Artificial Intelligence (AI) vs Artificial Instinct (Ai), The Distinction Cybersecurity Can’t Afford to Ignore
We are living in the peak of the AI revolution, and today almost every technology claims to be powered by artificial intelligence. Cybersecurity has followed this pattern with remarkable enthusiasm. Everyone is looking for a magical solution, something that promises effortless protection without structural change. The industry chases AI enhanced analytics, AI optimized remediation, AI powered detection engines, autonomous SOC copilots, automated triage assistants, predictive behavioral scoring, and self healing infrastructures, believing that one more layer of intelligence will finally resolve the complexity that has challenged us for decades. AI has become the universal shortcut that many hope will neutralize threats, simplify operations, and close every gap at once. But cybersecurity is unlike any other digital discipline because our adversary is not an algorithm. We are not defending against a mathematical model or a predictable machine. We are defending against human beings, criminals, groups with intention, creativity, adaptability, and strategy, who use technology as an extension of their will. Criminal activity is driven by motives, improvisation, psychological pressure, and opportunity, all of which evolve faster than analytical engines can process. Intelligence helps us understand adversaries, but instinct is what allows us to keep pace with them. A defensive posture built only on intelligence operates permanently behind a human adversary who thrives on speed and unpredictability. This is why cybersecurity demands more than analytical capacity. It demands instinct.
Why Crime Requires Instinct, Not Only Intelligence
Cyber adversaries behave like highly fluid, decentralized networks. They move quickly, automate aggressively, and adapt instantly. They do not need to be perfect, they only need to be faster than our decision making. They continuously probe for weaknesses, exploit ambiguity, and react to defensive changes in real time. During more than a decade of collaboration with INTERPOL I learned the most important thing about cybersecurity, criminals operate without hierarchy, without bureaucracy, and without hesitation, while defenders often depend on structured processes, long decision chains, and analytical cycles that introduce delay. Intelligence is critical for mapping these adversaries, understanding their methods, and planning long term strategy, but it is instinct that provides the real time protection needed to survive their speed. Cybersecurity is a human adversarial discipline, and in human adversarial disciplines, instinct is not optional. It is foundational.
The Hot Stove Principle, Why Reflex Saves You Before Reason Does
This is where the hot stove analogy becomes essential. When you touch a burning surface, you do not analyze the temperature, calculate the probability of a burn, or convene a meeting to evaluate possible reactions, you pull your hand away instantly. Your nervous system reacts before your brain has time to think. That reflex does not replace intelligence, it complements it. Instinct protects you in the moment, while intelligence helps you understand the event and avoid repeating it. This combination is not accidental, it is the same mechanism that allowed human beings to evolve beyond other species. Reflexes kept our ancestors alive in the presence of immediate dangers, while intelligence allowed them to transform those experiences into memory, tools, cooperation, and long term planning. The coexistence of instinct and intelligence is what enabled humans to anticipate threats rather than merely react to them, and this biological duality remains the foundation of our survival. Cyber defense requires this same balance. To withstand modern digital threats, we must stop depending solely on analytical engines and begin building architectures capable of reflex, speed, and autonomous protection, not intelligence or instinct, but intelligence and instinct working together.
Why Cybersecurity Is Unique, We Fight Intent, Not Automation
What sets cybersecurity apart from other AI driven disciplines is the central role of human intent. Our adversaries are not autonomous processes behaving within predictable boundaries, they are people who think, improvise, deceive, and reshape their strategies the moment they detect resistance. Technology accelerates their actions, but it is intention that directs them. Human attackers search for the single misconfiguration that opens a path, the brief moment of distraction during an operational rush, the tiny hesitation in an overworked SOC, and they act with precision when they find it. This intentionality creates an asymmetry that pure intelligence cannot solve. Artificial intelligence allows us to understand the broader threat landscape, recognize emerging patterns, and anticipate possible risks, but artificial instinct is what enables a defensive environment to respond at the exact speed at which a human adversary moves. Intelligence helps you see the threat, instinct stops it before it unfolds.
The Limits of Intelligence in a Millisecond Threat Environment
For a long time, cybersecurity has invested almost exclusively in intelligence. We built massive data lakes, complex SIEM architectures, and SOCs designed to analyze and interpret millions of signals. That intelligence is essential for long term learning, for understanding attacker behavior, and for guiding strategic decision making. But intelligence carries an inherent limitation, it is fundamentally reactive. It requires something observable to happen before it can act. It needs signals to be generated, logs to be collected, anomalies to surface, and patterns to form before it can decide what the appropriate response should be. Every step in the analytical chain, from normalization to enrichment to correlation to interpretation, consumes time. Human adversaries have learned to weaponize this delay. Ransomware can encrypt critical systems in milliseconds, cloud workloads can appear and disappear in minutes, and AI enabled malware can mutate its behavior faster than any correlation engine can update its models. An intelligence only strategy is forced to think through threats that execute far faster than human cognition or machine reasoning can process. In these high speed moments, survival does not depend on understanding the threat, it depends on reacting to it. Instinct, not intelligence, is what protects you during the milliseconds that matter.
The Unpredictability of Criminal Action and Why Instinct Belongs to Risk Management
They do not need to be perfect, they only need to be faster than our decision making, and human adversaries have learned to weaponize this delay. This reality exposes one of the most uncomfortable truths in cybersecurity, we cannot predict when a criminal will act or when an attack will unfold. Criminal behavior is inherently opportunistic, driven by intent rather than schedule. A vulnerability can sit unnoticed for years, then become the focal point of an attack within minutes of discovery. A misconfiguration can be irrelevant one day and catastrophic the next. This unpredictability mirrors the real world, where risk does not announce itself before it strikes. When you drive a car, you cannot predict which driver will suddenly change lanes without warning, yet your instinct prepares you to react instantly. When you walk down a poorly lit street, you cannot predict which person might pose a threat, yet your instinct heightens your awareness and influences your behavior long before anything actually happens. Human survival has always depended on a combination of awareness and reflex, a form of instinctual risk management that protects us against dangers we cannot forecast precisely. Cybersecurity requires the same mindset. Cyber risk management becomes the framework that shapes artificial instinct, because it provides the context necessary for reflexive action. Without understanding asset value, business impact, exposure, and systemic importance, instinct cannot make the right decisions at the right time. Risk management supplies the map, instinct provides the reaction. Artificial instinct is not simply a fast version of detection, it is the operational expression of cyber risk management, allowing defensive systems to act with the same natural immediacy that humans use to protect themselves in unpredictable environments. It is the fusion of understanding and reflex that allows organizations to operate safely despite adversaries who strike whenever opportunity appears.
