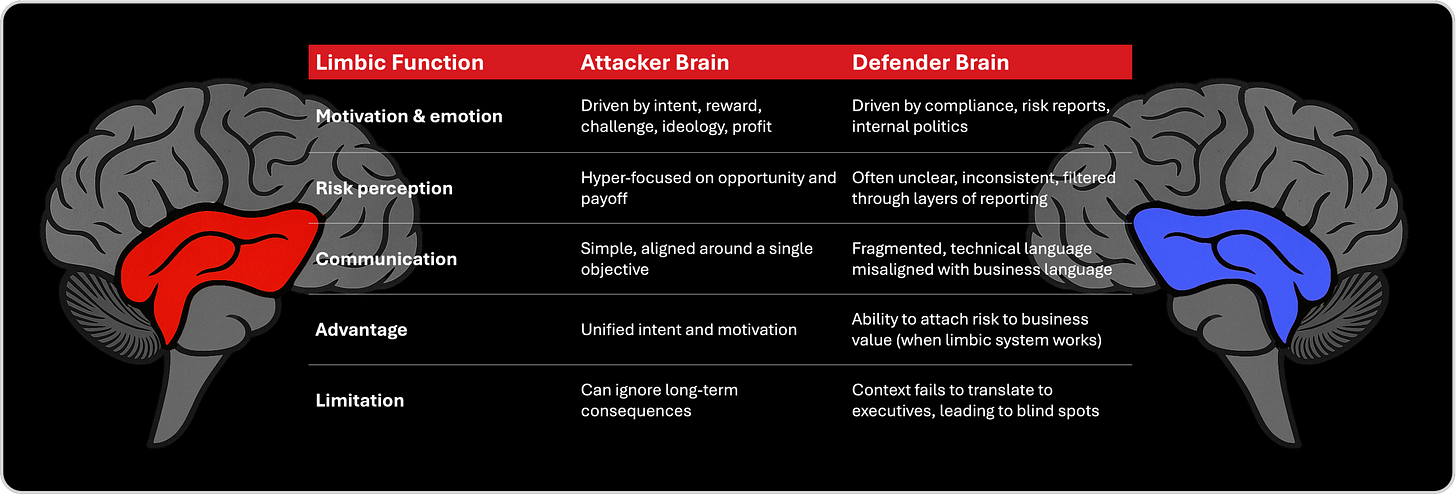
2. Limbic Layer - Context / Prioritization Layer
The limbic system is the emotional and interpretive center of cognition, the place where raw information becomes meaning, where motivation is shaped, and where priorities are formed. In cybersecurity, the limbic layer maps to cyber risk management, business alignment, and executive communication. It is where signals become impact, where risk becomes urgency, and where decisions receive their purpose. When this layer is strong, defenders understand the value of assets, the importance of exposures, and the relevance of every alert. When it is weak, context disappears, communication breaks, and the organization becomes strategically blind. This is where attackers gain a second major advantage, because their motivation is singular, unified, and unambiguous.
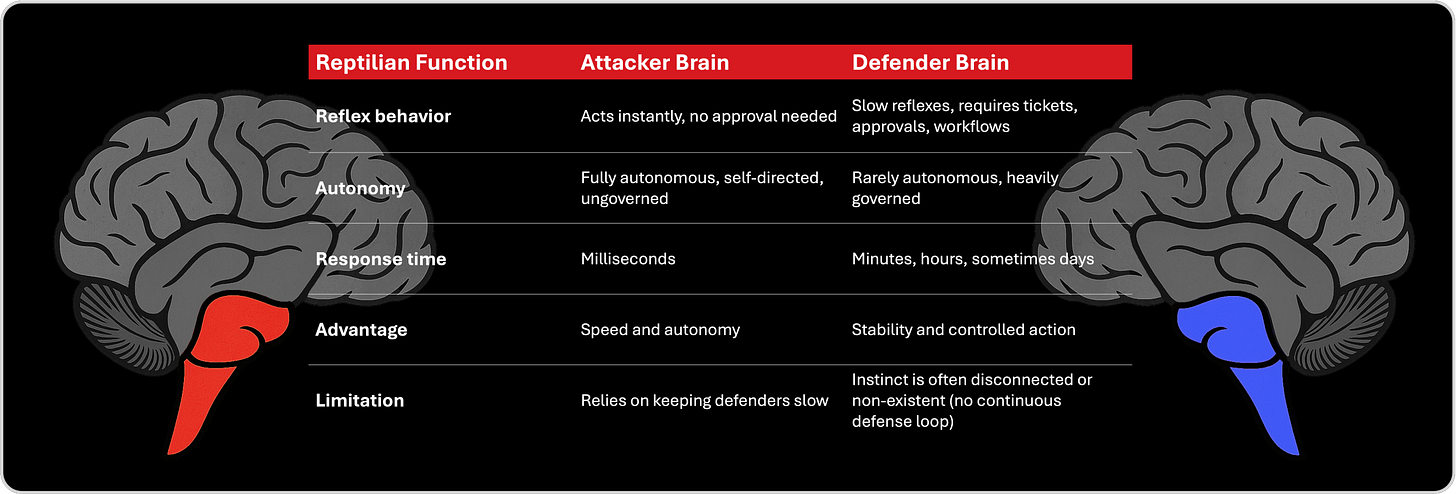
3. Reptilian Layer - Instinct / Reflex Protection Layer
The reptilian brain is the survival core, the instinctive system that acts before consciousness can intervene. In cybersecurity, this corresponds to the automated, reflexive, real time protection layer, containment, isolation, continuous defense loops, autonomic reactions. It is the only layer capable of acting in milliseconds, at the speed of the adversary. For attackers, this instinct is always active, amplified by automation and unconstrained by bureaucracy. For defenders, instinct is often disconnected, constrained by process, or entirely absent, forcing them to rely on slow cognition in situations where reflex is the only viable defense. This is where the final asymmetry emerges, attackers act instantly, defenders wait to think.
The Symptoms of Cybersecurity Paralysis
Cybersecurity paralysis rarely appears as a single catastrophic failure. It emerges slowly, almost invisibly, through a series of cognitive breakdowns inside the organization. Just as the human brain shows early signs of distress long before a crisis becomes visible, the cyber brain reveals clear symptoms when its analytical, emotional, and instinctive layers begin to fall out of alignment. These symptoms often go unnoticed because organizations look for technical root causes rather than structural or cognitive ones. Yet the patterns are unmistakable. Alert fatigue, communication breakdown, and inability to act reveal an internal architecture under stress. When these symptoms appear together, the organization enters a state where it thinks one thing, reports another, and reacts far too late.
Below are the three core symptoms, each tied to the breakdown of a different layer of the cyber brain.
1. Alert Fatigue, When the Analytical Brain Overheats
