Cybercriminals Have the Advantage: A Call for Radical Change in Cyber Risk Management
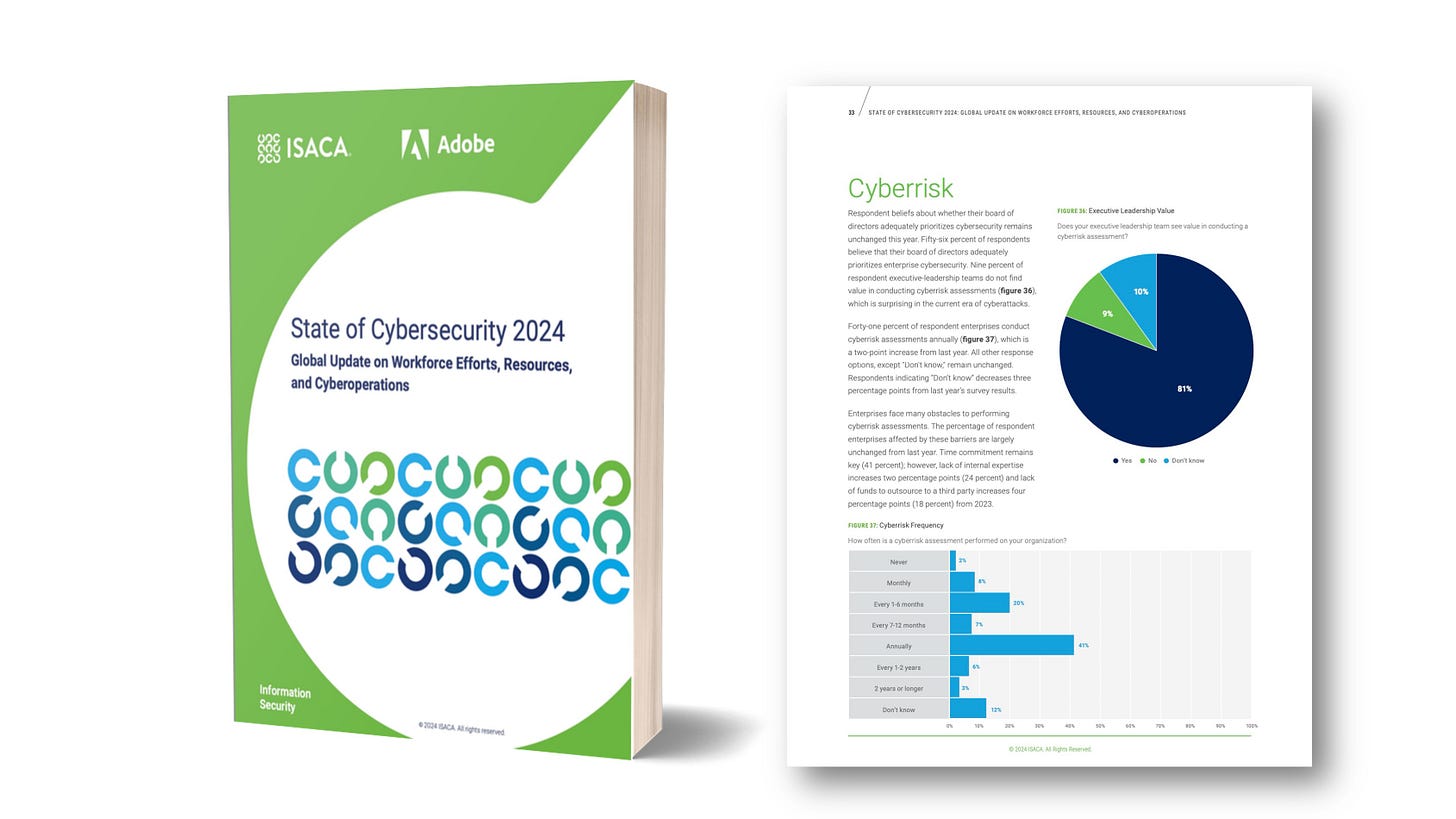
In the age of constant cyber threats, one would assume organizations are evolving rapidly to counteract cybercriminals. Yet, a quick glance at the latest ISACA State of Cybersecurity Report 2024 reveals a worrying trend: 41% of enterprises conduct cyber risk assessments only once a year, and shockingly, 12% still don’t know how frequently assessments occur. Meanwhile, cybercriminals operate with agility and innovation, continuously exploiting vulnerabilities as they emerge. This begs the question: Why do they have the upper hand? The answer lies in our outdated approach to cyber risk management and measurement.
As highlighted in a McKinsey report from 2019, The Risk-Based Approach to Cybersecurity:
“Attackers benefit from organizational indecision on cyber risk.”
Fast forward to 2024, and the latest ISACA State of Cybersecurity Report shows that many of these lessons remain unlearned. Despite increasing awareness of the threats, the pace of improvement in cyber risk management has been disappointingly slow, leaving organizations vulnerable to the ever-evolving tactics of cybercriminals.
This indecision stems from a lack of clarity about the danger and a failure to execute effective cyber controls. The result? Debilitating attacks on high-profile institutions are proliferating globally. Despite this, many organizations remain caught in a cycle of inaction or incomplete action, lacking the necessary enterprise-wide cyber efforts to combat these threats.
The urgency is clear: “Business leaders everywhere, at institutions of all sizes and in all industries, are earnestly searching for the optimal means to improve cyber resilience,” as the McKinsey report notes. There is no time to waste — the status quo is not only insufficient; it actively benefits attackers.
The 4Vs of Cyber Risk: Volume, Velocity, Variety, and Visibility
Today’s cyber risk environment is defined by the 4Vs:
Volume: The sheer measure of cyberattacks continues to grow exponentially. A once-a-year cyber risk assessment cannot possibly keep pace.