Why Organizations Struggle to Decide, and Why Cyber Risk Must Speak the Language of the Business
Inside most organizations, the people responsible for making decisions about cybersecurity are not security experts. Boards, executives, finance leaders, procurement teams, and business unit directors all influence the direction of cyber strategy, yet their perspective is shaped by operational priorities, financial models, and strategic outcomes rather than technical threats. They are not unwilling to invest in cybersecurity, they simply lack data they can understand, data that connects a security choice with a clear business consequence. When faced with budget allocation, project prioritization, vendor selection, or operational tradeoffs, decision makers rely on what they can quantify, what they can compare, and what they can justify. They understand financial exposure, operational continuity, customer trust, and regulatory compliance, but they often cannot interpret a list of vulnerabilities, an explosion of alerts, or a dashboard full of telemetry. This disconnect creates hesitation, not because they do not care, but because they cannot see the impact in terms that match their responsibilities. Cybersecurity becomes a technical argument made to a non technical audience, and this is where the CISO’s role becomes critical. The CISO must translate cyber risk into business risk, turning technical signals into language that boards and executives can act upon. It is not the CISO alone who should make decisions, cybersecurity is a business wide responsibility, but the CISO is the interpreter who enables the rest of the organization to choose correctly. Artificial instinct depends on this foundation, because instinctive systems must understand what the business values most in order to react in ways that protect continuity, performance, and growth. Without business aligned cyber risk insight, instinct has no compass. With it, decision making shifts from guessing to governing, allowing organizations to act with speed and clarity even when adversaries strike without warning.
The Architecture of the Human Brain and What It Teaches Us About Cyber Decision Making
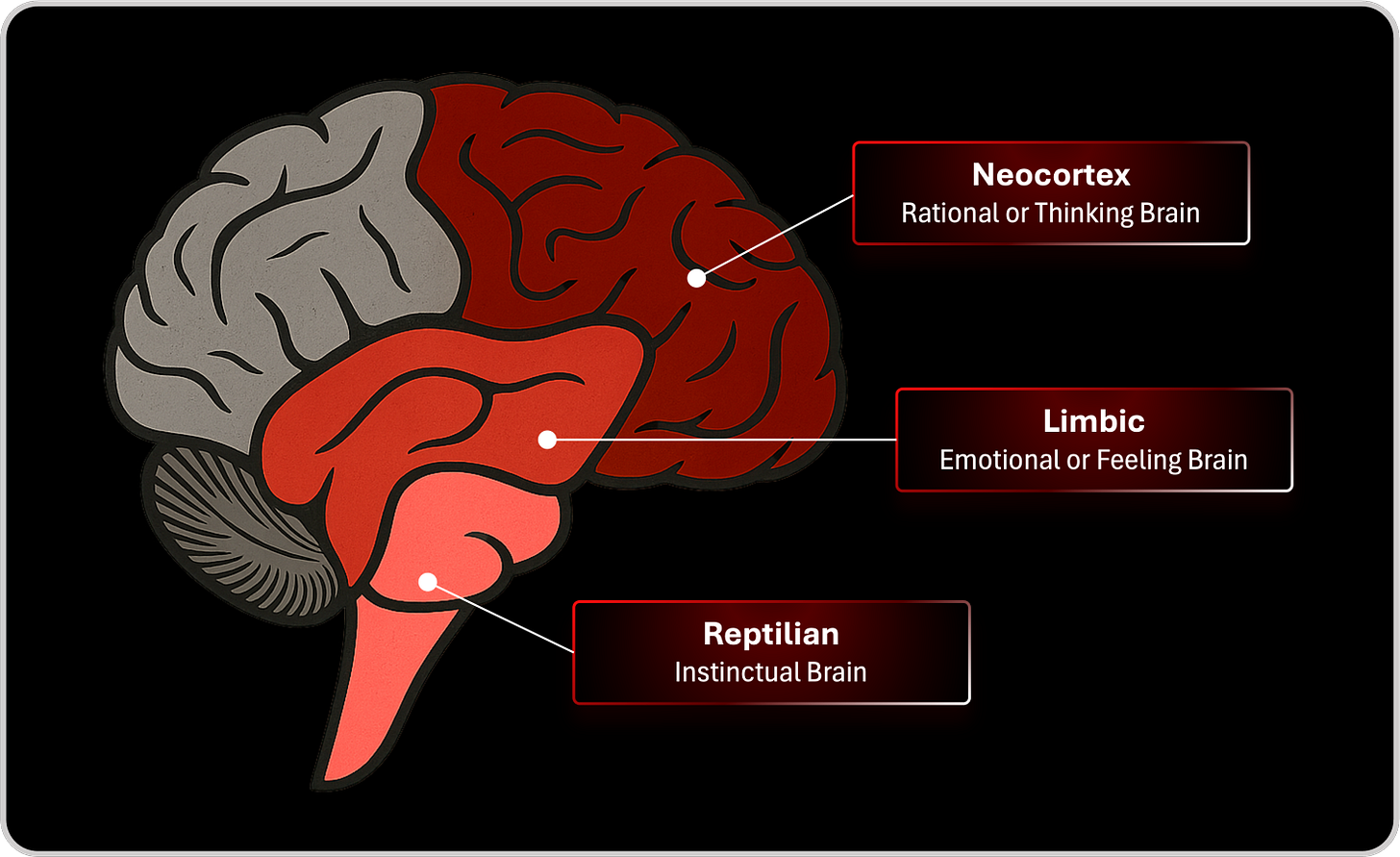
I have always been curious about how the human brain makes decisions, how we think, speak, and act in ways that feel coherent, and why sometimes those three layers fall completely out of sync. There are moments when we think one thing, say another, and act in a way that contradicts both, revealing that our internal architecture is far more layered and complex than we consciously perceive. The classical model that divides the brain into the neocortex, the limbic system, and the reptilian brain helps explain this tension. The neocortex is the rational and analytical layer, the part that evaluates information, reasons through complexity, and constructs logic. The limbic brain governs emotion, intuition, motivation, and social connection, shaping how we value things, what we fear, and what we prioritize. The reptilian brain is the instinctive core, the ancient survival system that reacts instantly to threat, long before the rational mind can analyze what is happening. These three layers coexist, influence one another, and sometimes conflict, but together they form the architecture that allowed humanity to evolve, innovate, and survive.