Alert fatigue is the first and most visible symptom of cybersecurity paralysis. It is the organizational equivalent of a neocortex pushed beyond its cognitive limits, forced to process far more information than it was designed to handle. Modern SOCs live surrounded by thousands of alerts, dashboards, events, anomalies, and continuous streams of telemetry demanding interpretation. Over time, the analytical brain becomes exhausted. It can no longer distinguish noise from signal, urgent from irrelevant, or meaningful from routine.
In the human brain, cognitive overload leads to decision paralysis, emotional detachment, and in extreme cases, the inability to perform basic prioritization. In cybersecurity, it manifests as endless alert triage loops, chronic burnout, missed indicators of compromise, and a sense of constant danger without clarity. When the neocortex is drowning, the rest of the system becomes unstable. It loses coherence. It loses focus. It loses the ability to protect the organism.
2. Risk Translation Failure, When the Emotional Brain Cannot Communicate
The second symptom appears in the limbic layer, the emotional and contextual system responsible for meaning, priority, and communication. In a healthy organization, this is where cyber risk becomes business impact, where technical signals are translated into language executives understand, and where decisions are guided by aligned understanding.
But in many organizations, this limbic bridge has collapsed. Security teams speak in CVEs, indicators, and technical vulnerabilities, while leadership thinks in revenue, continuity, trust, and regulatory exposure. Meaning gets lost. The emotional brain cannot translate the feelings of urgency from the SOC into a narrative the board can act upon. The result is strategic and emotional disconnection. The board sees green dashboards, while the SOC feels like the world is on fire. Technical teams operate in fear of risk, while leadership operates under the illusion of safety.
This gap explains why so many cybersecurity programs become performative instead of transformative. Without translation, there is no shared understanding. Without shared understanding, there is no aligned decision making. The limbic system fails to connect thinking with feeling.
3. Instinct Suppression, When the Survival Brain Cannot React
The deepest failure occurs in the reptilian brain, the instinctive survival layer responsible for immediate protective action. This is the part of the cyber brain that should isolate compromised assets, stop lateral movement, shut down malicious processes, and protect the core of the organization in the milliseconds when thinking is too slow.
