Beyond Questionnaires: Why We Must Rethink Cyber Insurance in the Digital Age
At its core, the insurance industry serves as a cornerstone of modern risk management, providing individuals and businesses with a mechanism to transfer the financial burden of unforeseen events. By pooling resources, insurers offer protection against a myriad of risks — from natural disasters and health issues to property damage and liability claims. This fundamental principle of risk transfer allows policyholders to navigate uncertainties with greater confidence, ensuring stability and continuity in the face of adversity.
Traditionally, insurance has encompassed areas such as life, auto, and property, each addressing specific vulnerabilities inherent in daily life and commerce. However, as our world becomes increasingly digital and interconnected, a new frontier of risk has emerged: cyber threats. The proliferation of technology and reliance on information systems have exposed organizations to a range of cyber risks, including data breaches, ransomware attacks, and system outages. These incidents not only pose significant financial losses but also threaten reputational integrity and operational viability.
In response to this evolving landscape, the cyber insurance industry has emerged as a specialized sector dedicated to mitigating the unique risks associated with the digital age. By extending the foundational principles of traditional insurance, cyber insurance offers tailored coverage that addresses the complexities of cyber threats, helping businesses safeguard their digital assets and maintain resilience in an ever-changing threat environment. This article delves into the intricacies of the cyber insurance industry, exploring how it builds upon the established practices of risk transfer to meet the demands of today’s technologically driven world.
The 4Vs That Define the Uniqueness of Cyber Risks
One of the critical issues facing the cyber insurance industry is its foundational reliance on traditional insurance models, which often fail to fully account for the distinct characteristics of cyber risks. Traditional insurance mechanisms are adept at managing and transferring risks that are generally stable, predictable, and well-understood. However, cyber risks are fundamentally different, defined by four key dimensions known as the 4Vs — Velocity, Volume, Visibility, and Variety. These dimensions not only highlight the complexity of cyber threats but also underscore why conventional risk management tools and insurance products may fall short. This section delves into each of the 4Vs, illustrating their unique impact on cyber risk and the necessity for tailored approaches in the cyber insurance landscape.
1. Velocity: The Dual Pace of Business and Attackers
Velocity in the context of cyber risk encompasses two intertwined aspects:
Velocity of Business: This refers to the rapid adoption of new technologies and digital practices by organizations. As businesses increasingly integrate advanced technologies — such as cloud computing, IoT devices, and AI-driven applications — their cyber environments expand, introducing new potential vulnerabilities at an unprecedented pace.
Velocity of Attackers: Cybercriminals are equally swift in adapting to technological advancements, constantly evolving their tactics to exploit emerging vulnerabilities. The speed at which attackers develop and deploy sophisticated malware, ransomware, and other malicious tools necessitates that defenses are not only reactive but also proactive and anticipatory.
Implications for Cyber Insurance:
Dynamic Coverage Models: Traditional insurance policies, which rely on historical data and static risk assessments, struggle to keep up with the rapid changes in both business operations and attacker strategies. Cyber insurance must incorporate dynamic coverage models that can adapt to the evolving threat landscape in real-time.
Proactive Risk Management Services: Insurers should offer services such as continuous monitoring, threat intelligence, and incident response planning to help policyholders stay ahead of potential attacks and mitigate risks promptly.
Continuous Cyber Risk Monitoring: Implementing continuous monitoring allows insurers to detect and respond to threats in real-time, ensuring that coverage remains relevant and effective as both business operations and cyber threats evolve.
2. Volume: The Scale of Data, Threats, and Assets
Volume refers to the sheer magnitude of data, the number of threats, and the diversity of assets within modern enterprises:
Data Volume: Organizations today handle vast amounts of data, ranging from customer information and intellectual property to operational data and financial records. The continuous growth in data volume increases the potential targets for cyberattacks.
Threat Volume: The number of potential threats is exponentially higher in the cyber realm compared to traditional risk domains. Each day brings new vulnerabilities and potential exploits, making comprehensive monitoring and protection a daunting task.
Asset Volume: Enterprises possess a wide array of digital assets, including on-premise hardware, cloud-based services, mobile devices, and interconnected IoT devices. Managing and securing this extensive volume of assets requires sophisticated and scalable security strategies.
Implications for Cyber Insurance:
Scalable Policy Structures: Insurance products must be designed to scale with the growing volume of data and assets, ensuring that coverage remains adequate as an organization’s digital footprint expands.
Enhanced Data Analytics: Insurers need robust data analytics capabilities to process and analyze the vast amounts of information related to cyber incidents, enabling more accurate risk assessments and tailored coverage options.