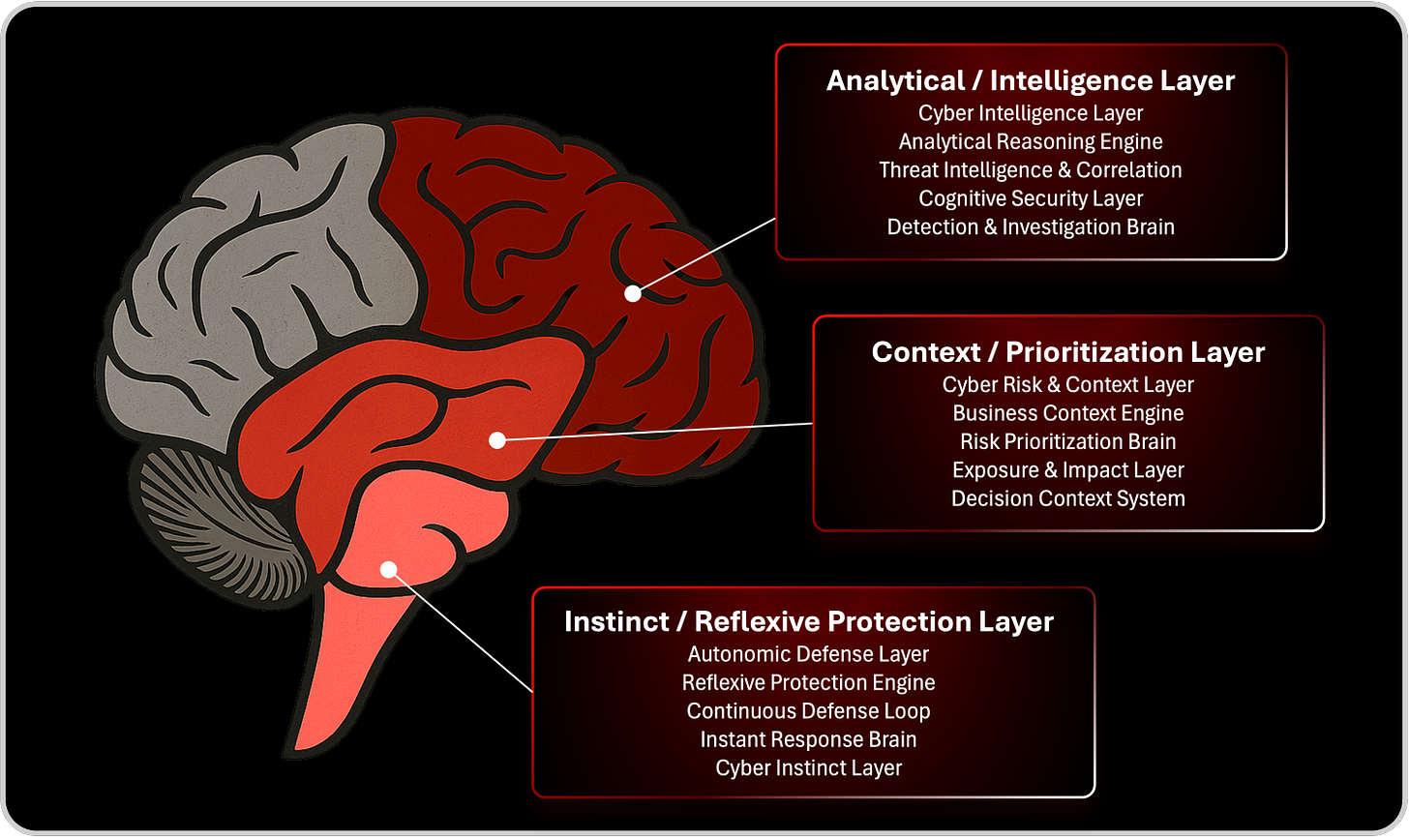
Cybersecurity mirrors this biological architecture more than we often admit. The neocortex is our analytical engine, the intelligence layer made of SIEMs, data lakes, AI models, and SOC investigation processes. It is powerful but slow, deliberate but vulnerable to time. The limbic layer is our organizational context, the emotional and prioritization layer, the place where business value, urgency, risk appetite, and stakeholder perception live. It determines what matters and how much it matters. And the reptilian brain represents instinct, the reflexive protective layer that bypasses analysis and acts immediately when danger emerges. Just as in human survival, cybersecurity cannot depend solely on the neocortex. Instinct and context cannot be ignored. When we think one thing, speak another, and act differently, it is often because these layers are not aligned. The same is true in modern defense. If intelligence signals one priority, business context demands another, and instinctive protection is missing altogether, organizations end up thinking one thing, reporting another, and reacting too late. Understanding this tri-layer structure is the key to building artificial instinct. We need systems that combine rational analysis, contextual awareness, and reflexive action into one coherent defensive architecture, just as the brain integrates thinking, feeling, and instinct to help us survive a world defined by uncertainty and threat.
How Risk Management Fits Into the Human Brain Model, and What It Means for Cyber Risk
If we extend the human brain analogy further, risk management becomes the missing link that integrates the three layers of the brain into coherent action. In everyday life, we constantly manage risk without realizing it. The rational neocortex evaluates information, the limbic system assigns value and emotional weight, and the reptilian brain decides how fast we must act to protect ourselves. When these three layers work together, we make effective decisions under uncertainty. When they do not, we experience the same cognitive dissonance we often see in organizations, we think one thing, feel something different, and act in ways that contradict both.