Yet in many organizations, this instinctive layer is weak, constrained, or completely missing. There is no autonomic response, no continuous defense loop, no mechanism for instant containment. Every action requires a ticket, a meeting, an approval chain, or a committee decision. Instinct is replaced by process. Reflex is replaced by hesitation. Speed is replaced by bureaucracy.
In the human body, a delayed survival response can be fatal. In cybersecurity, delayed instinct allows attackers to operate freely inside the environment. When a threat can encrypt systems in milliseconds but organizational reflex takes hours or days, the reptilian brain is effectively disconnected from the body. Without instinct, defenders rely solely on delayed cognition, while adversaries move faster than thought.
The Consequences of Cybersecurity Paralysis
When the cyber brain loses alignment, the consequences ripple across the entire organization. Paralysis is not simply a moment of inaction, it is a structural state that weakens every layer of defense. Just as a human brain under extreme stress begins to misinterpret signals, respond too slowly, or fail to protect the body, an organization experiencing cybersecurity paralysis loses its ability to perceive, prioritize, and react in meaningful ways. The result is not only operational instability, but strategic vulnerability. Paralysis is the invisible enemy that erodes resilience long before an attacker ever arrives.
The first consequence is delayed detection. When the analytical layer is overwhelmed by noise, threats hide in the clutter. Attackers who move quickly, automate aggressively, and adapt constantly exploit exactly this condition. A single missed signal becomes a foothold, a foothold becomes persistence, and persistence becomes full compromise. Paralysis turns the SOC into a reactive, overloaded system that is always looking backward, never ahead.
The second consequence is strategic blindness. When the limbic system fails to translate risk into meaning, leadership loses visibility into the true state of exposure. This disconnect creates an illusion of safety. Dashboards look green, reports sound confident, budgets remain unchanged, and the organization continues operating under the false assumption that threats are under control. This blindness is dangerous because it prevents the business from making informed decisions. Without a clear sense of what is critical, what is vulnerable, and what requires immediate investment, risk accumulates quietly and spreads across the enterprise.
The third consequence is inability to act under pressure. When instinct is suppressed and reflex is disconnected, the organization cannot respond at the speed of the adversary. Containment becomes slow. Recovery becomes chaotic. Even simple protective actions require coordination, approvals, and debate. The reptilian brain should act instantly, but in many companies, it is replaced by bureaucracy. This delay allows attackers to escalate privileges, move laterally, and complete their objectives long before defenders can decide what to do.
Another consequence is cultural fatigue. Teams begin to feel defeated. Analysts lose trust in the tools meant to support them. Executives lose trust in the security function. Business units become frustrated by unclear communication, and cybersecurity becomes viewed as a cost rather than a strategic capability. Paralysis erodes morale, erodes alignment, and erodes confidence. It turns cybersecurity into a cycle of firefighting and rationalizing, rather than anticipating and preventing.
Perhaps the most dangerous consequence is that paralysis becomes normalized. Leaders become accustomed to slow decisions. Analysts become accustomed to constant noise. Processes become rigid rather than adaptive. Instinct becomes something the organization no longer expects to have. At this point, attackers do not just exploit vulnerabilities, they exploit organizational inertia. They exploit culture. They exploit fear. They exploit the gaps created not by technology, but by a fractured cyber brain.
Cybersecurity paralysis is not a moment, it is a pattern. It weakens detection, blinds leadership, suppresses instinct, drains culture, and invites adversaries to operate freely. Understanding these consequences is the first step toward addressing them, because only when an organization sees paralysis clearly can it begin the work of restoring coherence to its cyber brain.
The Illusion of Strength, When the Three Parts of the Cyber Brain Exist but Never Connect
One of the most dangerous illusions in modern cybersecurity is the belief that having the best analytics platform, the best governance framework, and the best response tools automatically creates a strong security posture. On paper, it looks like the organization has built the perfect neocortex, the perfect limbic system, and the perfect reptilian brain. Yet in practice, these layers often operate as isolated islands, each doing its job extremely well, but none of them working together. This is the structural illusion that misleads executives into believing they are protected when, in reality, they are fragmented.
The analytical layer may be world class, capable of processing vast volumes of telemetry and producing precise insights, but without a contextual layer that transforms signals into organizational meaning, even the most intelligent neocortex becomes blind to business relevance. At the same time, the risk and governance layer may be mature, producing elegant frameworks, policies, and reports that look coherent on paper, but without connection to accurate, real time intelligence, those documents become detached from the operational reality they are meant to guide. And the instinctive layer, the reflexive defense mechanisms that automate containment and limit damage, may be fast and sophisticated, but without the direction of risk context or the insight of analytics, instinct becomes either overly cautious or dangerously permissive.