Velocity: Cyber threats evolve at breakneck speed, with new tactics and vulnerabilities emerging daily. The lag in annual or semi-annual assessments leaves organizations dangerously exposed.
Variety: Attack surfaces now include cloud environments, unmanaged assets, humans behaviours, and third-party integrations, beyond traditional IT systems.
Visibility: Many organizations lack visibility into their cyber risk posture, leading to blind spots that adversaries actively exploit.
These factors highlight why our current methods fall short. NIST CSF 2.0 emphasizes the need for continuous monitoring and governance as foundational elements of modern cybersecurity. Recognizing this need is only the first step — action is the next frontier.
Why the Status Quo is Unsustainable: The Danger of a False Sense of Security
The ISACA report provides a striking contradiction: while 81% of executive leadership teams claim to see value in conducting cyber risk assessments, the speed and frequency of these assessments remain alarmingly insufficient. Most organizations conduct assessments annually or semi-annually, entirely out of sync with the rapid evolution of cyber threats. This disconnect reveals a misunderstanding of cyber risk compared to other business risks.
Cyber risk is unique because it operates in a constantly shifting context. Unlike financial or operational risks, which may remain relatively stable over time, cyber risks are dynamic. New vulnerabilities, attack vectors, and threat actors emerge daily. Decisions made based on outdated risk assessments are inherently flawed. By the time these assessments inform executive decisions, the context has already changed, rendering those decisions suboptimal at best, and dangerous at worst.
The Value Problem: Outdated Insights Lead to Poor Decisions
Organizations often tout the value of their cyber risk assessments, but this value is based on static snapshots that fail to capture the real-time nature of cyber threats. Leadership may feel reassured by these periodic assessments, but this reassurance is a false sense of security — one of the most dangerous outcomes for any cybersecurity strategy.
This false confidence creates a critical blind spot. Organizations may believe they have a strong handle on their cyber risks, but in reality, they are relying on outdated insights that do not reflect the current threat environment. This illusion of control can lead to complacency, delayed responses, and misinformed decisions, ultimately leaving the organization more vulnerable than if they had no assessment at all.
In cybersecurity, everything is about context — and without continuous, up-to-date context, organizations are flying blind. Consider this: an organization conducts a comprehensive risk assessment in January. By March, new vulnerabilities emerge, threat actors shift tactics, and the organization adopts new cloud services. Yet, leadership continues to rely on January’s assessment to make critical decisions. This is akin to navigating with a map from last year, ignoring that the terrain has fundamentally changed.
This misalignment between perceived security and actual risk exacerbates exposure, as decisions made under a false sense of security are inherently flawed. To truly protect themselves, organizations must replace periodic assessments with continuous, real-time risk evaluations that reflect the constantly evolving nature of cyber threats.
The danger is clear: until this shift happens, the false sense of security provided by occasional assessments will leave organizations vulnerable to preventable attacks.
A Call for Continuous Contextual Awareness
To break free from this outdated model, organizations must recognize that cyber risk management cannot be static. Continuous monitoring and real-time risk scoring are essential for maintaining the context necessary for informed decision-making. Only then can organizations ensure their cybersecurity strategies remain relevant and effective in the face of an ever-changing cyber risk.
The Case for Continuous Cyber Risk Scoring System (CCRSS)
Cybercriminals are not constrained by the rigid timelines of annual assessments. They exploit vulnerabilities in real time, often leveraging sophisticated AI and machine learning tools. In contrast, many organizations are left playing catch-up, operating under a reactive model.
This is where the Continuous Cyber Risk Scoring System (CCRSS) can revolutionize the landscape. Unlike traditional assessments, CCRSS provides real-time insights into an organization’s risk posture by continuously analyzing vulnerabilities, threat intelligence, and business impact. This allows organizations to:
Prioritize vulnerabilities dynamically based on evolving threats.
Adapt defenses in real time, rather than waiting for the next assessment.
Bridge the communication gap between technical teams and business leaders by presenting cyber risks in a clear, quantified format.
The Cybersecurity Compass: Integrating Cyber Risk Management into a Continuous Cycle
A significant reason cybercriminals maintain the upper hand is the fragmented approach many organizations take toward cybersecurity. Cyber risk management is often seen as a discrete activity, carried out once or twice a year. This piecemeal approach leaves organizations exposed to the rapid and continuous evolution of cyber threats. To combat this, the Cybersecurity Compass integrates cyber risk management into a continuous cycle of preparation, detection, response, and recovery.
A Continuous, Holistic Approach to Cybersecurity
The Cybersecurity Compass divides cybersecurity into three interconnected phases, ensuring risk management remains an ongoing, dynamic process:
Before a Breach: Proactive Cyber Risk Management: Continuously identify and mitigate risks before they materialize. Using tools like CCRSS, companies can measure their risk posture in real time.
During a Breach: Detection and Response: In the heat of an attack, risk management plays a pivotal role. Real-time detection and response prioritize high-risk assets.
After a Breach: Cyber Resilience: Focus on recovery and learning. Post-incident analysis feeds directly back into the risk management process, improving defenses for the future.
Closing the Gap: Why Cyber Resilience Is Needed Now
As the McKinsey report further notes:
“Debilitating attacks on high-profile institutions are proliferating globally, and enterprise-wide cyber efforts are needed now with great urgency.”
The need for radical change is not just urgent; it is existential. Until organizations adopt continuous, dynamic frameworks like the Cybersecurity Compass and leverage real-time risk management tools, they will remain vulnerable to cybercriminals who thrive on organizational inertia. The time to act is now — because no organization can hope to stay ahead without a continuous understanding of its evolving cyber risk.