In the human brain, risk management is the invisible process that harmonizes thinking, emotion, and instinct. When you cross a busy street, your neocortex analyzes the distance and speed of the vehicles, your limbic system interprets the importance of getting to your destination safely, and your reptilian brain reacts instantly if a car turns unexpectedly. Risk management lives between these layers. It decides how much attention to allocate, how fast to move, how cautious to be, and when instinct must override thought. It is the mechanism that assigns priority, anticipates danger, and keeps you aligned with what matters most. Without this internal risk function, humans would either overreact to every stimulus or underreact to real threats.
Cyber risk management plays the exact same role in the cybersecurity analogy. The analytical neocortex of cybersecurity, made of SIEMs, telemetry pipelines, and threat intelligence, can describe the world but cannot assign meaning to it on its own. The limbic layer, represented by the business, stakeholders, strategy, and operational priorities, determines what truly matters to the organization. The reptilian layer, the artificial instinct we are building, reacts instantly when the first signals of danger appear. Cyber risk management sits at the center of these three layers, providing the structure that allows them to work in harmony. It quantifies what is important, translates abstract threats into business impact, and guides instinctive responses so that reflexive protection is not only fast but also meaningful. Cyber risk management ensures that artificial instinct does not react blindly, but reacts with purpose, aligned with business value, exposure, and continuity.
Just as in the human brain, cyber risk management is the interpreter and the integrator. It connects intelligence with instinct, emotion with logic, and business value with technical signals. When an organization has mature cyber risk management, its defensive instinct becomes sharper, its intelligence becomes more relevant, and its decisions become more coherent. Without it, organizations think one thing, report another, and act too late, exactly the same pattern we see when the human brain’s three layers fall out of alignment. Cyber risk management is the discipline that keeps everything synchronized, enabling artificial instinct to operate with the clarity and speed needed to confront adversaries who will always strike faster than we can think.
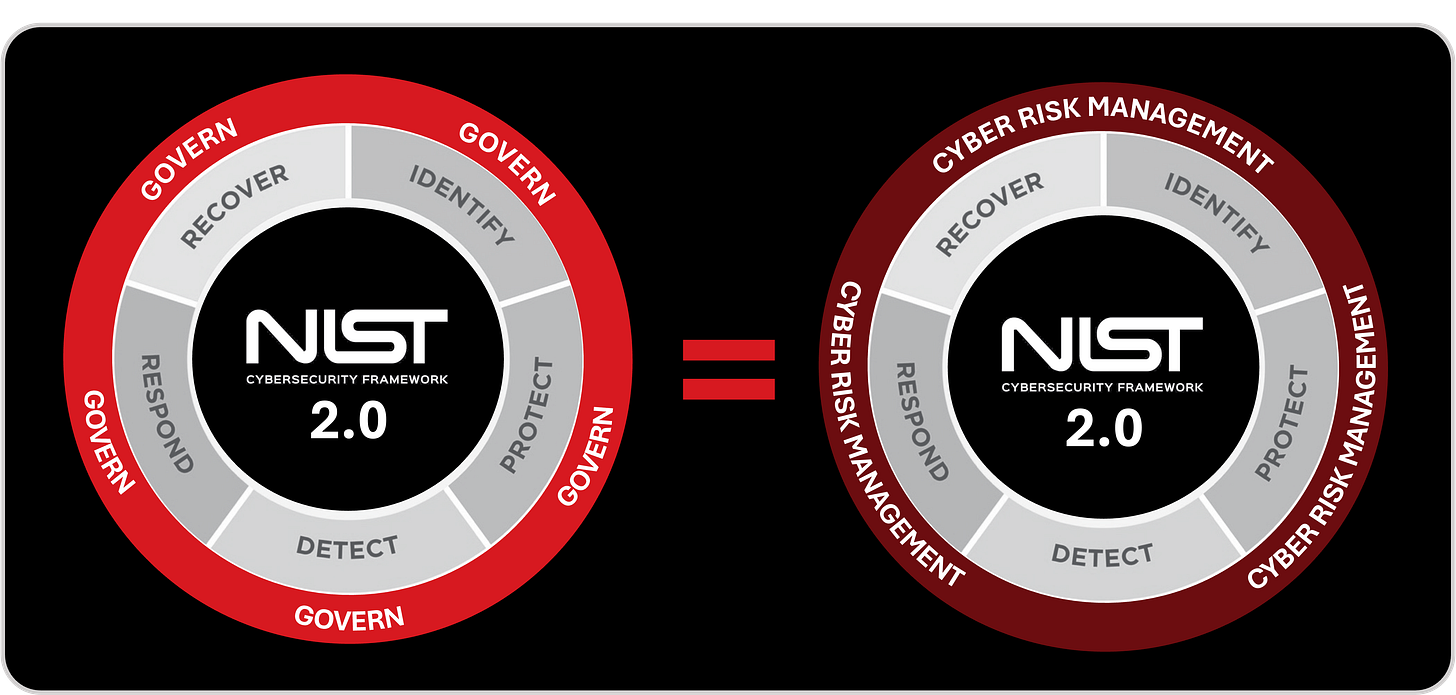
How Cybersecurity Frameworks Validate This Model, and Why NIST CSF 2.0 Makes the Brain Analogy Explicit
What is striking about the evolution of cybersecurity is that the industry’s most respected frameworks are beginning to mirror the same layered architecture found in the human brain. For years, cybersecurity frameworks offered structure but lacked an integrated model of how intelligence, instinct, and context should work together. NIST CSF 1.0 was a significant milestone, but its five core Functions (Identify, Protect, Detect, Respond, and Recover) behaved like parallel tracks rather than interconnected layers. There was no real mechanism to ensure that security actions were tied to business value, risk appetite, or strategic intent. As a result, many organizations ended up with a split-brain problem, the boardroom thinking one thing, the SOC doing another, and the business acting in ways that were disconnected from both. It was the same misalignment we see when the neocortex, limbic system, and reptilian brain are not working in harmony.