This illusion of isolated excellence is one of the primary causes of cybersecurity paralysis. Each part of the cyber brain exists, each part is funded, each part is praised during audits or assessments, yet none of them communicate with one another. The neocortex thinks without understanding what matters, the limbic system reports without knowing what is happening on the ground, and the instinctive layer acts without alignment to business priorities. It creates a condition where the organization believes it is intelligent, compliant, and reactive, while in reality it is uncoordinated and vulnerable.
The beauty of the human brain does not come from having the best neocortex, or the strongest limbic system, or the fastest instincts. The beauty comes from integration. The human brain thrives because thought, emotion, and reflex operate in harmony, informing and amplifying each other. Decision making becomes powerful not when these systems operate independently, but when they create coherence. Cybersecurity is no different. Excellence in isolated layers does not create resilience. Resilience emerges when intelligence is contextualized, when context guides instinct, and when instinct protects the space needed for intelligence to operate. The true power of cybersecurity comes not from perfect parts, but from the unity between them.
How to Restore the Cyber Brain, Rebuilding Alignment Across Intelligence, Context, and Instinct
Restoring the cyber brain is not a matter of adding more tools or expanding more dashboards. It is a matter of rebuilding coherence across the three layers that shape every security decision, the analytical neocortex, the contextual limbic system, and the instinctive survival brain. When these layers operate in isolation, organizations think slowly, communicate poorly, and act too late. When they operate together, cybersecurity becomes fluid, adaptive, and capable of responding to threats with the unity and speed of a living organism. Rebuilding this alignment is the path out of paralysis.
The first step is to clear the analytical layer. The neocortex cannot operate when overwhelmed with noise, so organizations must focus on reducing unnecessary signals, consolidating telemetry, and prioritizing high fidelity data. Intelligent filtering, native telemetry, and integrated platforms make thinking possible again. Just as the human brain thrives when distractions are removed, the cyber brain regains clarity when analysts can focus on what truly matters. This is not about collecting more data, it is about collecting the right data and allowing the analytical brain to regain its ability to perceive threats clearly.
The second step is strengthening the limbic layer, the system responsible for converting signals into meaning. Cyber risk management becomes the translator that connects technical intelligence with business priorities. By quantifying exposure, mapping impact, and assigning value, the limbic system teaches the entire organization what matters most. It helps analysts understand the business consequences of a technical event, and it helps leaders understand the technical signals that shape business risk. When the limbic system is healthy, cybersecurity communication becomes coherent. The SOC stops speaking in alerts, and the board stops relying on surface level dashboards. The organization begins to think with one voice.
The third step is reconnecting the instinctive layer. The reptilian brain of cybersecurity, the instinctive defense layer, must be active and integrated rather than constrained. Autonomic response, continuous defense loops, and protective reflexes allow the system to act during the milliseconds where cognition is too slow. Attackers succeed because their instinct is immediate. Defenders succeed when their instinct is connected. This does not eliminate human decision making, it amplifies it. Instinct buys time for intelligence. Reflex buys space for analysis. Immediate protection prevents crises from becoming catastrophes.
Rebuilding the cyber brain requires unifying the three layers through a continuous foundation of cyber risk management. Intelligence without context becomes noise, context without instinct becomes delay, and instinct without intelligence becomes blind. Cyber risk management is what brings these layers into coherence. It determines what matters most, it gives meaning to signals, and it ensures that instinctive protections activate where the business is most exposed. When intelligence is shaped by risk, when context is informed by impact, and when instinct responds in alignment with enterprise priorities, the organization becomes capable of thinking, feeling, and acting as a cohesive whole. It gains the clarity and unity needed to resist adversaries who move with human intent and machine speed.
The cyber brain is restored when cyber risk management brings clarity back to analysis, coherence back to communication, and confidence back to action. Once intelligence, context, and instinct are aligned around a shared understanding of risk, the organization is no longer paralyzed. It becomes aware, adaptive, and resilient, not because it has added more tools, but because it has reconnected the essential architecture of its decision making. In a world where threats move fast, criminal networks operate fluidly, and exposure evolves continuously, restoring the cyber brain through risk management is not just an improvement, it is a necessity.
