Cyber Resilience: The Learning Phase of the Cybersecurity Compass Framework
In the stormy sea of today’s cyber landscape, where waves of threats and breaches crash relentlessly, organizations must navigate with more than just preventative measures. The reality is that no ship can sail without facing turbulent waters, and no organization is immune to cyber incidents. What matters most is the ability to weather the storm and emerge stronger. This is where Cyber Resilience, a critical phase of the Cybersecurity Compass framework, plays a pivotal role.
Understanding Cyber Resilience
Cyber resilience is the ability of an organization to sustain its critical functions during and after a cyber incident. It ensures that despite facing disruptions, an organization can absorb the impact, recover swiftly, and evolve to prevent similar occurrences in the future. The paper Unpacking Cyber Resilience from World Economic Forum highlights this dual focus:
“Organizations must shift their mindset from solely preventing attacks to also ensuring resilience post-incident” .
The Cybersecurity Compass integrates cyber resilience as a critical phase, reinforcing the idea that cybersecurity is a continuous cycle. This phase works in tandem with Cyber Risk Management (before a breach) and Detection and Response (during a breach), forming a comprehensive defense strategy.
The Role of Zero Trust in Cyber Resilience
Zero Trust Architecture (ZTA) plays a crucial role in enhancing cyber resilience. It operates on the principle of “never trust, always verify,” enforcing strict access controls and continuous verification of users and devices. Zero Trust strengthens resilience by:
Minimizing Breach Impact: By limiting lateral movement within the network, Zero Trust ensures that even if an attacker gains access, their ability to compromise critical assets is restricted.
Enhancing Detection and Response: Continuous monitoring identifies anomalies in real time, enabling rapid containment.
Facilitating Swift Recovery: By segmenting systems, Zero Trust ensures that recovery efforts are localized, reducing downtime for unaffected areas.
Adapting Dynamically: Real-time risk assessments enable flexible access controls, aligning security measures with the evolving threat landscape.
Visualizing Cyber Resilience in Practice