NIST CSF 2.0 changes this dynamic entirely. By introducing the GOVERN Function, NIST effectively acknowledges that cybersecurity cannot operate without a layer that assigns meaning, priority, and context to everything else. The Function’s language is explicit:
“The organization’s cybersecurity risk management strategy, expectations, and policy are established, communicated, and monitored.”
It also reinforces the principle of continuity by stating that
“Cybersecurity risks are expanding constantly, and managing those risks must be a continuous process.”
This is not just governance; it is the limbic system of the cybersecurity framework, the part that defines what matters most, how much it matters, and how those priorities are communicated across the entire organization.
Where CSF 1.0 treated the five Functions as operational domains, CSF 2.0 acknowledges that without governance, they lack directional coherence. GOVERN becomes the connective tissue that links intelligence (Identify, Detect) with instinctive defense (Protect, Respond, Recover). It defines how risk strategy is established, how expectations flow from leadership to operations, and how decisions are continuously monitored, reassessed, and aligned with business objectives. In other words, it formalizes the missing middle layer, the business-aware, context-driven, risk-informed layer that allows instinct and intelligence to function productively rather than contradict one another.
This shift reflects the reality I discussed in my previous article, Cyber Risk Is a Moving Target. The conditions we are trying to manage evolve too quickly for periodic assessments or static governance structures. Threats move, assets change, exposure fluctuates, and adversaries exploit every lag in decision-making. CSF 2.0’s GOVERN Function acknowledges this by framing cybersecurity governance as a continuous, iterative, real-time conversation. It moves governance closer to the limbic system of the brain, dynamic, adaptive, constantly adjusting what the rest of the system should pay attention to and how urgently it should act.
Frameworks evolve when practices evolve. And as organizations confront faster adversaries, expanding attack surfaces, and complex digital ecosystems, the need for a brain-like architecture becomes undeniable. Intelligence alone cannot keep up. Instinct alone cannot make informed decisions. Context alone cannot act. NIST CSF 2.0 validates this truth by giving cyber risk management not just a place in the model, but the central role that guides and integrates everything else. It acknowledges that modern cybersecurity must function like the human brain: continuously learning, continuously adapting, and continuously aligning instinct with intelligence through the lens of risk.
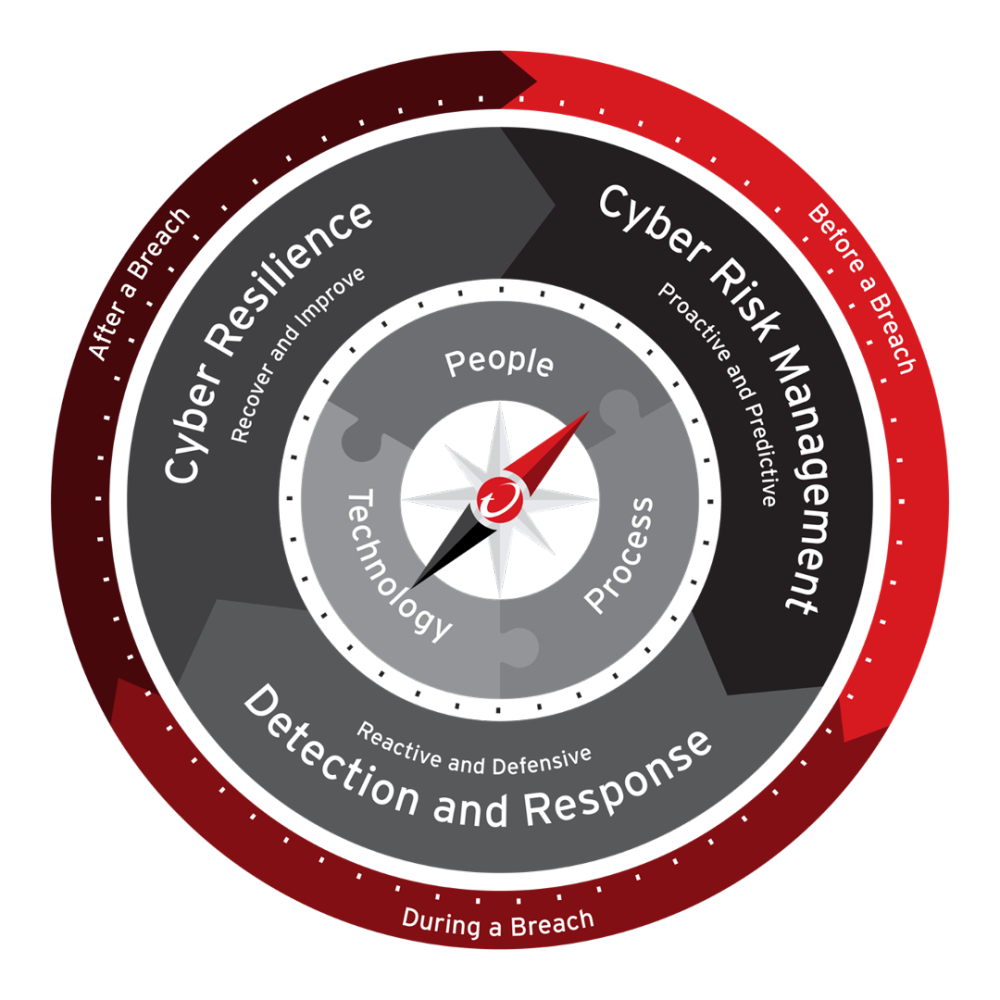
How the Cybersecurity Compass Aligns With This Model
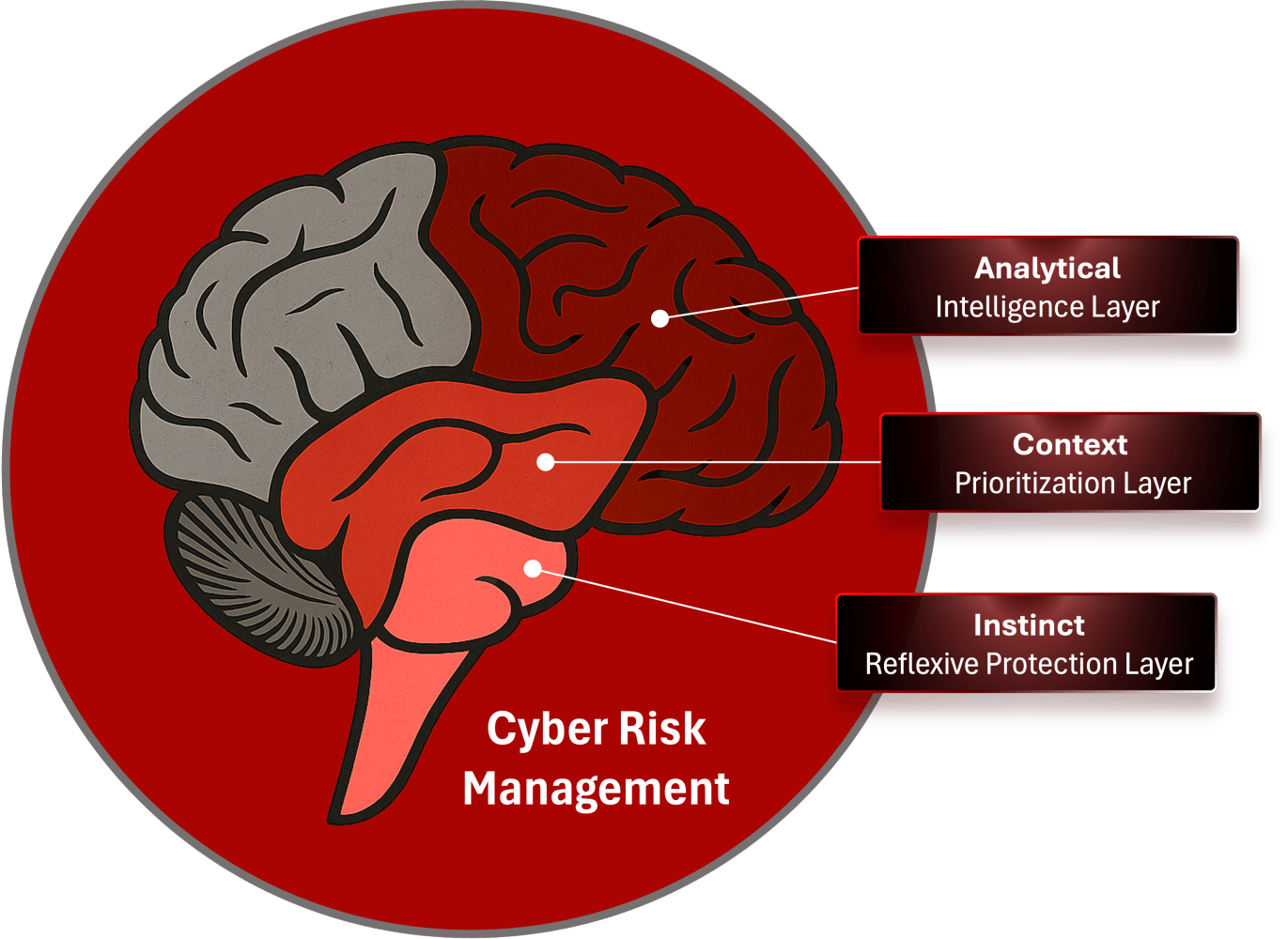
The Cybersecurity Compass I developed follows the same logic found in both the human brain and modern cybersecurity frameworks. It organizes cybersecurity into three concentric layers, Cyber Risk Management, Detection and Response, and Cyber Resilience, each operating within a temporal cycle of before, during, and after a breach. What makes the Compass especially aligned with the brain model is that it mirrors the same hierarchical structure of intelligence, context, and instinct that governs human decision-making.