Cyber Resilience as the Result of a Coherent Cyber Brain
Cybersecurity has entered an era where adding more tools, more telemetry, and more analytics no longer guarantees safety. The challenges we face today are not only technical but cognitive and structural. They are failures of coherence inside the organizational brain. Just as the human mind falters when its analytical, emotional, and instinctive layers fall out of sync, the cyber brain collapses when intelligence is overloaded, risk context is unclear, and instinctive protections are disconnected. Attackers exploit this fragmentation not through superior sophistication, but through superior alignment. Their thinking, motivation, and action are unified, while defenders often operate with disconnected priorities, unclear signals, and delayed reflexes.
This is where cyber resilience truly begins. Resilience is not the result of perfect tools or flawless prevention, it is the result of restored coherence. It emerges when the analytical layer can perceive clearly rather than drown in noise, when the contextual limbic layer can translate risk into meaning that leaders understand, and when the instinctive layer can act autonomously in the milliseconds where analysis is too slow. Cyber resilience is not a product feature, it is the ability of an organization to continue thinking, adapting, and acting even under pressure. It is the operational expression of a healthy cyber brain.
And at the center of this alignment is cyber risk management. Cyber risk management is the connective tissue that turns intelligence into priority and instinct into purposeful action. It gives cybersecurity meaning by linking every signal, every exposure, and every decision to what the organization values most. By establishing continuous visibility into exposure, by translating technical risk into business impact, and by guiding decision making across all layers, cyber risk management becomes the limbic system of the organization, the interpreter that creates coherence. Without it, intelligence becomes noise and instinct becomes blind. With it, the entire cyber brain becomes aligned.
The future of cybersecurity will belong to organizations that understand this relationship, that recognize paralysis as a structural signal, not a technical flaw, and that invest in rebuilding the internal architecture required for resilience. It will belong to leaders who understand that cyber resilience is not achieved through isolated technologies but through the integration of intelligence, risk, and instinct into a single coordinated system. And it will belong to those who embrace cyber risk management not as a compliance requirement but as the strategic discipline that brings coherence back to the cyber brain.
In the end, cybersecurity is not just about defending systems. It is about restoring the organizational mind so that it can sense, interpret, and act with unity. When intelligence, context, and instinct move together, defenders become resilient not because they stop every attack, but because they can navigate any attack with clarity and purpose. Coherence is the foundation of cyber resilience, and cyber risk management is the language that makes coherence possible.
Castro, J. (2025). Artificial Intelligence (AI) vs Artificial Instinct (Ai), The Distinction Cybersecurity Can’t Afford to Ignore. ResearchGate. https://www.researchgate.net/publication/397834714 DOI:10.13140/RG.2.2.31096.30725
Castro, J. (2025). What More Than 10 Years Working with INTERPOL Taught Me About Cybersecurity. ResearchGate. https://www.researchgate.net/publication/395524745 DOI:10.13140/RG.2.2.13176.92160
Castro, J. (2025). Rethinking the Pyramid of Pain in 2025: Precision, Pressure, and the Power of Context. ResearchGate. https://www.researchgate.net/publication/394107570 DOI:10.13140/RG.2.2.24252.35201
Castro, J. (2025). Context is Everything in Cybersecurity: Why Signals Without Meaning Are Just Noise. ResearchGate. https://www.researchgate.net/publication/392408653 DOI:10.13140/RG.2.2.15442.26561
Castro, J. (2025). Umbrellas, Storms, and Cyber Risk: Why Threat Management Is Not Risk Management. ResearchGate. https://www.researchgate.net/publication/396695719 DOI:10.13140/RG.2.2.24818.98240
Castro, J. (2025). What Is Governance in Cybersecurity?. ResearchGate. https://www.researchgate.net/publication/393065290 DOI:10.13140/RG.2.2.30988.63360
Castro, J. (2025). Cyber RiskOps: Bridging Strategy and Operations in Cybersecurity. ResearchGate. https://www.researchgate.net/publication/388194428 DOI:10.13140/RG.2.2.36216.97282/1
Castro, J. (2025). Cyber Risk Operational Model (CROM): From Static Risk Mapping to Proactive Cyber Risk Operations. ResearchGate. https://www.researchgate.net/publication/390490235 DOI:10.13140/RG.2.2.15956.92801
Castro, J. (2024). Simplifying Cybersecurity with the Cybersecurity Compass and the Feynman Technique. ResearchGate. https://www.researchgate.net/publication/388528834 DOI:10.13140/RG.2.2.32458.48327/1
Castro, J. (2025). When GRC and Heatmaps Do More Harm Than Good to Cyber Risk Management -Building the Language of Cyber Risk. ResearchGate. https://www.researchgate.net/publication/397440511 DOI:10.13140/RG.2.2.11185.85601/1