These visualizations provide a clear representation of how cyber resilience minimizes the impact of cyber incidents and ensures operational continuity.
Shrinking the Impact of Cyber Incidents
This diagram illustrates the journey from a cyber incident to recovery and adaptation. It outlines three critical phases:
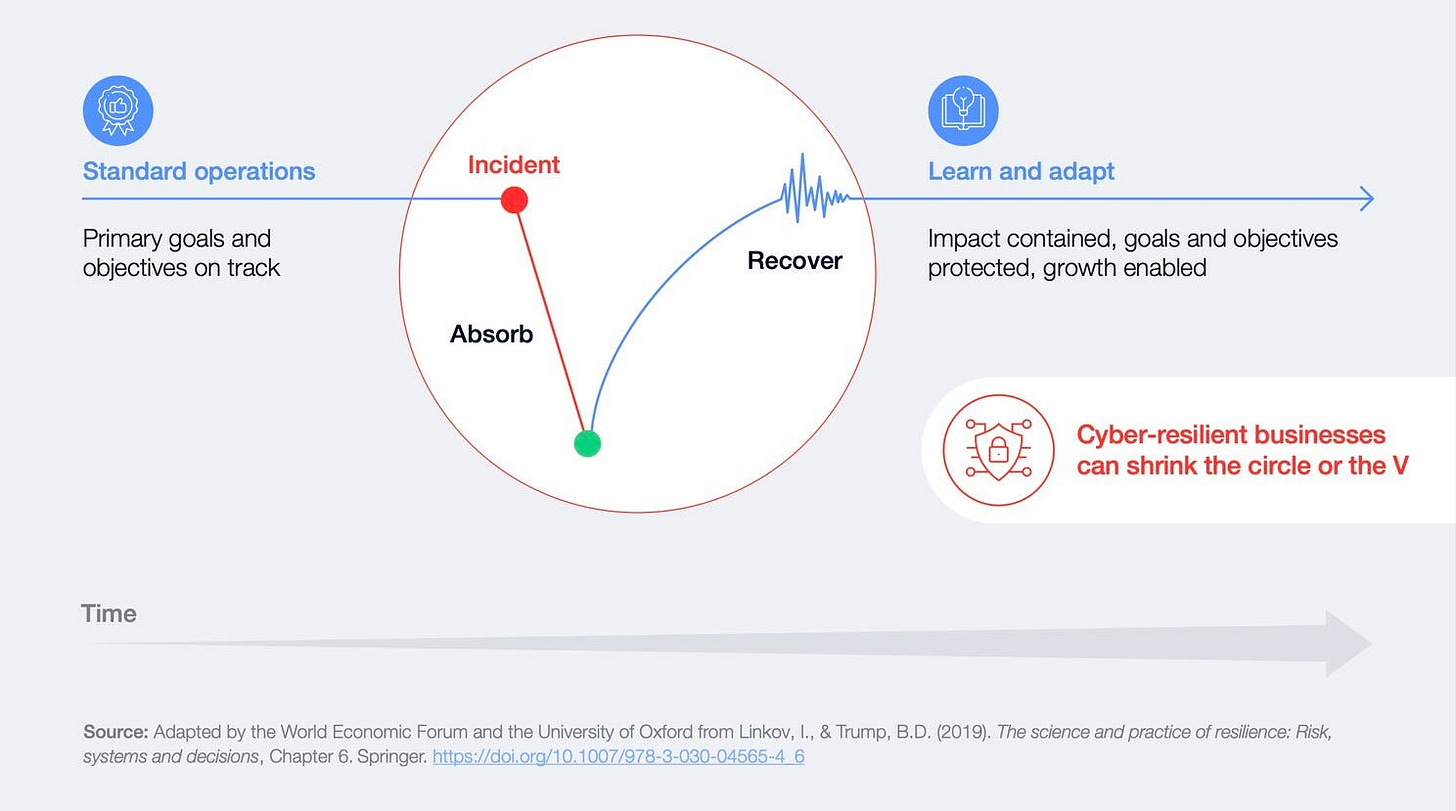
Incident and Absorption: The initial impact disrupts operations, but resilient organizations absorb the shock effectively.
Recovery: Prompt restoration of critical functions minimizes operational downtime.
Learn and Adapt: Post-incident analysis drives improvements in defenses and response strategies.
The goal is to “shrink the circle,” reducing both the severity of the impact and the time required for recovery. Cyber-resilient organizations can rapidly return to normalcy, maintaining alignment with their strategic objectives.
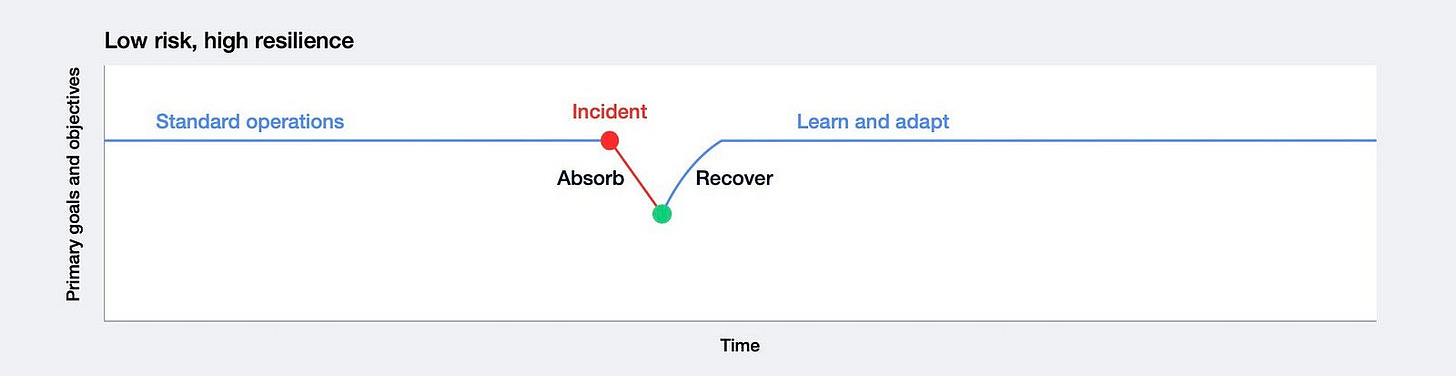
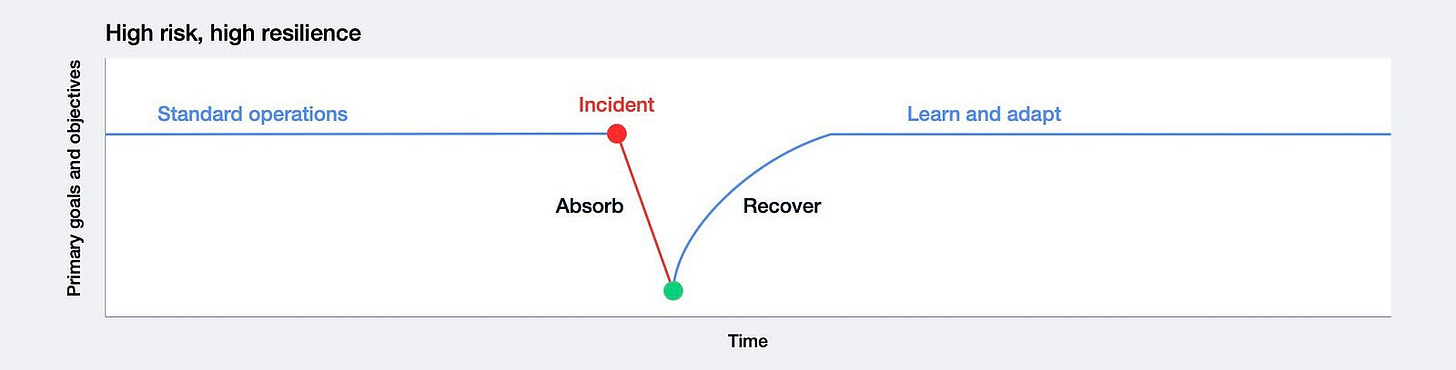
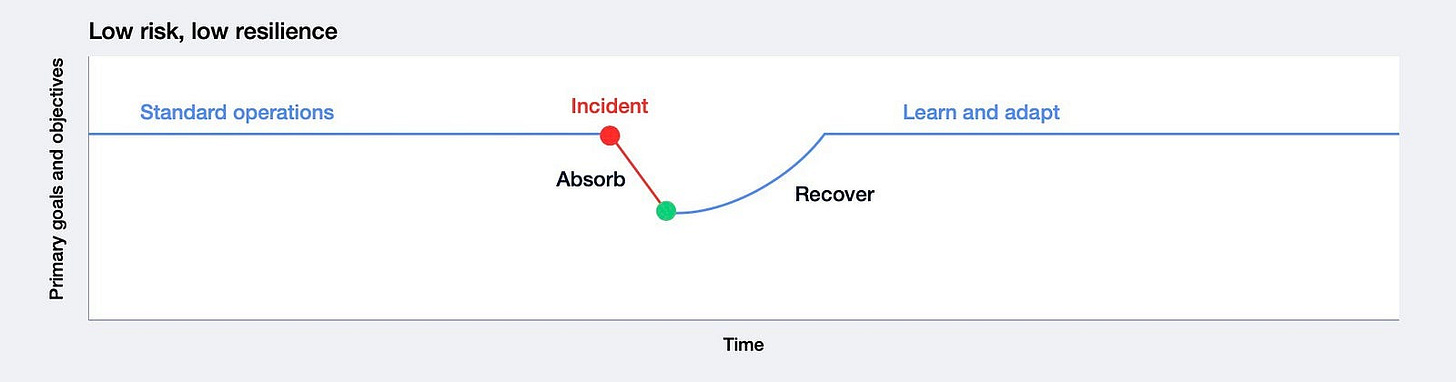
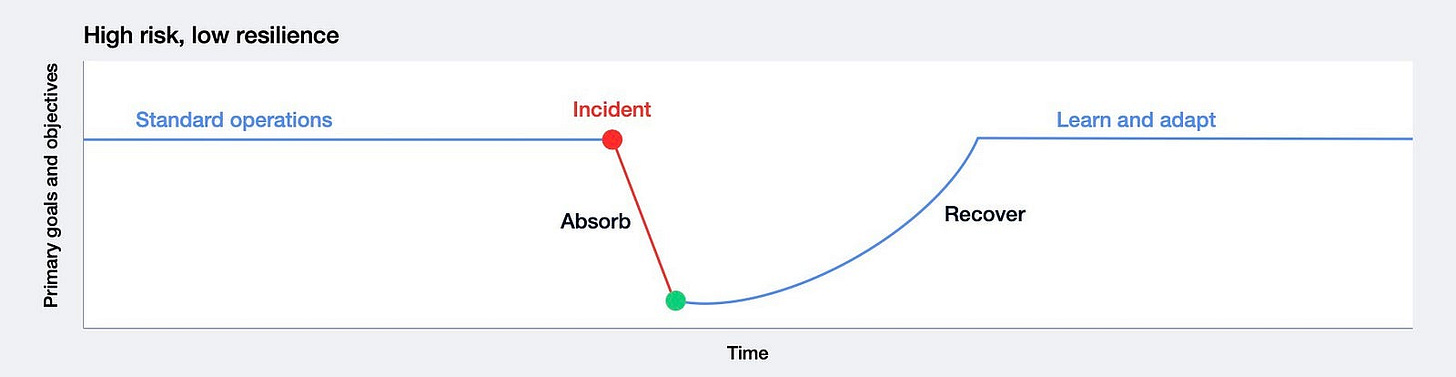
Cyber Resilience Profiles Across Cyber Risk Levels
These diagram categorizes organizations based on their cyber risk exposure and resilience
Low Cyber Risk, High Cyber Resilience: Minimal disruption with quick recovery.