Continuous Cyber Risk Monitoring: With the high volume of data and threats, continuous monitoring is essential to manage and mitigate risks effectively, providing insurers with up-to-date information to adjust policies and respond to incidents swiftly.
3. Visibility: The Challenge of Comprehensive Insight
Visibility pertains to the ability to fully comprehend and monitor an organization’s digital landscape:
Attack Surface Complexity: Modern enterprises often operate with a sprawling and complex attack surface, including shadow IT (unsanctioned software and devices used by employees), extensive cloud infrastructures, unmanaged assets, remote work environments, and third-party and supply chain connections. This complexity makes it challenging to maintain complete visibility into potential vulnerabilities.
Hidden Risks: Elements like shadow IT and unmanaged assets can harbor hidden risks that are difficult to detect and mitigate, increasing the likelihood of unnoticed breaches and data leaks.
Implications for Cyber Insurance:
Comprehensive Risk Assessments: Insurers must conduct thorough and continuous risk assessments that account for all facets of an organization’s digital footprint, including less visible components like third-party integrations and shadow IT.
Advanced Visibility Tools: Offering or partnering with providers of advanced visibility and monitoring tools can help policyholders gain better insights into their security posture, thereby reducing blind spots and enhancing overall risk management.
Continuous Cyber Risk Monitoring: Maintaining ongoing surveillance of an organization’s digital environment ensures that hidden risks are identified and addressed promptly, allowing insurers to offer more accurate and responsive coverage.
4. Variety: The Diversity of Attack Surfaces
Variety highlights the wide range of attack surfaces and the multifaceted nature of cyber threats. Unlike traditional risks that may be more contained, cyber risks involve multiple interconnected attack surfaces that require specialized attention:
External Attack Surface: This includes all the points of interaction between an organization and external entities, such as public-facing websites, email servers, and APIs. External attack surfaces are constantly exposed to new threats from outside the organization, making them a primary target for cybercriminals.
Internal Attack Surface: These are the vulnerabilities within an organization’s internal network, including internal servers, workstations, and internal communication systems. Insider threats, whether malicious or accidental, can exploit internal weaknesses to gain unauthorized access to sensitive information.
Cloud Attack Surface: With the increasing reliance on cloud services, the cloud attack surface has expanded significantly. This includes cloud storage, cloud-based applications, and virtualized environments, each presenting unique security challenges that differ from traditional on-premises setups.
Human Attack Surface: Often considered the weakest link in cybersecurity, the human attack surface involves social engineering attacks such as phishing, spear-phishing, and other tactics that exploit human behavior to gain unauthorized access or information.
Implications for Cyber Insurance:
Tailored Coverage Options: Insurance products must offer customizable coverage that addresses the specific types of attack surfaces relevant to different industries and organizational structures. For example, a company heavily reliant on cloud services would require different coverage compared to one with a significant internal network presence.
Specialized Expertise: Insurers should employ or collaborate with cybersecurity experts who possess in-depth knowledge of diverse attack surfaces and threat vectors to accurately assess risks and design appropriate policies.
Continuous Cyber Risk Monitoring: Given the variety of attack surfaces, continuous monitoring is vital to identify and respond to diverse cyber incidents, ensuring that insurers can provide timely and relevant coverage adjustments.
Bridging the Assessment Gap: Moving Beyond Questionnaires in Cyber Insurance
While the cyber insurance industry has made significant strides in adapting traditional insurance models to address the unique challenges of cyber risk, a critical gap remains in the current assessment process. Presently, obtaining cyber insurance often involves filling out a detailed questionnaire that captures an organization’s cybersecurity posture at a single point in time. This static approach fails to account for the dynamic and ever-evolving nature of cyber threats, leading to several limitations that undermine the effectiveness and accuracy of risk assessments. By examining this gap, we can better understand the necessity for more advanced, continuous assessment methods.
The Current Process: Static Questionnaires
The standard process for acquiring cyber insurance typically involves the completion of comprehensive questionnaires designed to evaluate an organization’s cybersecurity measures. These questionnaires cover various aspects, including:
Security Policies and Procedures: Documentation of existing cybersecurity policies, incident response plans, and compliance with industry standards.
Technical Safeguards: Details about firewalls, intrusion detection systems, encryption practices, and other technical controls.
Employee Training: Information on cybersecurity training programs and awareness initiatives for staff members.
Incident History: Records of past cyber incidents, breaches, and the organization’s response to them.
Third-Party Risk Management: Evaluation of how the organization manages risks associated with vendors and partners.