The first section of the Compass, Cyber Risk Management, represents the proactive and predictive layer, the place where organizations understand exposure, quantify risk, evaluate business impact, and prioritize action. This is the Limbic Brain of cybersecurity, the system that interprets what matters, how much it matters, and why. It connects business priorities with security action, transforming abstract risk into concrete guidance. This is precisely what NIST CSF 2.0’s GOVERN Function formalizes, a continuous, adaptive framework where risk strategy, expectations, and policies are established, communicated, and monitored. In both the Compass and the brain, context is the system that decides where intelligence should focus and where instinct should trigger.
The middle section of the Compass, Detection and Response, aligns with the Neocortex, the analytical and reasoning system. This is the domain of intelligence-driven defense, where telemetry, signals, analytics, and investigation converge. It is reactive out of necessity, because analysis requires evidence and signals must first exist before the system can think about them. This is where SIEMs, EDR, XDR, and threat intelligence operate. It mirrors the rational functions of the neocortex, interpreting patterns, understanding relationships, and guiding response but always subject to the latency required for cognition.
The final section of the Compass, Cyber Resilience, connects to the Reptilian Brain, the instinctual survival mechanism. Cyber resilience includes continuity, rapid recovery, operational adaptability, and the ability to maintain function under stress. These are instinctive capabilities in the biological sense, enabling the system to survive immediate danger even before deeper analysis occurs. Just as the reptilian brain preserves life under threat, resilience preserves business continuity during and after a breach. It is the autonomic layer that stabilizes the system while intelligence and governance recalibrate.
What unifies all three layers of the Compass is the directional navigation at its center, People, Process, and Technology, the same triad required to align instinct, intelligence, and risk context. The compass needle points toward constant alignment, reinforcing that security is not a technical domain but a systemic one. It demands coordination between human behavior, organizational procedures, and technological capabilities, just as the human brain requires coordination between instinct, emotion, and rational thought.
The Compass also emphasizes time, before, during, and after a breach, which perfectly aligns with the continuous, adaptive nature of risk management. Just as the brain learns, reacts, adapts, and evolves through cycles, cybersecurity must continuously refine its posture through the lived experience of threats. NIST CSF 2.0 underscores this with its insistence that cyber risk management must be a continuous process rather than a static one. The Compass reflects this by embedding dynamism into every layer.