High Cyber Risk, High Cyber Resilience: Even in high-risk environments, these organizations demonstrate rapid restoration.
Low Cyber Risk, Low Cyber Resilience: Smaller risks lead to prolonged recovery due to weak resilience measures.
High Cyber Risk, Low Cyber Resilience: Prolonged recovery and severe disruptions due to high risk and poor resilience capabilities.
Continuous Cyber Risk Scoring: A Foundational Element
Continuous Cyber Risk Scoring System (CCRSS) is essential for maintaining cyber resilience. By providing real-time insights into an organization’s risk posture, CCRSS enables:
Identification of Emerging Risks: Highlighting vulnerabilities and threats before they escalate.
Prioritization of Remediation Efforts: Allocating resources to address the most critical risks.
Tracking of Resilience Improvements: Measuring the effectiveness of risk mitigation strategies over time.
CCRSS ensures that organizations are constantly aware of their risk environment, supporting informed decision-making and proactive adjustments to security measures.
The Role of Red Teaming in Enhancing Cyber Resilience
Red Teaming Exercises simulate real-world attack scenarios, providing a critical test of an organization’s defenses and incident response capabilities.
The real questions are, what works in practice — and how can this be identified? What can organizations learn from the front-line experience of others?
These exercises are vital for:
Identifying Hidden Vulnerabilities: Exposing gaps that may not be evident through standard assessments.
Validating Response Plans: Ensuring that incident response strategies are effective under pressure.
Strengthening Recovery and Adaptation: Highlighting areas for improvement in resilience and operational continuity.
By challenging the organization’s defenses, red teaming provides actionable insights that enhance both its resilience and overall security posture.
Integrating Resilience: People, Processes, and Technology
Cyber resilience relies on the seamless integration of People, Processes, and Technology:
People: Employees are the first line of defense. Regular training ensures they are prepared to recognize and respond to threats. Clear roles within incident response teams facilitate coordinated action during crises.
Processes: Well-defined and regularly tested processes, including incident response and business continuity plans, ensure organizations can recover quickly and effectively.
Technology: Advanced technologies such as AI-powered detection systems, automated recovery tools, and predictive analytics play a crucial role in enabling swift and efficient responses. Zero Trust principles further enhance this by continuously validating access and segmenting critical assets.
Cyber Resilience as Part of a Continuous Cycle
Cyber resilience is not a one-time achievement but a continuous process. Each incident provides lessons that feed into improved Cyber Risk Management and more effective Detection and Response. As the WEF report states,
“Resilience is not about preventing every attack but ensuring recovery while protecting critical business objectives” .
This cycle of learning and adaptation strengthens the organization’s ability to handle future incidents.
In an era of constant cyber threats, Cyber Resilience is a critical phase of the Cybersecurity Compass framework. It ensures that organizations can recover from incidents, learn from them, and adapt to prevent future disruptions.
By incorporating Zero Trust, Continuous Cyber Risk Scoring, and Red Teaming Exercises, organizations can minimize the impact of cyber risks and maintain their strategic goals. This integrated approach not only strengthens their defenses but also builds a resilient foundation for sustainable growth in an unpredictable digital landscape.