While these questionnaires are thorough, they present several significant shortcomings:
Limitations of Questionnaire-Based Assessments
Snapshot in Time:
Static Nature: Questionnaires provide a one-time assessment of an organization’s cybersecurity posture, failing to capture ongoing changes and emerging threats.
Outdated Information: Cyber risks evolve rapidly, and a static questionnaire may quickly become obsolete, leading to inaccurate risk profiles.
Subjective Responses:
Self-Reporting Bias: Organizations may unintentionally or intentionally provide inaccurate information, either by overstating their security measures or underreporting vulnerabilities.
nconsistent Interpretation: Different respondents may interpret questions differently, leading to inconsistencies in the data collected.
Lack of Real-Time Insight:
No Continuous Monitoring: Questionnaires do not offer real-time visibility into an organization’s current security posture or immediate detection of new vulnerabilities.
Delayed Risk Assessment: The delay between completing a questionnaire and the insurance policy being issued can result in significant changes in the organization’s risk profile that are not reflected in the assessment.
Inadequate Risk Granularity:
Limited Depth: Questionnaires may not delve deeply enough into specific areas of cybersecurity, missing nuanced risk factors that could impact the overall risk assessment.
Generic Questions: Many questionnaires use generic questions that do not account for the unique aspects of different industries or organizational structures.
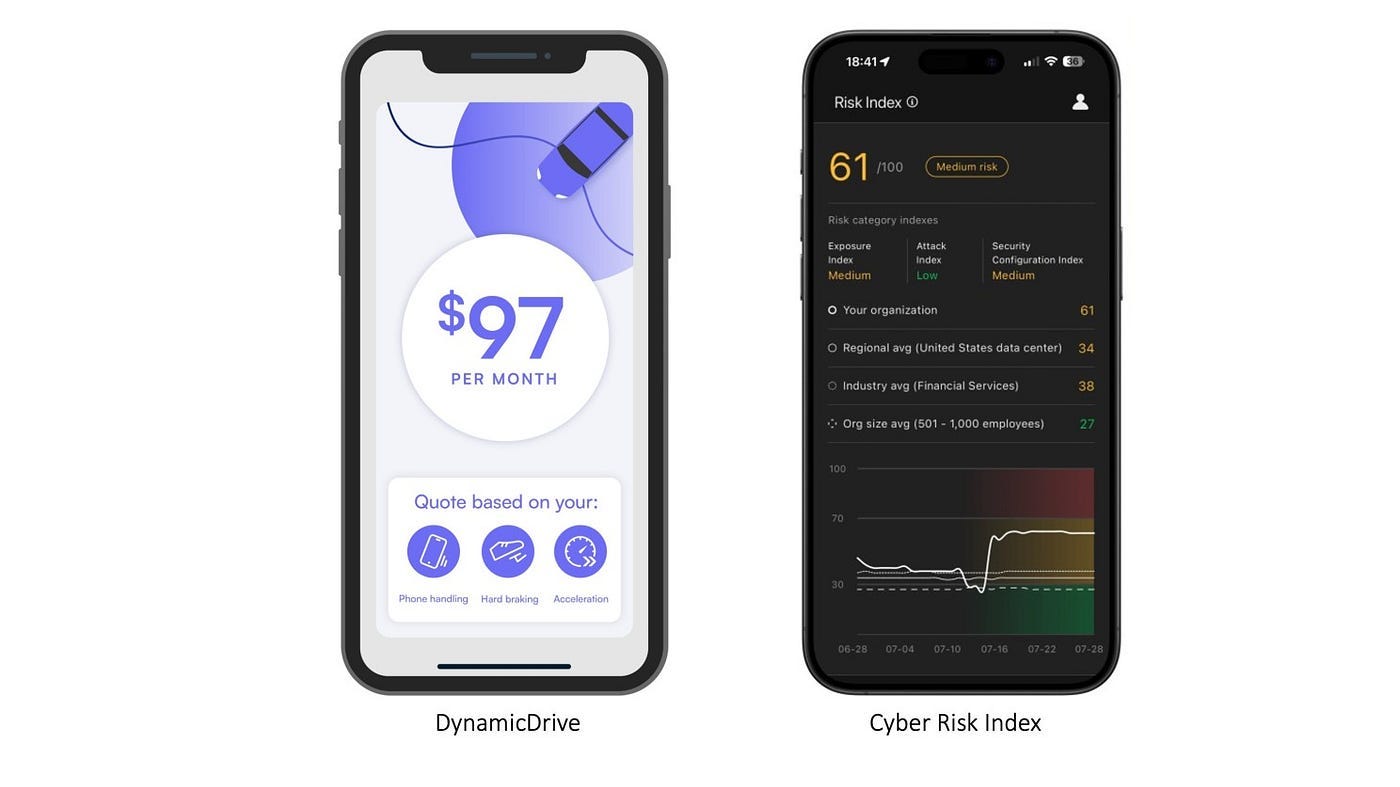
Learning from DynamicDrive: Embracing Continuous Risk Scoring in Cyber Insurance
One thing that the cyber insurance industry can learn from car insurance is the innovative DynamicDrive program. DynamicDrive leverages a smartphone app to monitor and assess driving behavior, enabling insurers to offer more tailored insurance rates and rewarding safe drivers with significant savings. This behavioral-based approach provides valuable insights into how the cyber insurance industry can adopt similar strategies to enhance risk assessment, policy customization, and overall effectiveness through the integration of a Continuous Cyber Risk Scoring System (CCRSS).