By combining the instincts of resilience, the intelligence of detection, and the contextual awareness of risk management, the Cybersecurity Compass becomes a visual representation of the very architecture this article describes: an integrated cyber brain capable of reflex, reasoning, and alignment with business purpose. It operationalizes what frameworks now endorse, that cybersecurity must behave like a living, adaptive system, where instinct and intelligence work under the guidance of risk-informed governance.
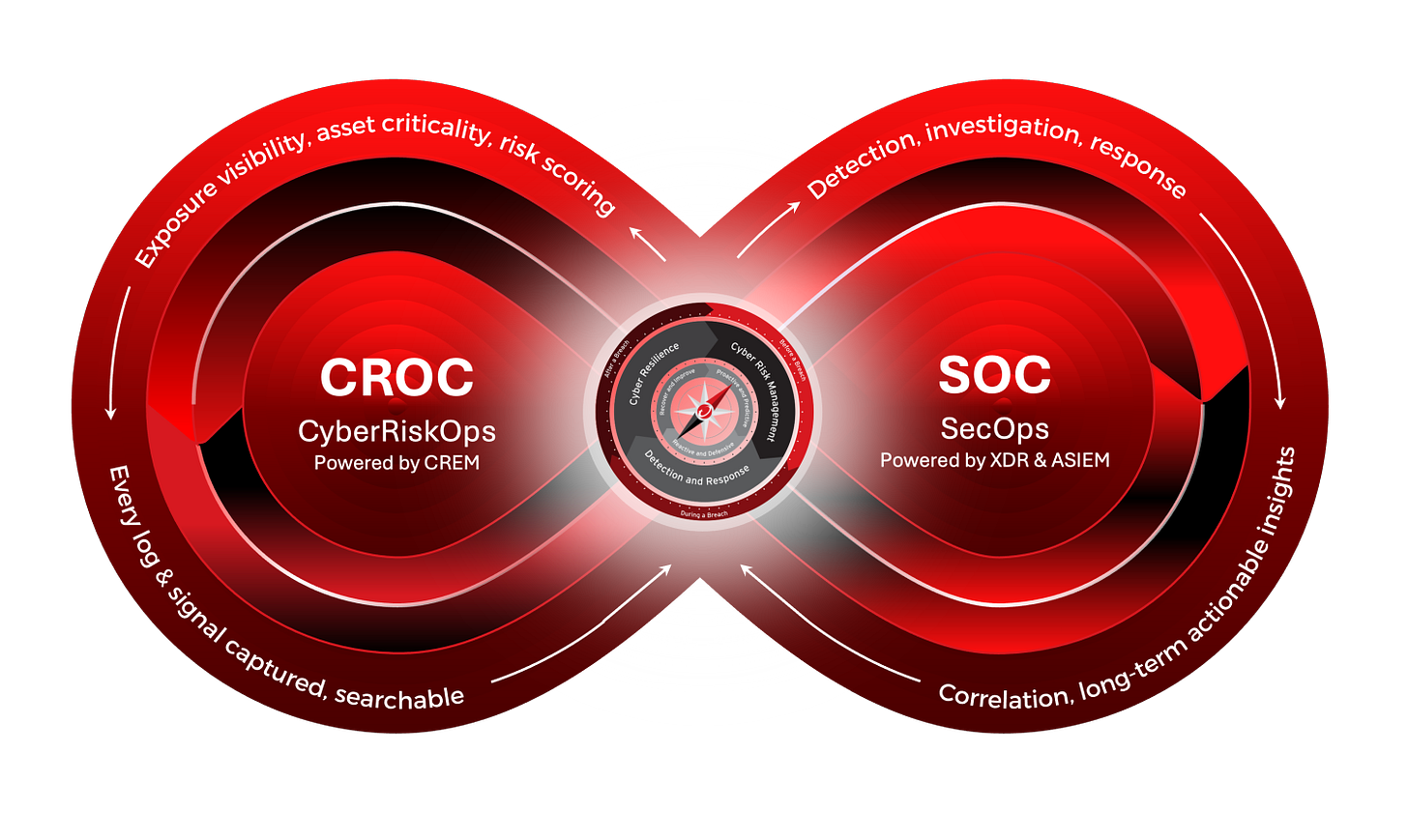
How the Continuous Defense Loop Unifies Instinct, Intelligence, and Risk
The Continuous Defense Loop is the operational expression of everything described in this article, the fusion of instinct, intelligence, and risk that turns cybersecurity from a collection of isolated activities into a living, adaptive system. In the same way the human brain constantly circulates information between instinctive reflexes, emotional context, and rational thought, a modern cyber organization must function in a circular and self correcting rhythm. The Continuous Defense Loop ensures that every signal, every risk insight, and every business priority moves through the system continuously, shaping both defensive instinct and analytical intelligence in real time.
At its center, the Loop connects CROC, or CyberRiskOps powered by CREM, and SOC, or SecOps powered by XDR and ASIEM, into a single coordinated organism. The SOC represents the analytical neocortex, the realm of detection, investigation, correlation, and long term understanding. This is where threats are interpreted and intelligence is refined. The CROC represents the limbic system, the business oriented risk engine that assigns meaning and criticality to every signal, mapping exposure, asset value, and operational impact. It provides the answer to the essential question in cybersecurity, which is not whether an event is malicious, but how much it matters. Complementing both layers is the instinctive core of defense, the reflexive and autonomic response mechanisms that act during the milliseconds when cognition is too slow and when survival depends on immediate action.
The Continuous Defense Loop connects these layers so that none of them operate in isolation. Signals entering the SOC are continuously enriched with risk context from the CROC, transforming raw telemetry into business aware intelligence. At the same time, risk insights generated in the CROC are shaped by what the SOC observes across the attack chain, closing the feedback loop between risk and intelligence. Every log, every alert, and every emerging anomaly travels through this cycle, becoming either an immediate protective action, a refined risk insight, or a deeper analytical understanding of adversary behavior.