Understanding DynamicDrive: A Model of Behavioral-Based Insurance
DynamicDrive is a unique program designed to measure a customer’s driving behavior through a dedicated smartphone app. By tracking various aspects of driving — such as driving time of day, distracted driving due to phone handling, hard and extreme braking, and speeds at or above 80 mph — DynamicDrive calculates a driver performance score. This score directly influences the customer’s insurance premium, allowing safe drivers to save up to 10% on their auto insurance. Key features of DynamicDrive include:
Continuous Monitoring: The app continuously tracks driving behavior, providing real-time data on various driving events.
Tailored Insurance Rates: Insurance premiums are dynamically adjusted based on the driver’s performance score, incentivizing safe driving practices.
User Empowerment: Drivers receive immediate feedback on their driving habits, promoting awareness and encouraging safer behavior.
Flexibility and Customization: The program accommodates various driving conditions and behaviors, ensuring that insurance rates accurately reflect individual risk profiles.
Integrating CCRSS: Continuous Cyber Risk Scoring System
To parallel DynamicDrive’s success in auto insurance, the cyber insurance industry can implement a Continuous Cyber Risk Scoring System (CCRSS). CCRSS is an advanced framework designed to provide ongoing assessments of an organization’s cybersecurity posture. Unlike traditional risk assessment methods that rely on periodic evaluations and historical data, CCRSS leverages real-time data analytics, machine learning, and comprehensive threat intelligence to deliver up-to-the-minute risk scores. Key components of CCRSS include:
Real-Time Data Collection: Continuously gathers data from various sources, including network traffic, user behaviors, system logs, and external threat intelligence feeds.
Dynamic Risk Scoring: Utilizes machine learning algorithms to analyze collected data, generating a dynamic risk score that reflects the current cyber threat landscape and the organization’s vulnerabilities.
Proactive Risk Management: Identifies emerging threats and vulnerabilities, enabling organizations to take preventive measures before incidents occur.
Personalized Insights: Provides tailored recommendations based on specific risk factors, enhancing the effectiveness of cybersecurity strategies.
Benefits of Integrating CCRSS with DynamicDrive-Inspired Cyber Insurance Models
Incorporating CCRSS into the DynamicDrive analogy offers several significant advantages for the cyber insurance industry:
Improved Risk Accuracy: Continuous and real-time risk scoring leads to more accurate and up-to-date risk assessments, reducing reliance on outdated or incomplete data.
Proactive Threat Mitigation: CCRSS enables organizations to identify and address cyber threats before they escalate, enhancing overall cybersecurity resilience.
Enhanced Customer Engagement: Providing organizations with detailed insights and actionable feedback fosters greater engagement and satisfaction, strengthening the insurer-policyholder relationship.
Optimized Premium Structures: Dynamic premium adjustments based on real-time risk scores ensure that insurance costs are fair and reflective of actual risk, promoting cost efficiency for organizations.
Encouraged Cyber Best Practices: By rewarding organizations for maintaining strong cybersecurity practices, CCRSS incentivizes continuous improvement and adherence to best practices in cybersecurity.
Integrating the Continuous Cyber Risk Scoring System (CCRSS) based on a transparent methodology offers a robust framework for transforming the cyber insurance industry. By embracing continuous monitoring, dynamic risk scoring, and tailored insurance solutions, cyber insurers can move beyond traditional models to provide more accurate, responsive, and effective protection for organizations. This evolution not only enhances the value and relevance of cyber insurance products but also contributes to building a more secure and resilient digital ecosystem.