This architecture aligns perfectly with the evolution represented by NIST CSF 2.0. The GOVERN Function provides strategic direction and policy clarity, acting as the contextual center that ensures the entire defensive organism moves according to business priorities and risk appetite. The Identify, Protect, Detect, Respond, and Recover Functions become the operational zones inside the Loop, informed continuously by one another rather than operating in parallel or in isolation. What emerges is a recursive system of learning
The Future of Cybersecurity Belongs to Systems that Think and React Like a Brain
Cybersecurity has become a race shaped not only by technology but by human intent. Modern adversaries think creatively, adapt quickly, and exploit the smallest delay between what we observe and how we act. This human dimension is why relying on intelligence alone is no longer enough. Defense must combine analytical understanding, business context, and instinctive protection, much like the human brain relies on cognition, emotion, and reflex to survive uncertainty.
Artificial intelligence provides the thinking layer, cyber risk management provides the meaning and priorities, and artificial instinct provides the immediate protection needed when threats move faster than analysis. When these layers work together, organizations gain the ability to anticipate, prioritize, and respond with coherence and speed. When they operate in isolation, defenders fall behind human adversaries who face no internal friction and no hesitation.
Cybersecurity is no longer about accumulating more tools or more data, it is about creating an architecture that thinks and reacts as a unified system. The future will belong to organizations that understand the human nature of cybercrime and build defenses that are adaptive, contextual, and continuous. In that future, we will not only defend against attacks, we will learn, evolve, and respond with the same fluidity and resilience that define every living system.
Castro, J. (2024). From Reactive to Proactive: The Critical Need for a Cyber Risk Operations Center (CROC). ResearchGate. https://www.researchgate.net/publication/388194441 DOI:10.13140/RG.2.2.27408.93445/1
Castro, J. (2025). Cyber RiskOps: Bridging Strategy and Operations in Cybersecurity. ResearchGate. https://www.researchgate.net/publication/388194428 DOI:10.13140/RG.2.2.36216.97282/1
Castro, J. (2024). Integrating Cyber Risk Management to your Cybersecurity Strategy: Operationalizing with SOC & CROC. ResearchGate. https://www.researchgate.net/publication/388493453 DOI:10.13140/RG.2.2.30164.72328/1
Castro, J. (2024). Integrating NIST CSF 2.0 with the SOC-CROC Framework: A Comprehensive Approach to Cyber Risk Management. ResearchGate. https://www.researchgate.net/publication/388493049 DOI:10.13140/RG.2.2.13387.50720/1
Castro, J. (2025). Cyber Risk Operations Center (CROC) Process and Operational Guide. ResearchGate. https://www.researchgate.net/publication/389350613 DOI:10.13140/RG.2.2.19164.09600
Castro, J. (2025). What Is Strategy in Cybersecurity? Rethinking the Way We Lead, Protect and Adapt. ResearchGate. https://www.researchgate.net/publication/393674625 DOI:10.13140/RG.2.2.16703.42409
Castro, J. (2024). What Cybersecurity Can Learn from Glucose Management in Diabetes. ResearchGate. https://www.researchgate.net/publication/388528830 DOI:10.13140/RG.2.2.14003.54568/1
Castro, J. (2025). Introducing the CROC Levels: Operationalizing Cyber Risk Management. ResearchGate. https://www.researchgate.net/publication/393333383 DOI:10.13140/RG.2.2.31393.31841
Castro, J. (2025). How a Cyber Risk Index (CRI) Can Be Used as a KPI in Your Cybersecurity Strategy. ResearchGate. https://www.researchgate.net/publication/389001302 DOI:10.13140/RG.2.2.32915.18728
Castro, J. (2025). Cyber Risk Operational Model (CROM): From Static Risk Mapping to Proactive Cyber Risk Operations. ResearchGate. https://www.researchgate.net/publication/390490235 DOI:10.13140/RG.2.2.15956.92801
Castro, J. (2025). Cyber Risk Should Not Be Treated — It Should Be Operationalized. ResearchGate. https://www.researchgate.net/publication/389991463 DOI:10.13140/RG.2.2.12429.45289
Castro, J. (2024). Safely Sailing the Digital Ocean with the Cybersecurity Compass. ResearchGate. https://www.researchgate.net/publication/387410177 DOI:10.13140/RG.2.2.20696.00003
Castro, J. (2025). Threat Hunters vs. Cyber Risk Hunters: Two Sides of Modern Cybersecurity. ResearchGate. https://www.researchgate.net/publication/395721548 DOI:10.13140/RG.2.2.20329.35688
Castro, J. (2025). Umbrellas, Storms, and Cyber Risk: Why Threat Management Is Not Risk Management. ResearchGate. https://www.researchgate.net/publication/396695719 DOI:10.13140/RG.2.2.24818.98240
Castro, J. (2024). Strategic Cyber Defense: Applying Sun Tzu’s Art of War Lessons to the Cybersecurity Compass. ResearchGate. https://www.researchgate.net/publication/387410535 DOI:10.13140/RG.2.2.25085.68327
Castro, J. (2024). A Common Language for Cybersecurity. ResearchGate. https://www.researchgate.net/publication/387505866 DOI:10.13140/RG.2.2.31894.05448
Castro, J. (2024). Safely Sailing the Digital Ocean with the Cybersecurity Compass. ResearchGate. https://www.researchgate.net/publication/388729549 DOI:10.13140/RG.2.2.20696.00003
Castro, J. (2025). Logs Telemetry and the Golden Ratio: Why the Data Ownership Ratio Will Redefine Cybersecurity Architecture and Cyber Risk Management. ResearchGate. https://www.researchgate.net/publication/397677257 DOI:10.13140/RG.2.2.21403.53288
Castro, J. (2025). What Is Governance in Cybersecurity?. ResearchGate. https://www.researchgate.net/publication/393065290 DOI:10.13140/RG.2.2.30988.63360
Castro, J. (2025). Context is Everything in Cybersecurity: Why Signals Without Meaning Are Just Noise. ResearchGate. https://www.researchgate.net/publication/392408653 DOI:10.13140/RG.2.2.15442.26561
Castro, J. (2025). Rethinking the Pyramid of Pain in 2025: Precision, Pressure, and the Power of Context. ResearchGate. https://www.researchgate.net/publication/394107570 DOI:10.13140/RG.2.2.24252.35201